UPDATE 02/07/22: Video of the talk added
The guys from BSides Dublin asked me to talk about the Russian offensive in Ukraine. I use the term offensive because there has been a state of war between Russia and Ukraine since 2014 in my opinion. I had a radically different talk planned where I would talk about other things entirely, but I'll save them for another time since they are pretty rad and shouldn't be in the dark.
PDF of slides and notes for BSides Dublin
PDF of slides and notes for the ICSPC Discord
I would also note that while BSides asked me to talk about all of this, the initial inkling for me was planted several days into the war when a friend of mine asked;
So far, I'm hearing lots of concern about the possibility of massive cyber attacks, but very little evidence of any such thing
Don Edwards; #world-events; Irish Cyber Security and Privacy Discord
Finally, apologies for how long this took to write and post... Normally this is out within hours of me giving the talk, and written before the slides are, but I got COVID at BSides and oh boy... It put me down for the count and it took me a long time to get back on my feet... I'm still not 100% over a month later...
War Is Boring
The easiest way for me to explain why Cyber War would be to look at why War is boring on its own, which David Axe, like him or not, describes as;
… that much of warfare is about politics, paperwork and logistics more than it is about actual combat.
David Axe; Author Bio; Small Wars Journal
The way we think about Cyber in a lot of ways is the same. Though rather than politics, paperwork and logistics, Cyber Warfare is more about Politics, Legalities and Perceptions, though logistics and paperwork still matter. You still ultimately need to get implants etc into place, which is a logistical problem and if you joined any military and expected not to be doing paperwork... I have some very bad news for your career prospects.
Now I do want to note, because I was very lucky to have someone in the audience who had studied under Dr Thomas Rid, is that Cyber War as a concept is dead and gone. War cannot and does not take place in a single domain without spillover to other domains. Cyber War isn't real, but Cyber Warfare is very real and it is what people are thinking about when they are thinking about operations against computers, networks or systems.
Politics
Cyber war is an extension of policy by actions taken in cyber space by state or nonstate actors that either constitute a serious threat to a nation’s security or are conducted in response to a perceived threat against a nation’s security.
Paulo Shakarian, Jana Shakarian and Andrew Ruef; Introduction to Cyber-Warfare - A Multidisciplinary Approach; pp 2
Put simply, using cyber warfare to achieve one's goals is an option that exists because you can't get it through other policy actions such as active diplomacy, sanctions or other compelling behaviours. This is a very Clausewitzian view of the world where War itself is something that you do as a state when you run out of political runway, you turn to your next tool in the toolbox, which is war. The use of Information Warfare and Cyber Network Operations (CNO) opens up an area before war, where Grey Area Operations can take place.
The Bronze Night
The Bronze Nights are a fascinating look at the politics that underly a lot of Information and Cyber Operations. The story starts in September 1944 when the Wehrmacht had retreated from Tallinn and the citizens of Estonia, knowing what Soviet Occupation was like, proclaimed their independence, only to have the Red Army come in and reoccupy Tallinn. At the site the Bronze Soldier of Tallinn would eventually stand, the Soviet Union buried two soldiers, and post-war burying more and renaming the area from Tõnismägi to Liberators' Square.
To many Estonians, this was seen as a symbol of Soviet oppression and the statue that was there, was originally a smaller statue, but it was blown up by teenagers during the Estonian War of Independence. The Soviets rebuilt the square as a park and placed the Bronze Soldier of Tallinn there, where it remained until 2007 when a plan was unveiled to move the statue to the Defence Forces Cemetery of Tallinn, which was thought to be a less decisive place to have a memorial to the war dead.
Russians though, they saw it as a symbol of victory over the Nazis and more importantly, this was an idea that could be weaponized by the Kremlin, and it was. Russia feels it's important to protect Russian speakers outside of Russia and sees repression of them as a form of cultural genocide, something Putin has repeatedly stirred up over the years, from Ukraine now, to Estonia in 2007 to Chechnya in 1999.
When Estonia finally planned to move the statute, Russia began a coordinated campaign of DDoS incidents, website defacements spamming comments on news websites with what is most likely the first truly modern Fake News campaign. While the DDoS' and defacements were not that successful beyond the initial shock of sites being down or defaced, the spamming was incredibly effective at mobilizing Russian speakers against the removal of the statue. Those that were mobilized, or better radicalized, then began to meet with diplomats about what to do about the removal of the statue, including cash payments to prevent the removal.
They began protesting the site, camping in cars etc until eventually, Estonia began to dismantle the statue in preparation to move it. This is when a Kremlin-backed stooge assaulted a police officer and the police responded as police do, with massive retaliation, resulting in two days of rioting. Russia was ready for exactly this, immediately deploying stories throughout Russian media, including Fake News with doctored images of what was going on, which mobilized more people to protest.
Eventually, the statue was moved to the Defence Forces Cemetery of Tallinn, where it stands today, vandalized again in the wake of the Russian offensive in Ukraine. These events became the first real deployment of a set of tactics known as Hybrid Warfare.
Peeter Kaasik of the Estonian Ministry of Foreign Affairs, compiled an amazing report on the background to the Bronze Soldier of Tallinn, for the Estonian Foundation for the Investigation of Crimes Against Humanity, which is well worth a read if you are interested in it. And Ivo Juurvee and Anna-Mariita Mattiisen of The International Centre for Defence and Security wrote an amazing retrospective of the Bronze Nights titled The Bronze Soldier Crisis of 2007: Revisiting an Early Case of Hybrid Conflict, which is essential reading to understand the events.
Hybrid Warfare
Hybrid Warfare is a difficult idea to grasp. The idea was coined by Frank G. Hoffman, a Research Fellow at the US Marine Corps Center for Emerging Threats and Opportunities, who defined Hybrid Warfare as;
Conflicts are increasingly characterized by a hybrid blend of traditional and irregular tactics, decentralized planning and execution and non-state actors, the strategy states using both simple and sophisticated technologies in innovative ways
Frank G. Hoffman; Conflict in the 21st Centaury: The Rise of Hybrid Wars; pp 7
The EU and NATO have a joint project, the Hybrid CoE, where they describe Hybrid Threats as;
Coordinated and synchronized action that deliberately targets democratic states’ and institutions’ systemic vulnerabilities through a wide range of means.
Activities that exploit the thresholds of detection and attribution, as well as the different interfaces (war-peace, internal-external security, local-state, and national-international).
Activities aimed at influencing different forms of decision-making at the local (regional), state, or institutional level, and designed to further and/or fulfil the agent’s strategic goals while undermining and/or hurting the target.
Hybrid CoE; Hybrid threats as a concept
Personally, both of these are terrible ways to define anything... So I think about Hybrid Warfare as strategically targeted Political Warfare against Democracies and Democratic Intuitions, that blends conventional and irregular warfare with cyber and influence operations.
So for example, you could look at the Conventional Warfare as the Russian backed uprisings in the Donbas and Luhansk in 2014. The Irregular Warfare of the "Little Green Men" in Crimea in 2014. Cyber Operations such as the DNC Hacks in 2015 and 2016, and then the dumping of select data from the DNC hack as part of Influence Operations in 2016.
These are all targeting Democracies, but Hybrid Warfare has been used against Democratic Intuitions, such as the World Anti Doping Agency (WADA) after Russia was banned from participating in the 2016 Olympics for their state-sponsored doping campaign, which led Russia to carry out a Cyber Operation on WADA and dump data that made multiple top athletes look like they were also doping, which is an Influence Operation. They did the same to the Organization for the Prohibition of Chemical Weapons (OPCW), where after the Skripal Poisoning, Russia used Influence Operations to say that the poisoners were just tourists, and attempted to hack into the OPCW to see what they had, an attempt that was foiled by Dutch intelligence.
The idea here is what is known as Grey Area Operations. They are operations that utilize all available techniques, up to the threshold of war, without crossing it. These are what are sometimes called Shadow Wars, where you may not even be able to respond in a conventional sense to the conflict, but you may need to respond to prevent destabilization. For example, Russia backs Syria in the Syrian Civil War, which will make the conflict go on for longer, the longer conflict means more refugees to Europe, which fuels far-right politics, which destabilizes Europe.
The longer war also means that there is a conflict between religious groups such as Iranian backed Hezbollah, a Shia group, which is pitted against Saudi backed groups such as Jaysh al-Islam, who are Sunni. Both Iran and Saudi Arabia are using the conflict as one of several proxy wars they are using to fight each other in this Grey Area. Sticking with Syria, even though we are in theory moving away from oil and gas globally, there are still significant hydrocarbon deposits in the Middle East and attempts to recover these deposits are hampered by the various conflicts in the region, driving up energy prices.
It should though be noted, that just because I have listed a whole pile of bad things that are contributing to a horrendous humanitarian situation in the Middle East and unnecessary wars, that is only one side of the coin, the threat. As the former C at SIS, Sir Alex Younger notes, there is both a threat and an opportunity and spies love the ambiguity that Grey Area Operations give them access to;
"There was a difference, call it prosaic, between peace and war; there was a difference between domestic and international; there was a difference between cyber and real, largely because cyber didn’t exist,” he explains. “That’s all blurred now and we’ve got hybrid and ambiguity and conflict across the spectrum.” Ambiguity is a fascinating concept for a chief spy, he admits with an edgy laugh, because it is both a threat and an opportunity: “We are charged with dispelling ambiguity, but we also use ambiguity.”
Roula Khalaf and Sir Alex Younger; ‘The Russians did not create the things that divide us — we did that’
And this opportunity is best exemplified by US Intelligence essentially being dumped, fully analyzed and ready for dissemination in the run up to H Hour in Ukraine. Just skimming my notes for the month of February, the US began releasing troop estimates on the border with Ukraine, dropping information about some of those units, such as the mercenary group known as Wagner was deploying to Ukraine, finally dropping what we all knew to be true, that Russia was funding Neo Nazi and 'Neo Fascist' groups around the world, and that Russian commanders were given the order to invade Ukraine. All of this was done with the aim of preventing or more likely, postponing the invasion, something that was likely effective, but we will have to wait a long time to learn this for sure.
Legalities
I could spend forever on the legal issues around just the two words "Cyber Attack", but I will spare you the details as that is my secret bore you death weapon. Ultimately, in legal terms, the relevant branch of law for all wars is International Law. In International Law, there is a branch of law that depending on your perspective, you know as the Rules of War or the Law of Armed Conflict (LOAC), and the other term is International Humanitarian Law (IHL).
Now a lot of people think that having Laws of War is dumb because we just shouldn't have war... And like... I would also like to live in the Land of Milk and Honey but... I know that realistically, war is something that will happen and like many things in life, you buy insurance against the great evils we have seen in the past. And if any recent war Russia has been involved in is anything to go by, if you don't think we should have IHL, what I am hearing is that you are ok with absolutely grotesque War Crimes such as we have seen in Aleppo and Mariupol.
To understand simply why CNO opens the door to Grey Area Operations, you need to understand what it means to cross the Threshold of Armed Conflict. There is a whole process in the UN Charter about how states can legally enter a state of war, as generally speaking there is a prohibition on the use of threats of war or "Uses of Force";
Article 2
4. All Members shall refrain in their international relations from the threat or use of force against the territorial integrity or political independence of any state, or in any other manner inconsistent with the Purposes of the United Nations.
The UN Charter; Chapter I: Purposes and Principals
Now Uses of Force are a complicated and vigorously debated topic, so in short, Using Force is to use military power. Something that damages or destroys property or injures or kills people. I won't get into Threats of Force though. So to go to war, if there is a general prohibition on war, you have very limited options. Firstly your aim must be consistent with the principles of the UN, so when Putin says that he is going to kill Nazis in Ukraine, what he is saying is not just an inspiring message to the homefront, but also that Putin is telling the world, in carefully crafted legalese is that they are going in to prevent humanitarian tragedies and/or Human Rights Violations. Now, this is preposterous which is why Russia didn't take the first path to war;
Article 41
The Security Council may decide what measures not involving the use of armed force are to be employed to give effect to its decisions, and it may call upon the Members of the United Nations to apply such measures. These may include complete or partial interruption of economic relations and of rail, sea, air, postal, telegraphic, radio, and other means of communication, and the severance of diplomatic relations.
Article 42
Should the Security Council consider that measures provided for in Article 41 would be inadequate or have proved to be inadequate, it may take such action by air, sea, or land forces as may be necessary to maintain or restore international peace and security. Such action may include demonstrations, blockade, and other operations by air, sea, or land forces of Members of the United Nations.
The UN Charter; Chapter 7: Action with Respect to Threats to the Peace, Breaches of the Peace, And Acts of Aggression
The other option available is the Article 51 minefield;
Article 51
Nothing in the present Charter shall impair the inherent right of individual or collective self-defence if an armed attack occurs against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defence shall be immediately reported to the Security Council and shall not in any way affect the authority and responsibility of the Security Council under the present Charter to take at any time such action as it deems necessary in order to maintain or restore international peace and security.
The UN Charter; Chapter 7: Action with Respect to Threats to the Peace, Breaches of the Peace, And Acts of Aggression
Long story short, it states that you can go to war if you are attacked or that you can be called into war because you are part of a collective defence agreement, Article 5 of NATO is generally the go to for people but there is also the signatories of the Common Security and Defence Policy in the European Union. There is also Article 107 of the UN Charter, or as I like to think of it, the 'Fuck the Axis' clause, but that's not really relevant unless you want to dig really deep into the weeds. And from this, you should also note that what Putin is doing is an Illegal War.
If we go back to Clausewitz again, we can see that he defined one of the preeminent legal criteria for war, which he called Violence;
…there is no known cyber attack that unequivocally meets Clausewitz’s first criterion: violence. No cyber offense has ever caused the loss of human life. No cyber offense has ever injured a person. No cyber attack has ever damaged a building.
Thomas Rid; Cyber War Will Not Take Place
We can get into arguments about TRITON/TRISIS being used to kill people and that IF, and that is a BIG IF, it had worked it would have absolutely been a Violent act. Or you could look at Stuxnet where according to Kim Zetter, in her book Countdown to Zero Day, President Obama was shown pieces of a destroyed centrifuge, though while we know centrifuges were being replaced at Natanz thanks to the IAEA, we don't know if they were destroyed or damaged, or if removal was part of malware eradication. You could even look at the German Steel Mill incident in 2014 where apparently cyber warfare was used to destroy a Blast Furnace, but little is known about this incident in open sources. Ultimately, in open sources, we are unaware of cyber causing such effects.
This understanding of cyber having yet to have such an effect is so clear that even here in Ireland, where we are so far behind the times, Irish law even recognises that Violence isn't something cyber is being used for as in Irish law, Violence implies that an attack took place and caused some harm to someone or something. The Criminal Justice act covering computer things only mentions the word Attack a single time, wherein the preamble, it quotes the EU Directive that was the basis for the law;
An Act to give effect to certain provisions of Directive 2013/40/EU of the European Parliament and of the Council of 12 August 2013 on attacks against information systems and replacing Council Framework Decision 2005/222/JHA; for those and other purposes to amend the Criminal Damage Act 1991, the Bail Act 1997 and the Criminal Justice Act 2011; and to provide for related matters.
Tithe an Oireachtas; Criminal Justice (Offences Relating to Information Systems) Act 2017
If you take the time to read the law, you will also notice that all of the sections are related to how a hacker accessed data, such as access without authority, interception or using passwords or tools to access the data without lawful authority. These complexities, have led me to carry around a fun bit of text to deploy where needed, including sources;
Cyber Attacks are an internationally defined legal concept, whereby a Cyber Operation [1] is carried out by a Subject of International Law that is reasonably expected to cause injury or death to persons or damage or destruction to objects [2] [3].
A Cyber Operation is the use of cyber capabilities to totally or partially destroy, capture, or neutralize tangible objects such as computers, networks, and other infrastructure in cyberspace, which make an effective contribution to military action by their nature, location, purpose, or use [4]. This effort is made to link the attacks to existing Humanitarian Law, but also because existing law expects that the use of such a capability should have the same impacts and characteristics as a kinetic weapon [5]. This Cyber Operation must also be carried out by someone subject to international law as not everyone is, these people are called Subjects of International Law. Subjects are limited to States, Entities Legally Proximate to States, Entities Recognized as Belligerents, International Administration of Territories Prior to Independence, and International Organizations [4]. Beyond this, Individuals, Corporations, Non-Self-Governing Peoples, and Entities Sui Generis in specific situations, such as Human Rights, Trade Law, National Liberation Movements, and the Roman Catholic Church respectively [6].
The criteria one should be looking for to identify a cyber intrusion as a Cyber Attack is;
❓ Was there a Cyber Operation?
❓ Was such an intrusion reasonably expected to cause injury or death to persons or damage or destruction to objects?
❓ Was the intrusion carried out by an actor Subject to International Law
- Schmitt, et al, 2018. Tallinn Manual 2.0. On the International Law Applicable to Cyber Operations. 1st ed. Cambridge: Cambridge University Press, pp.521.
- Schmitt, M., 2013. Tallinn Manual on the International Law Applicable to Cyber Warfare. 1st ed. Cambridge: Cambridge University Press, pp.106-110.
- Schmitt, et al, 2018. Tallinn Manual 2.0. On the International Law Applicable to Cyber Operations. 1st ed. Cambridge: Cambridge University Press, pp.415-420.
- Schmitt, et al, 2018. Tallinn Manual 2.0. On the International Law Applicable to Cyber Operations. 1st ed. Cambridge: Cambridge University Press, pp.435-445.
- Brown, G. and Metcalf, A., 2014. Easier Said Than Done: Legal Reviews of Cyber Weapons. Journal of National Security Law & Policy, Vol 7(No 1).
- Crawford, J. R., 2012. Brownlie's Principles of Public International Law. 8th ed. Oxford: Oxford University Press, pp.115-126.
Now we can quibble if taking an understanding of Cyber Law from the Tallinn Manual is an appropriate approach, but ultimately, under current legal understandings, Cyber, in the realm of military uses of Cyber, is a deeply legal topic. The ultimate impact of these legalities has even led Thomas Rid to proclaim that Cyber War has not happened, isn't happening now and won't happen in the future;
Cyber war has never happened in the past. Cyber war does not take place in the present. And it is highly unlikely that cyber war will occur in the future. Instead, all past and present political cyber attacks are merely sophisticated versions of three activities that are as old as warfare itself: subversion, espionage, and sabotage. That is improbable to change in the years ahead.
Thomas Rid; Cyber War Will Not Take Place
What is also particularly prescient about this observation is that War is not a thing that takes place in a single domain of battle. Cyber is a form of warfare that can be utilized as seen fit by a military. In the Fifth Domain, the Information Domain, you can use Cyber to have impacts beyond the information Domain, in Land, Sea, Air and in Space, making it just one of a number of tools in a toolbox rather than the tool you use to fight a war.
The Subversive Trilemma
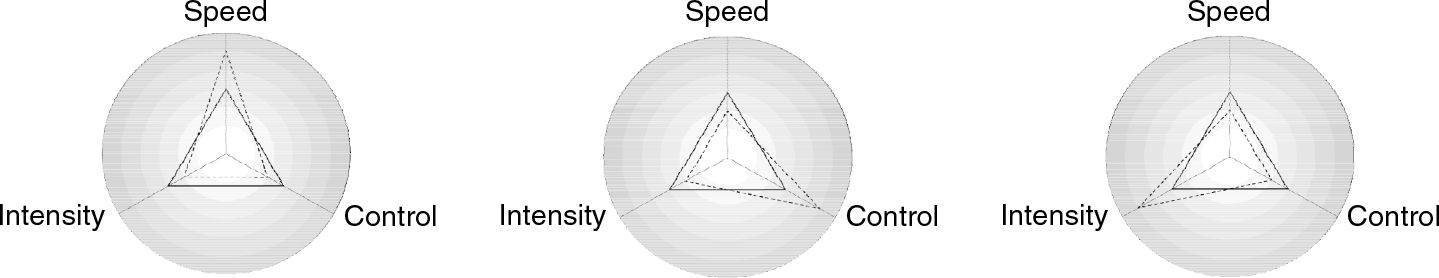
Rid talking about Cyber as a sophisticated version of Subversion is also something worth examining as a recent paper by Lennart Maschmeyer makes clear where there are limiting factors that constrain not just the usefulness of Cyber, but also what Cyber is capable of. Maschmeyer Defines the three variables as;
Speed - The time taken from the start of the operation to the intended effect. Effective and secret reconnaissance takes time, as does the development of exploits for use against system vulnerabilities, using exploits at scale can take time to avoid detection and learning the systems and networks post exploit takes time.
Intensity - The severity of effects. Minimal system effects are relatively easy to attain, though they may not have the intended effect. Larger effects, such as we could have seen with TRITON/TRISYS, which could have caused the release of hydrogen sulfide gas that could have caused death or injury to people or caused a failure of plant systems resulting in an explosion.
Control - The amount of control you have over a given system. Put simply, the more control you have over a system, the more commands you have run on a given system, which in turn generates noise that could be detected and alerts to analysts have a tendency to be acted upon.
These factors are negatively correlated so if you prioritize one, the other ones are sacrificed as can be seen from this diagram from Maschmeyer's paper;
If we were to compare, for example, the OLYMPIC GAMES program as a whole to recent events, we can learn a lot about how this pans out in practice. The OLYMPIC GAMES was a project spanning 5 years, maybe more, and costing approximately a billion US Dollars, and over that time produced two pieces of malware, possibly three. The third is Stuxnet for North Korea, which very little is known about. The two main pieces are Stuxnet 0.500 and Stuxnet 1.001 and the subsequent patches, 1.100 and 1.101.
Stuxnet 0.500 was developed using a replica of the Natanz Enrichment Facility at the Y-12 National Security Facility where the aim was to create malware that lived on the PLCs that controlled the centrifuge's feed and dump systems rather than the centrifuges. It would feed excess gas into the systems, which caused excess pressure and forced the system to dump the gas to be enriched into a waste tank leading to next to no enrichment taking place. Development started in 2005 and was deployed approximately in 2007, where it ran for a period of time, laying undiscovered until 2013. It ran without any C2 whatsoever, which limited control and had the ultimate effect of just slowing the enrichment process. Stuxnet 0.500 had a slow operational speed with limited control, but massive effects.
Stuxnet 1.001 is the version of Stuxnet that everyone is familiar with. Development started in approximately 2007 with the aim of having more control over the virus so that the US could react to Iranian actions rather than deploying the malware and then not having malware present when systems were replaced. 1.001 was also intended to have larger effects, something the replica facility was used to test where Kim Zetter in her book Countdown to Zero Day mentions that President Obama was shown pieces of a destroyed centrifuge.
Initially, 1.001 was slower moving than expected and unhappy with the progress that was being made, the C2 that was in place was used to patch Stuxnet to the 1.100 variant, which is the variant most people are familiar with. This patch is the one that sent Stuxnet into overdrive and turned it into a massive news story that scared people. It was quickly patched to the 1.101 variant, which was more controlled and careful, but it was too late at that stage and the cat was out of the bag. In attempting to have more control and intense effects, for the same operational speed, Stuxnet became made too much noise and was detected. Most likely it was deemed to be an operational failure, though probably a strategic victory as it did lead Iran to come to the negotiating table to discuss what became the JCPOA.
If we look at Russia and their offensive in Ukraine, the offensive operation was approved on the 18th of January, to take place on the 20th of February. This was likely delayed several days to allow units to arrive from the Eastern Military District and also at the behest of China, to allow the Winter Olympics to finish and for China to have their propaganda victory. US influence operations dumping details of Russian plans, as covered previously, along with Ukrainian Intelligence publishing intercepts on YouTube, probably also delayed the operation until the 24th. Given the defensive efforts, which I will come back to later, this gave Russia a month to prepare not just operational plans for Land Sea and Air attacks, but also for Cyber Attacks too. This is likely why we see the use of low effort techniques such as website defacements, DDoS' or Wipers in use.
Leaked document from Russian troops showing war against Ukraine was approved on 18th January, and initial plan to seize Ukraine starting 20th Feb to 06th March https://t.co/KG2j0Pwqat #Ukraine pic.twitter.com/NlhnyBTJCv
— Liveuamap (@Liveuamap) March 2, 2022
War Criming
Now, this is complicated, and I have tried to get in contact with Ms Oonah McCrann SC, who is the JAG for Ireland, and I have also tried to consult with James Creedon CJA, who is the Wonk's go to lawyer for Military Justice issues but sadly, I have not gotten a definitive answer. Yet!
When I was delivering my version of this talk to the ICSPD Community, I wanted to discuss the fun little element of the possibility of War Crimes being committed by hacktivists. As I mentioned previously, International Law is the relevant law in the conflict between states, not local criminal law, so the presence of an IT Army for Ukraine, in a Telegram group could be problematic.
Initially, I was under the impression that Article 43 of Protocol 1 of the Protocol Additional to the Geneva Conventions would matter a lot here as the IT Army could easily meet the criteria laid out in the law;
The armed forces of a Party to a conflict consist of all organized armed forces, groups and units which are under a command responsible to that Party for the conduct of its subordinates, even if that Party is represented by a government or an authority not recognized by an adverse Party. Such armed forces shall be subject to an internal disciplinary system which, ' inter alia ', shall enforce compliance with the rules of international law applicable in armed conflict.
ICRC; Treaties, States Parties and Commentaries; Armed Forces
My assumption was that while the IT Army is recruited via Twitter, and targeting data is given out via Telegram, I was under the impression that it would be considered an Organized Unit (The IT Army), that is Subordinate to a Command of a Party to the Conflict (Government of Ukraine via Telegram), and that there is a disciplinary system in place (The Judiciary of Ukraine). This would allow them Prisoner of War status in the conflict. Though a recent paper from the CCDCOE states otherwise;
... the IT Army will not be viewed as an organised armed group to determine combatant status, and so many of the questions relating to combat and the different forms of civilian participation matter greatly. For instance, although the privilege of being treated as a POW might not hold much significance for a cyber fighter, other aspects such as becoming a legitimate military target and having limited legal immunity from criminal prosecution 2 might become very important.
Ann Väljataga; Cyber vigilantism in support of Ukraine: a legal analysis; CCDCOE Law Library
Now this throws my entire argument into jeopardy, but, I didn't want to talk about the IT Army, I think it's pretty boring and really just an outlet for the Script Kiddies out there and maybe a few solid hackers, but they can join the SBU in wartime, so that is probably a better outlet as that's a place to accomplish real goals.
What I did want to talk about was Conti though! Conti made a really interesting post, which you can view here via onion.ly. Essentially, Conti made a statement that they "condemn the ongoing war" but if they see the US participating in "Cyber Warfare" against Russian critical infrastructure, they will be unilaterally entering the war, they will "deliver retaliatory measures". This would firmly place them outside Article 43 of Protocol 1 of the Protocol Additional to the Geneva Conventions, but since that isn't relevant anymore, it would fully render them an Unlawful Combatant, a nasty status to have bestowed upon one;
Unlawful combatants are subject to capture and detention, but in addition they can be tried and punished in a trial of the capturing parties choice, including Military Tribunal to render judgement on their belligerency
Ingrid Detter; The Law of War and Illegal Combatants; pp 1063
So... If Conti were to unilaterally enter the conflict, could they be treated as Unlawful Combatants, have a Military Tribunal in absentia, and have punishment rendered? Where the punishment could be a death penalty and have Conti be... Say... Drone strike-ed? I would love to know and if possible, have this taken care of quickly!
Perceptions
Once preparations for the offensive became crystal clear, we started to see the use of Cyber in Ukrainian Government websites being defaced and Belarusian Cyber Partisans ransoming ticket machines, Adam Boileau remarked on Risky Biz that;
… it’s not the cyber war we were promised.
Patrick Grey and Adam Boileau; Risky Biz 652; 00:05:10
And I think this is where the real problem comes in for understanding the use of Cyber during wars. People have a certain picture of what the Cyber Warrior should look like and that they should run around firing cyber bullets, all pew pew pew! They imagine something like this;

These are a pile of people in camo, they are resting trigger fingers on the finger guards of their rifles, I mean keyboards, they hold the keyboards like rifles, one dude even has the keyboard on a USB cable sling around his neck. The problem with this is that new forms of warfare just don't pop into existence, they tend to have long run lineages where you can look back at the history of a given form of warfare and learn a lot about today from how these forms of warfare evolved.
If we were to look at Naval Warfare, for example, most people have in their mind's eye something like an Iowa class Battleship firing shells that weigh as much as a Volkswagen Golf, 30 nautical miles with explosives that weigh as much as a grand piano. Or they imagine a more modern guided missile destroyer such as an Arleigh Burke class Destroyer firing piles of missiles off over the horizon to hit stuff they can only see on radar or know is there because they have other sensors informing them that there is stuff there to blow up.


But if you look back at the history of naval warfare, you don't really get this long range fire concept we have today. Naval Warfare originated in Ancient Egypt where 4000 years ago, someone had the bright idea that if you couldn't win on the land, you could cause havoc by going around your adversary and attacking or raiding their rear via building ships to carry troops down waterways. The result of this is what we know today as Galley's or more popularly the type of Gally known as a Trireme. These vessels were basically ships propelled by oars with a platform on top of them where you could have soldiers. In effect what was created was land, on a boat, so you could have a land battle at sea. You ram your adversary so that you can board their ship and have a battle for control of their ship.

We see a similar problem with how people think about modern Aerial Warfare where people think about big expensive projects like modern stealth aircraft such as this F-22 with an unusual camouflage scheme made of metallic plates or aircraft such as the unbelievably gorgeous F-117 Nighthawk.


Airel Warfare experiments started before World War 1 to see what was and was not possible that ultimately resulted in a lot of ideas that have stuck around until today, the best example of which is bombing. Though unlike what people think of when they see World War 2 bombers carpet bombing cities, using the Norden Bombsights, you have some guy, in a flimsy cloth and balsa wood plane, aiming with the Mk 1 Human Eyeball and basically chucking modified hand grenades out of the plane, such as this example of a 20lbs Hales Bomb;

Even though Clausewitz was long dead by World War 1, this kind of creation and change in warfare throughout history is what lead him to claim that;
Every age has its own kind of war, its own limiting conditions, and its own peculiar preconceptions.
Carl von Clausewitz; On War; pp 593
The finest modern example we have today is that of the French Cuirassier. These were a type of highly mobile light Cavalry unit that was intended to fight with sabre and firearm either on horseback or dismounted as needs be and were famous for having not just horsehair helmets but also breastplates like knights of old. At the start of World War 1, they rode into battle in not just their shiny armour, but their brightly coloured uniforms like a unit from a bygone era and in the face of machine gun fire, they didn't fare well.

But the idea of having a unit that can fight both mounted and dismounted with a range of weapons is not an idea that is dead and gone and not just that, the unit still exists today as the 12e Régiment de Cuirassiers. They have been Peace Keeping and performing Counter Insurgency Operations in Mali as well as training with NATO allies in recent years, having exchanged their horses for Steel Beasts. The mode of warfare changed drastically, but the concept of Cuirassier, infantry that fights mounted and dismounted, has arguably become modern infantry tactics.


The Preconceptions & Limitations of Information Warfare
If we then want to think as militaries do about how they intend to use Cyber, what we need to do is look to the past and see what Information Warfare was before computers or Cyber and then see how these preconceptions limit what Information Warfare can be used to accomplish.
Preconceptions
When most people think of Sun Tzu and his book The Art of War, they think that he was a strategic genius. Though to me, he is the first information warrior. His book is broken into 13 chapters, which are then subdivided into skills or arts one must learn to master that area of warfare. In a little bit, I will be discussing WayPoint 2028, which is how the US Army intends to fight wars from 2028 onwards. As part of this, one of the new units they will be deploying is the Theater Information Advantage Element, whose goal is to;
... provide enhanced non lethal capabilities, conduct information warfare protect friendly information and inform and influence activities ... though forward postured persistently engaged ...
Army University Press; WayPoint in 2028 – Multidomain Operations
What the US is saying is that they will be protecting friendly information, or Operational Security (OPSEC), and they will be performing influence activities, which could be any number of things from Deception Operations to Psychological Operations (PSYOPS). And these are things Sun Tzu has ideas about, from 2500 years ago, that are still relevant today. For example on OPSEC;
Hence, when able to attack, we must seem unable; when using our forces, we must seem inactive; when we are near, we must make the enemy believe we are far away; when far away, we must make him believe we are near.
Sun Tzu; Art of War; Ch 1 Art 19
On Deception Operations;
Hold out baits to entice the enemy. Feign disorder, and crush him.
Sun Tzu; Art of War; Ch 1 Art 20
On PSYOPS;
If your opponent is of choleric temper, seek to irritate him. Pretend to be weak, that he may grow arrogant.
Sun Tzu; Art of War; Ch 1 Art 22
These are only from the first chapter of the Lionel Giles translation from 1910 and may be out of date, but what I want to get across is that for such generic examples, Sun Tzu, was thinking about major problems today, 2500 years ago. And I do mean generic, these could be applied prior to Information Warfare as we know it today, but Sun Tzu was just the seed that grew a tree.
Between Sun Tzu and our next character, the Islamic polymath, Abu Yūsuf Yaʻqūb ibn ʼIsḥāq aṣ-Ṣabbāḥ al-Kindī or just Al-Kindi, there were all sorts of things tried that birthed Encryption. We saw the first substation cipher, the Atbash cipher, which replaced the first letter in the alphabet with the last, the second with the second last and so on, we saw the first transposition cipher where parchment was wrapped around the Scytale. When the parchment is read normally, it is a garbled mess, but when wrapped around a Scytale, a message can easily be read off of it. Al-Kindi's contemporary, Al-Khalil, who introduced Algebra to the world, created polyalphabetic ciphers.
Up to this point, the only way to break encryption was to get the plain text one way or another, such as understanding the keying used in the Atbash cipher, or the right Scytale was recovered to wrap parchment around. Al-Kindi was able to understand that some letters are used more than others and that this could be used to break ciphers by attempting to see if you could make a plain text by replacing a letter in the ciphertext, with the most common letter of the alphabet or most common words in a language, something that he was able to do thanks to Al-Khalil.
This was the creation of cryptanalysis and it wasn't just frequency analysis that Al-Kindi discovered. He came up with techniques to break some kinds of polyalphabetic ciphers and how to class ciphers, not to mention being a foundational scholar of Islamic Philosophy, being one of the first, if not the first person to understand light and optics, not to mention popularizing Indian Numerals like we use today
Between Al-Khalil and the next cast of characters at Room 40, lots of things happened of note such as cryptography making it to Japan in the 1500s, the French created le Grand Chiffre, a substitution cipher that relied on rather on substituting letters for other letters, it substituted French syllables for numbers, which could be referenced on a table. It was thought to be uncrackable after the tables were lost until Étienne Bazeries in 1893. And now you know Mads Mikkelsen's rad character in Casino Royale, le Chiffre, means he was called the Cipher...
Anyway, Room 40 is an interesting bunch. Naval historiographer Drachinifel described them as a headteacher, a book publisher, a translator of theological works, a naval instructor, a barrister and a scientist. These people were so much more than that though! Room 40 isn't responsible for the birth of Signals Intelligence, after all the British had been using their near monopoly on cables and radio stations to transmit telegrams and diplomatic cables for decades at this point, but what they did that was important was they fused data. They brought together intercepted signals and cryptanalysis and this was the real magic.
Room 40 was set up just after the start of World War I with the specific intent of cracking German ciphers and by the end of 1914, they had all three of Germany's major codebooks, the SKM, the HVB and the VB codebooks. These codebooks were all used for naval communications and worked by having lists of possible orders or words that could be used to create a message to send. Each order or word would be given a numeric or alphanumeric code which would be what was transmitted via Morse Code.
These cracked codes allowed the British to achieve two major events in Information Warfare. The first was at the Battle of Jutland where the early warning of a massive German deployment of ships from Wilhelmshaven allowed the Royal Navy to position their ships in such a way that the Royal Navy could bring all their guns to bear on the German ships with withering fire and where the British had the setting sun behind them so they were black dots that were hard to see and gather gunnery data on. While this seems like a sure victory, the Battle of Jutland was ultimately inconclusive as the British had a fatal flaw in their ammunition handling procedures that lead to multiple ships completely exploding as well as having poor shell design that didn't penetrate targets but exploded on the armour belt.
The other major event was the Zimmerman Telegrams. Germany was sending some diplomatic traffic over US cables as their cables were cut on day one of the war. But the cable from Europe to the US went via the UK, at a site today known as GCHQ Bude, where the UK was able to intercept this traffic. The German State Secretary for Foreign Affairs, Arthur Zimmermann, sent a cable to Mexico, informing them of their intent to start Unrestricted Submarine Warfare. At the time it was a huge deal, less so today, but the US had drawn a hard red line under Unrestricted Submarine Warfare and would get involved on the side of the Entente in WWI if Germany chose to pursue this idea. To throw a spanner in the works, Zimmerman was inviting Mexico to join the war on the side of the Central Powers and was promised territory lost to the US in the preceding decades such as Texas, New Mexico and Arizona.
Mexico declined this offer as by the time they had the opportunity to reply, the British had publicized the story, though their store was that British agents in Mexico had stolen the telegram when they had cracked the diplomatic codes being used and decrypt the intercept, keeping Mexico out of the war, Germany isolated and the worlds largest economy on the side of the Entente. It should though be noted that it's not crazy to think that Mexico could have entered the war. After all just 3 years prior, the US had invaded Veracruz, the US was funding arms sales to anyone who rivalled Francisco "Pancho" Villa, and on the subject of Villa, the US had a decade long Expedition to capture Villa that included totally not invading Mexico and going at least 500 miles South of the US border.
This wasn't the only major breakthrough that Room 40 gave us. They also hit upon the idea of Radio Direction Finding, whereby turning the island of Great Britain into effectively a giant antenna, they were able to detect and locate transmissions made by German ships. You see long distance radio transmissions are a matter of power. The more power your transmitter uses, the further it can send signals. And the Germans only operated at full power. They could easily be heard from the UK. With the aid of spherical trigonometry, you can pretty accurately locate where a signal emanates from, using Spherical Cosine Law. Room 40 got so good at this that they stopped decrypting certain transmissions as they knew they were related to minefields and could precisely plot the locations of German minefields with great accuracy.
Room 40 ultimately became the Government Code and Cypher School or GC&CS and was based at a little place you may have heard of called Bletchley Park, ultimately becoming an organisation you also may have heard of called GCHQ.
Post World War I while there was a nearly unbelievable run of inventions and discoveries that lead to mechanical encryption, mechanical cryptanalysis, the massive proliferation of signal generating equipment like telephones, all sorts of wireless communication for the everyday person in the street and the birth of digital computing to just skim how we got to today, there are really only two things the left on the list of preconceptions in Information Warfare. The work of Claude Shannon and the idea of communication as a mathematical concept, and how this allows not just the entire concept of Electronic Warfare (EW), but more importantly for how people think about Cyber Warfare, the birth of Electronic Attack.
While you could argue that the Royal Navy getting a warning that the German Navy had left port and you could attack them, this isn't really an attack as the platform, such as Admiral Jellico's flagship HMS Iron Duke at Jutland, isn't collecting data on the Electromagnetic (EM) Spectrum and then attacking based on that. In World War 2, the UK would widely deploy their ASDIC system, which today we know as sonar, in combination with the Radio Direction Finding that Room 40 developed to allow the Royal Navy to locate and home in on Nazi U-Boats and drop depth charges or early forms of acoustic homing torpedoes. This concept of allowing platforms to gather and deploy weapons against targets that are only detected in the EM Spectrum opens up a whole new world to fight in.
The UK was not the only side playing around in these early stages of Electronic Warfare, in fact, all the major powers in World War 2 were playing with EW. The one to watch though, that's gotta be Japan! During the Battle of Singapore, several ditched Hawker Hurricane fighters were ditched, but in good shape, and were later captured, specifically that of Squadron Leader Richard "Ricky" Brooker, whose Hurricane, BE 208, was later restored and flown by Japan in 1943. These Hurricane's had a feature called Identify Friend or Foe (IFF) which allowed radar operators to distinguish friendly aircraft from enemy aircraft. This system went on to be used on ships as well as on aircraft so that the allies could detect friendlies across the board.
Japan had an air search that on the ground was called a Type 12 and aboard ships was called a Type 21, and it operated in the range that the IFF system would respond to radar pulses with. This response to pinging, from enemy sources, would make this maybe the first case in history of CWE-284: Improper Access Control. If you believe this as I do, it would also make this maybe the first instance of Cyber Warfare in history! And not just that, it would also be using what is undeniably modern attacker techniques.
Now the scuttlebutt here is a little speculative I don't have all the links in the chain but it's a great story if it's true! Japan also operated the Tachi 35 Height Finding Radar, and with a bearing and range from the Air Search Radar, Japan could figure out if something was a ship, or if it was a plane and by tracking movements and watching changes over time, you could build patterns and use those patterns to say, identify an Aircraft Carrier, in 3D space and do it to within as small a window as 1 mile.
I say 1 mile because the ping you get back isn't a little tiny response, it's a large wideband signal you get back, and because this is the case, you potentially can hide in this band, which is how I believe that Japan targeted the USS Bunker Hill, by utilizing the US' inability to see his plane in the natural camouflage of clouds and the concealment on the EM Spectrum provided by friendly US Aircraft;
Japanese Sub Lt. (j.g.) Yasunori Seizō piloted a Zero that went undetected by radar and emerged from the low broken clouds on Bunker Hill’s starboard quarter.
Naval Histroy and Heritage Command; Bunker Hill I (CV-17)
Now, one kamikaze getting in would be a fluke, but 30 seconds later there was a second undetected kamikaze, and then a little later there was a third. In maybe as little as a minute, there were three kamikaze attacks on Bunker Hill. I am a firm believer that coincidences don't just happen and while this was on the 11th of May 1945, I can see this as being a test of Japan's ability to perform kamikaze attacks on US carriers.
This isn't the only thing Japan was working on along these lines, they were developing something called a HAMA 63 Foe Aircraft Locator which the US Army Air Force described as an Interception Computer (pdf page 90-92) and was effectively a new type of entirely electronic and automated Ground-Controlled Interception (GCI) system, that was radically different from what the British for example operating. It is also possible that it was a very early form of Airborne Warning and Control System (AWACS) where an airborne radar plane could be used to identify Allied aircraft and have other aircraft in its formation target them.
Finally, if we look forward to the near future, I mentioned the US Army's WayPoint 2028 doctrine. This is generally interesting to me for a lot of reasons, but on the Information Warfare aspects of it, I want to point out a few things. First is that in the Perceptions section, I mentioned that you can use Cyber to have impacts beyond the information Domain, in Land, Sea, Air and in Space. This is how militaries think about weapons systems. You don't have a missile that you can only use to blow up a Frigate or a shell you can only use to blow up a tank. The missile is an Anti Ship Missile and can target all ships and maybe more. Tank shells can blow up helicopters and armoured personnel carriers as well as tanks.
This thinking has led the US Army to set up a what they call the TFC or Theater Fires Command, which will be used to provide fires to support missions and crucially, they show tube and rocket artillery in the video, but also some people with a pile of antennae all over the place. This is the big hint that they meshing the old school fires that one expects with new capabilities. The other interesting unit is the Cyber Warrior or the TIAE, Theater Information Advantage Element which will;
... provide enhanced non lethal capabilities, conduct information warfare protect friendly information and inform and influence activities ... though forward postured persistently engaged ...
Army University Press; WayPoint in 2028 – Multidomain Operations
Now that is pretty clear that these people should be Information Warriors rather than Cyber Warriors right? Well if you are familiar with the US Department of Defence's 2018 Cyber Strategy, you will be aware that Persistent Engagement and Defend Forward are what the DoD is calling Cyber. In effect, cyber is sexy with policymakers, but they don't understand it, so the DoD is telling policymakers that this is the cyber magic, but the boots on the ground, who know the details in and out of their roles and have spent years training, they know it as Information Warfare and that Cyber is just one of the tools available as they also have PSYOPS and OPSEC, which can easily be done without computers and are essential as we learned from Sun Tzu.
Limitations
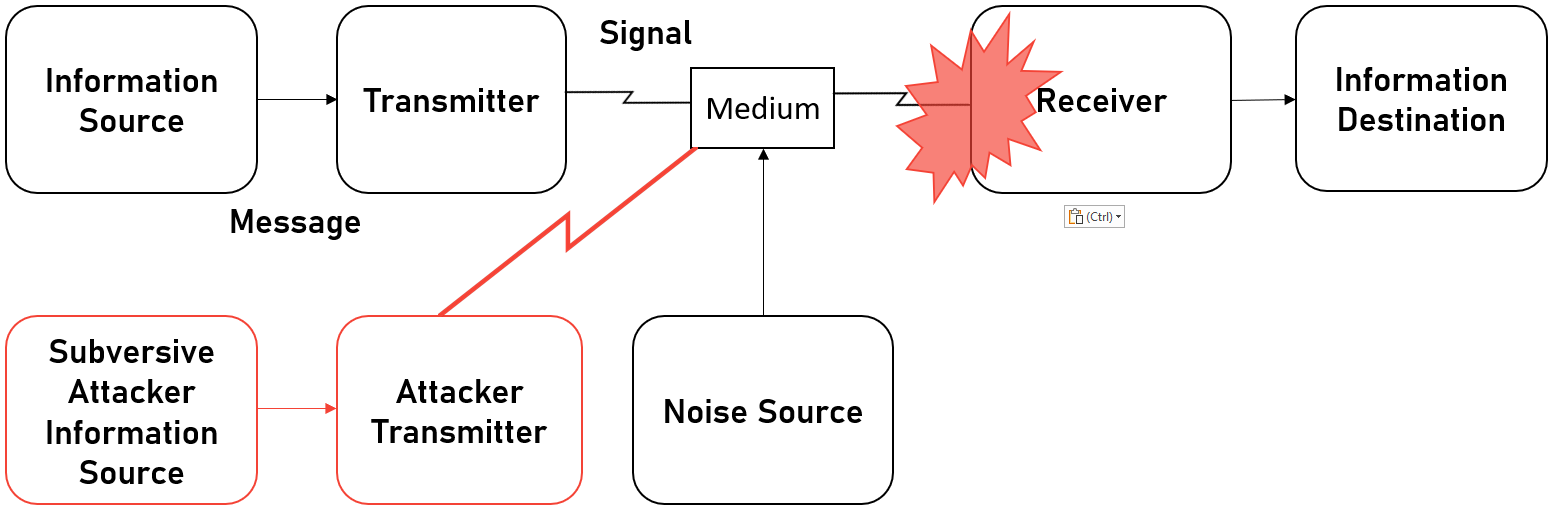
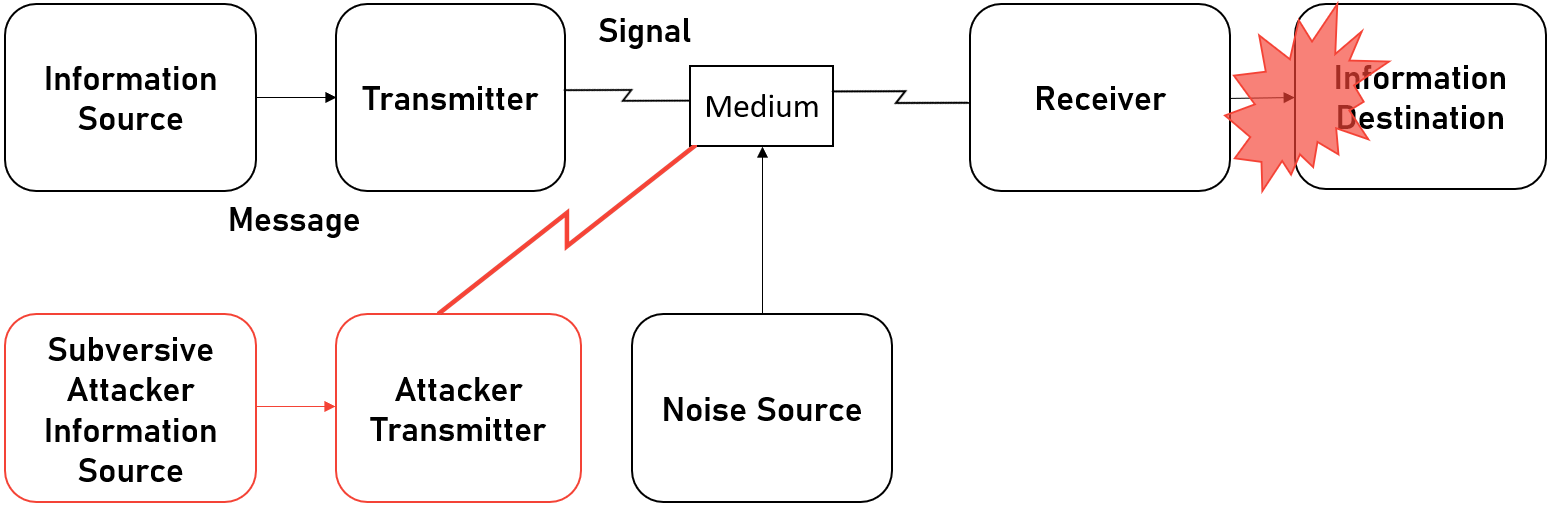
I did say I wanted to talk about the work of Claude Shannon and his groundbreaking work A Mathematical Theory of Communication, but there's a new heading? Well, Shannon's work is both a blessing and a curse. While it opens up an entirely new dimension for battle, it also imposes a single massive limitation on what is possible in this dimension. Shannon defines a generalized communications system that looks like this;
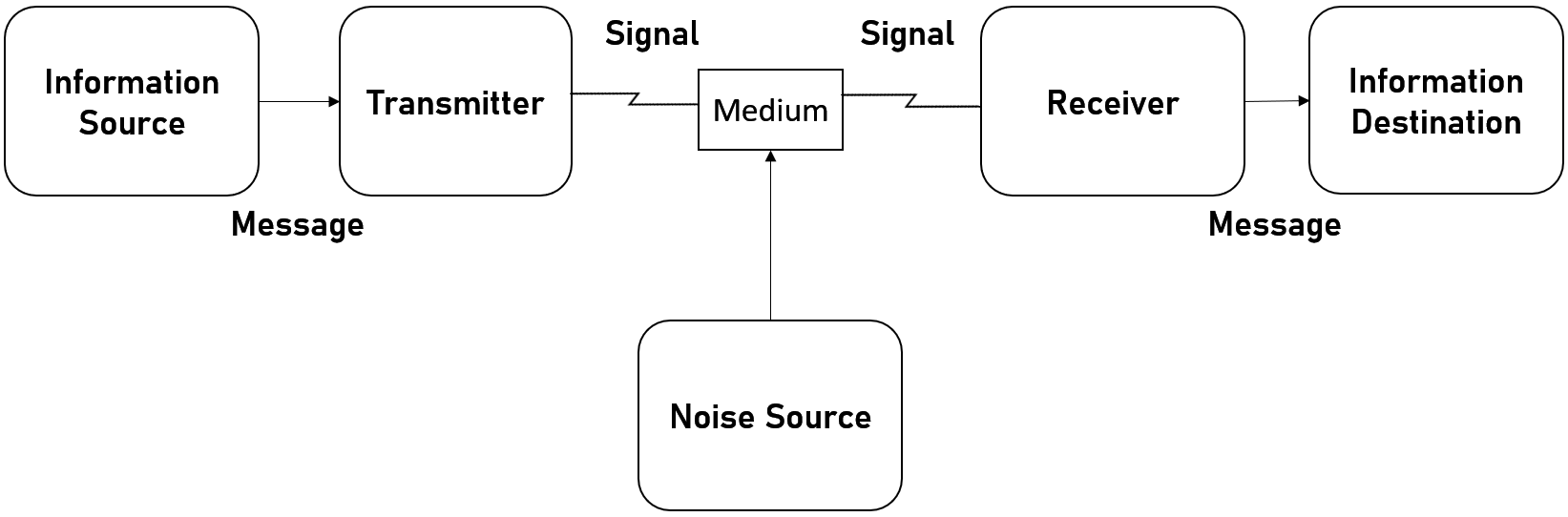
Where the Information Source is the system that generates a message to be communicated and he defines the generation as functions. So when I speak, there is a function for speaking f and my speech happens over time, so the generation is f(t). Much like any function, you can add as many parameters as are needed by this function. The Transmitter takes the generated message and produces a signal for transmission. This isn't like the OSI 7 Layer model where a series of processes happen to send data, this is more like the Data Link Layer where data is put into Frames that can be transmitted.
Then there is the Medium as I call it, or as Shannon calls it, the Channel. This is simply the medium that the transmission can pass through such as air or a wire etc. The Reciever is the inverse of the transmitter, taking the signal and turning it back into a message. Finally, there is the Destination, which is the system that the message is intended for. For example, I gave the example of me speaking, you listening to me, makes you the intended person or system the message is for.
The curse is that if this entire dimension of warfare is defined by sources, transmitters, mediums, receivers and destinations, then you have a massively limited set of targets to attack. So when people are expecting a Cyber War and the massive power of cyber, they are aware that the potential of cyber is everywhere, but not necessarily that cyber can do what you imagine it can.
So when we see malware that targets Industrial Control Systems such as TRITON (aka TRISYS), people see that the malware targeted Safety Instrumentation Systems (SIS), and yes this is scary and dangerous and something that could legitimately kill people, but if you look at what SIS does, it is simply a sensor, a logic solver and a final control element. The sensor monitors variables in an environment, then the logic solver determines if these variables are within safe parameters for a process and if they are outside the safe area, the final control element is an off switch that turns a given process off.
So while this seems simple in theory, it ignores the hoops you have to jump through to get to an SIS and how the Subversive Trilemma impacts your actions, but most of all, it limits how you can actually use Cyber capabilities against the SIS. Though it should be noted that hackers have an advantage that militaries to date haven't had. Systems such as SIS' to Supervisory Control and Data Acquisition (SCADA), which allows humans to interact with the machinery of a process, are connected not just by cables, or wirelessly or some other medium, but they interact via protocols that abstract the physical operations taking place to something that not just computers can understand, but that hackers can natively interact with.
So What Cyberz Pew Pew do we See In Ukraine?
When it comes to Information Warfare, there are two models that you can use to look at Information Warfare. The first is the Borden Model, which breaks Information Warfare into 4 categories;
- Degrade
- Corrupt
- Deny
- Exploit
And second is the Kopp model, which breaks things down to;
- Denial of Information
- Deception and Mimicry
- Disruption and Destruction
- SUBversion / Denial
There is nothing wrong with the Koop Model, and it is still based off of the work of Claude Shannon, but I just have a preference for the Borden Model as for me, it is just easier to understand, so I will be looking at things through Borden's lens. And just for going forward from here, in the talk, to give background to the various categories of attacks, I give events from outside the current war, and then what we see currently so that you have the opportunity to fully understand the categories in the Borden Model.
Attacks that Degrade
Shannon defined Information as the reduction of uncertainty, better known as noise, in data transmissions. So to attacks that Degrade information, you have attacks that do useful work on the information itself. Borden saw this as attacks that introduce malicious noise into a system, such that the level of uncertainty remains high, but beyond the examples he gives in his paper, it's not a useful way to look at the problem. I see attacks that degrade as ways of attacking the information itself rendering the data useless or creating a delay such that the information is useless by the time it is available to be processed.
Wipers
Something that we have seen before and during the War in Ukraine is Wipers, some have even been directed at Ukraine previously like NotPetya, but there have been others such as Shamoon. There are more interesting attacks that degrade information in the War in Ukraine currently, so for background, I have discussions to follow on Shammon and NotPetya and I will skip over discussing the likes of WisperGate, HermeticWiper, CandyWiper etc and discuss what I see as more interesting forms of attacks that degrade information in the War in Ukraine.
Shamoon
Shamoon is a Logic Bomb, released by "The Cutting Sword of Justice". This group is widely believed to be Iran but there is no substantive evidence in open sources to say that this is the case. The bomb was set to detonate on the 15th of August, 2012, in the middle of the Muslim holy month of Ramadan, across the whole company of Saudi Aramco, and potentially also RasGas, the Qatari national petrochemical company, though this has never been publicly confirmed. The choice of timing would ensure maximum damage with minimal chance to stop the bomb as the company would be operating on a skeleton staff of western, non-Muslim staff.
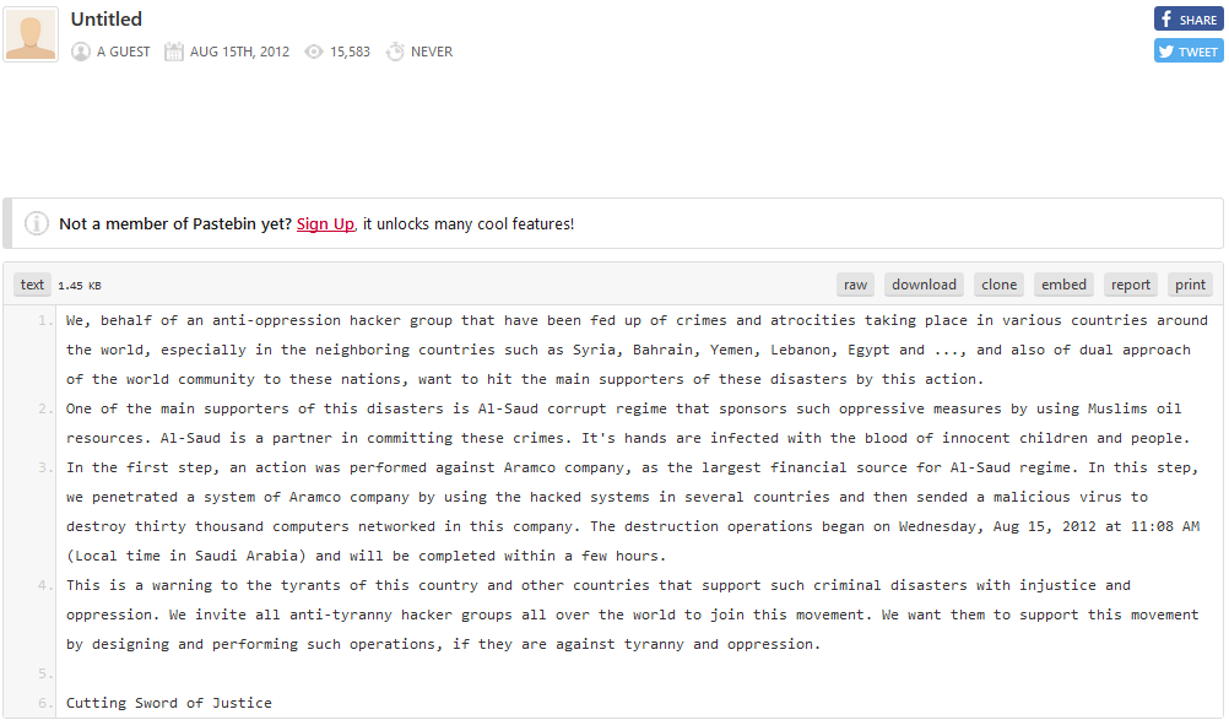
The Attack is believed to have begun in April or May of 2012 via a phishing attack, potentially taking advantage of a vulnerability in Word or Adobe Acrobat which gave the attackers a reverse shell into the network. This computer was potentially a proxy for the rest of the network to a C2 server. Due to the flat nature of the IT Network, the attackers gained control of the Domain Administrator account and essentially had total control over the business functions of Aramco. They used this to deploy Shamoon on the network which used a dropper to drop 32 or 64-bit versions on devices and when the time came, along with a reporting component to communicate with the proxy or the C2 directly and a wiper called RawDisk, a commercial disk wiping program that can, in usermode, without using Windows API's, directly modify the disk, circumventing Windows security features. In total, the bomb hit 35k systems, about 85% of IT infrastructure and took about 3.5 months to recover.
Aramco had a separate Operational Technology network that was made of ICS, SCADA and SIS systems that were able to keep functioning, though to prevent the risk of this becoming infected, Aramco chose to disconnect from the internet. Something they did a total of three times throughout the infection. Which for the world was a lucky thing. Aramco provides 25% of the world's energy needs. If RasGas was also hit, that's 14% of the world's energy needs. In total, nearly 40% of the world's production of energy could have vanished in minutes. Would that have been sufficient "scale and effects" to be considered an Armed Attack if it had happened? Hard to say, NATO's CCDCOE has it as a real world example of a state or state sponsored hacking campaign, on its short, shortlist of 51 such articles.
It's also worth noting that Shamoon may not be dead. It has made two comebacks, Shamoon 2 which had similar targeting to the Aramco attack and timing in accordance with a time when people would be out of the office, though this was a weekend rather than a holy holiday. And Shamoon 3 which attacked an Italian petrochemical company, Saipem but operated with a different modus operandi to previous versions and had some previous functionality removed.
Jack Rhysider has an amazing episode of Darknet Diaries on Shamoon and it's not just amazing because of the background it gives you into Shamoon, but also the recovery process for Saudi Aramco with the woman who lead the recovery.
NotPetya
NotPetya is a fascinating piece of malware. Essentially it is a data wiper, but not like any you have seen until recently with Russia's offensive in Ukraine. It masqueraded as ransomware, it even told you how you could pay to recover your system, but no key ever existed to decrypt your device, even if you paid. This may have been the first case of deliberately dysfunctional malware which had the absolutely intended consequence of destroying systems and making them unrecoverable. Not only did it have EternalBlue two months after it dropped, but it also had ways to get on to systems that were patched against this vulnerability.
The attack was simple. In Ukraine, basically anyone who files taxes or does business in the country uses a piece of software called M.E.Doc to do and file those taxes. The update servers for M.E.Doc were hijacked by Sandworm which essentially gave them a backdoor into thousands of computers, and on thousands of LANs and with EnternalBlue, it gave them the potential to access millions of devices. To ensure it could spread with incredible speed, Mimikatz was also used to access users' credentials and use them to access other machines on the network. The combination of both is brilliant as if there is a single unpatched device on the network, EternalBlue can get you in and Mimikatz can use credentials it finds to log into devices that are patched.
Once it was on a system it worked to encrypt the Master Boot Record, or MBR, which had two major impacts on a system. The first is that with the MBR encrypted, the system didn't know how to find the operating system. The second is that the Partition Table was encrypted so that the location of all your files is essentially lost forever†. With the MBR encrypted, the malware would set itself as bootable media in the MBR and boot to the error message you see below.
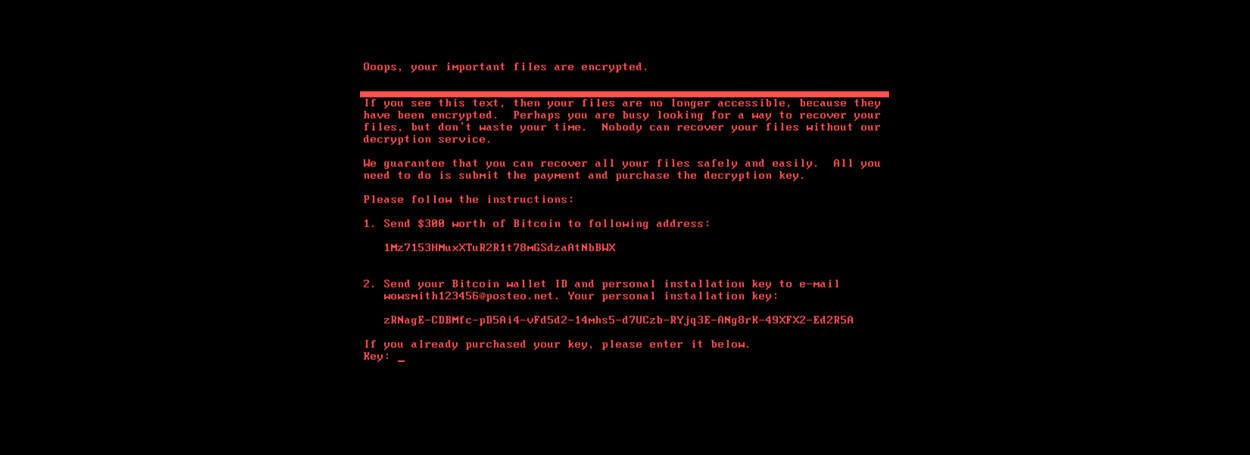
Wired has a breakdown of the cost of the damage caused by NotPetya that includes the $10 Billion in damages and the untold destruction of computers in what the Ukrainian Minister of Infrastructure summarised as "The government was dead" as an estimated 10% of all computers in the country were dead and all of this was done in about 45 seconds in what has been called "fastest-propagating piece of malware we’ve ever seen".
If you want to learn more, there are tons of great sources on this! Andy Greenberg's fantastic book Sandworm, where chapter 24 is dedicated just to NotPetya. There's a great episode of Darknet Diaries on it and unusually, we have an inside account from the Identity & Access Management Subject Matter Expert, and later IAM Service Owner at Maersk who was on the front line of dealing with the impacts of NotPetya.
HTTP 418
This is hands down my favourite attack, it's simple, there's not much to say, but it's wonderful! Someone hacked the Russian Ministry of Defence's website to respond with the HTTP error 418, informing the world that it was no longer a webserver, but it was now a teapot when queried with the Hyper Text Coffee Pot Control Protocol. Effectively it's a very simple DDoS.
Russia's military website (https://t.co/FZOqrzvQ8R) is currently down, returning HTTP 418 (I'm a teapot) 💀💀💀 pic.twitter.com/s7QYbz0Y01
— dangered wolf 💙💛 (@dangeredwolf) February 25, 2022
Painting the Electromagnetic Spectrum
Today in Ukraine we see some different things going on that are interesting. Russia operates a Numbers Station known to the world as The Buzzer or UVB-76. One of the things we have seen happen on the chunk of spectrum that UVB-76 usually operates on is where pirates have been drawing pictures in the waterfall of the spectrum by injecting bits of noise onto the spectrum. These bits of noise form a pixel on the waterfall. Of course, you can use pixels to make images and this is what the pirates have been doing. These pictures range from pictures such as My Little Pony characters, a cute little bee and various other objects.
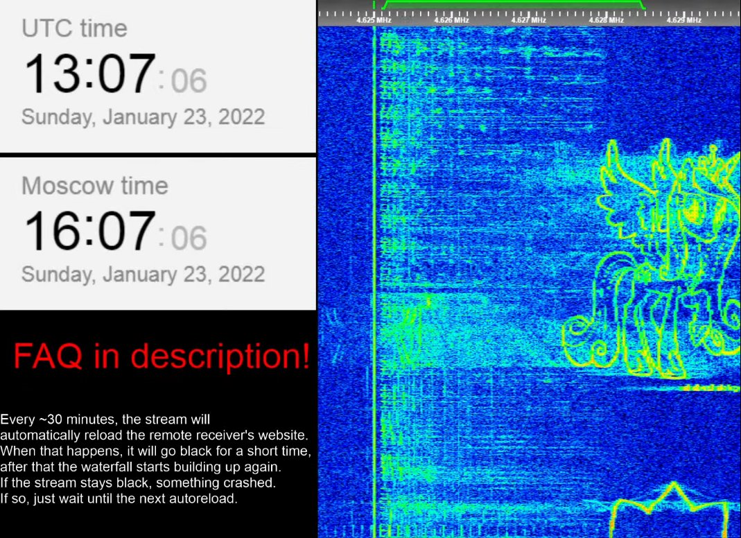
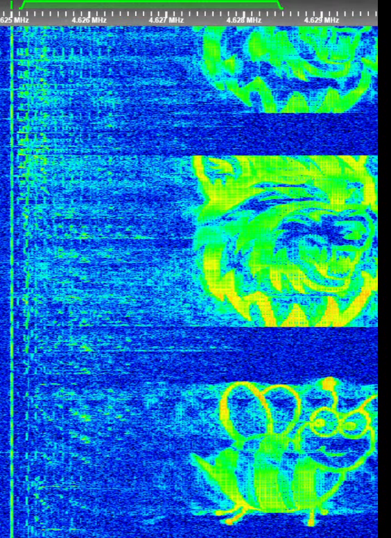
Jamming GPS and/or GLONASS
Ukraine being a post-Soviet state has access to all of the toys that we left behind and some of these systems were Electronic Warfare (EW) systems. One of the things you can EW systems is to jam a radio frequency. While the concept of jamming can get very complex, so complex that I need help from a friend to explain it to me like I was a 4 year old, in its simplest form, jamming is just increasing the signal to noise ratio that the device to be jammed.
When we look at GPS, for Civilian or Military use, the signal that arrives at your device arrives at a precise frequency with very precise timing data attached to it. If you were to increase the noise around a given location, you would end up in a situation where the timing signature could be slightly manipulated by making it so that part of the signal was unintelligible or error correction changed the timing signature to something else.
Since we are dealing with things moving at the speed of light, and light travels one foot in a nanosecond, if you were to even make slight changes to the timing data, you could massively impact the location of things compared to where they actually are in the real world. Realistically you can only offset things by tens of feet, but that is more than enough to defend locations and we have seen exactly this in Ukraine recently where Ukraine has protected at least some of its air defences with this technique and there is little Russia can do about it
This lost Russian UAV may be due to Ukrainian jamming of Global Navigation Satellite Systems (GNSS) around their SAM sites.
— Trent Telenko (@TrentTelenko) March 14, 2022
There has been some evidence of this going on circulating on various Discord server forums from the beginning of the war.
The Russians are aware by now
1/ https://t.co/1q9x10LTI2 pic.twitter.com/aeheIiUqFj
The KA SAT Kerfuffle
I brought this up with the ICSPC Discord but I chose not to use at BSides as the information had yet to firm up and I didn't want to make unfounded statements based on what I had inferred rather than on what there was evidence for, to such a large and public audience. Since then Viasat has released a statement and more data has come to light, so I can talk about what I know, sans speculation.
To understand this whole thing, you need to understand that KA SAT is a satellite operated by Viasat and bandwidth on this network is resold to others, and what is relevant in this case is that it is resold to Skylogic, a subsidiary of Eutelsat, where the satellite internet service is called Tooway. Viasat has made a statement where they effectively threw Skylogic and Eutelsat under the bus;
This incident was localized to a single consumer-oriented partition of the KA-SAT network that is operated on Viasat’s behalf by a Eutelsat subsidiary, Skylogic, under a transition agreement Viasat signed with Eutelsat following Viasat’s purchase of Euro Broadband Infrastructure Sàrl ("EBI"), the wholesale broadband services business created as part of Viasat's former partnering arrangement with Eutelsat. The residential broadband modems affected use the “Tooway” service brand. This cyber-attack did not impact Viasat’s directly managed mobility or government users on the KA-SAT satellite. Similarly, the cyber-attack did not affect users on other Viasat networks worldwide.
Viasat; KA-SAT Network cyber attack overview
In effect, Skylogic's Tooway network was compromised and as the attack went on, there was also a decline in the number of modems connected to the satellite. Ruben Santamarta, known for his Reversemode blog, released a post where he looked at the ASNs that Skylogic has and noticed that they use Fortigate appliances, which had some pretty major issues in 2021 with a leak of user passwords, which lead to a spate of hacks on Fortinet big iron. Once inside the VPN network, they were able to access the management API, which Ruben also found and posted in his blog. Through this, he concludes that the TR069 protocol was being used to install an app on the modems, which the AcidRain wiper, taking them offline.
Rubber-Hose Cryptanalysis
Finally, we have the attack that I predict most often, the attack where a provider is taken offline. Normally this is something that I would expect to see via having a cable cut, particularly one on the seabed as the lead times to fix such an issue are in years rather than days, but in Ukraine, we have seen an example of a provider going down due to what I have seen described on the grapevine as coercion.
The employee who was coerced is now safe which is good news, but we know very little else beyond that this person was coerced into giving up credentials and these credentials were subsequently used to take down Ukrtelecom. I'm sure you can imagine what I believe to be the series of events that took place given the heading I chose to use and Russia's history recent in places like Mariupol, Bucha or Borodianka.
📰 Hackers took down #Ukraine's national internet provider Ukrtelecom by stealing credentials from an employee in a territory recently occupied by Russia, then compromising and gaining access to the ISP's network.
— NetBlocks (@netblocks) April 6, 2022
🖋 @SebMoss writes for @dcdnewshttps://t.co/n2YV74v9ep
Attacks that Deny
Attacks that Deny are attacks that attempt to render the assets that collect and process data useless. Traditionally, this has been attacks on receivers that are collecting information.
Suppression of Enemy Air Defenses (SEAD)
On the 20th of June 2019, the IRGC shot down an American RQ-4 Global Hawk drone that Iran contends violated Iranian airspace in the Strait of Hormuz. Iran used سوم خرداد or a 3rd Khordad, sometimes called a Sevom Khordad, air defence missile system.
«#پهپاد_آمریکایی در دام سامانه پدافندی ایرانی؛ اولین شکار در کارنامه "سوم خرداد"»
— خبرگزاری تسنیم 🇮🇷 (@Tasnimnews_Fa) June 20, 2019
پهپاد آمریکاییRQ-۴ توسط سامانه پدافندی سوم خرداد ساقط شده است؛سامانه پدافندی سوم خرداد یک سامانه پدافندی کاملا بومی است که به دست متخصصان صنایع دفاعی کشور طراحی شده است https://t.co/wOY25bsiPB pic.twitter.com/vMuSoR4U2z
In response to this, POTUS ordered a mix of kinetic and non-kinetic fires against these systems, but called off the kinetic ones, to keep things below the threshold of armed attack. The New York Times reported that multiple systems were targeted, they mention an additional attack;
An additional breach, according to one person briefed on the operations, targeted other computer systems that control Iranian missile launches.
Julian E. Barnes and Thomas Gibbons-Neff; U.S. Carried Out Cyberattacks on Iran
It would appear that US Cyber Command carried out this attack and it was their first since they became a full combat command. Given that they were able to attack what appears to be the command and control computers of a battery, this is effectively the suppression of enemy air defences and done in a way that doesn't put Wild Weasel crews or aircraft at risk. It is unclear if the attack was against a single battery, multiple independent batteries or against a battalion of batteries though, which could have wide-ranging consequences if the battalion command and control vehicle's systems were targeted;
The C2 unit provides communication between Sevom Khordad batteries. Furthermore, the C2 unit can connect other air defense systems of the Raad family, including Raad and Tabas, into a single air defense network. This allows to cover large area and targets can be engaged with a wide range of missiles from the cheapest Taer-1 missiles to the most capable Taer-2s. This adds the capability of facing different types of threats with different types of interceptors. In case of heavy jamming when even the X-band engagement radar can’t handle its duty, the C2 unit can provide an additional data link, connecting the system to electro-optical engagement systems of Raad batteries, in order to guide missiles toward targets.
Ehsan Ostadrahimi; Sevom Khordad - Medium-range air defense missile system
SEAD in Ukraine
By comparison, Russia has an option that the US didn't have when the US went after Iranian air defences. Russia can use things that go bang and boom.

If you compare these two events, you end up in a situation where when a commander is presented with options, to strike air defences, you have a Cyber team of at least 4, with a SIGDEV, SIGOPS, Signals Analyst, and Signals Exploitation to work on the project over months and they can't guarantee with certainty that their operation will go to plan. Or you can turn to the fighter jock who can basically guarantee that he will blow up the air defences with a 99% chance of success, within the next 24 hours.
The Other Form of Denial
As I mentioned previously, Information Warfare is a very old idea, but after Claude Shannon and before the invention of modern computing that gave us Cyber, the US was experimenting with traditional Information Warfare techniques such as Warfare like Electronic Warfare and Psychological Operations, but they didn't stop there, they were also trying to apply the same techniques in a more general sense.
One of the ideas they had was rather than go after the systems that gathered or processed data, they would go after the endpoints that analysed the data to form intelligence or to go after the endpoints that acted based on this intelligence such that there would be more opportunities to break the intelligence cycle, in the same way you can potentially stop cyber intrusions by breaking the Cyber Kill Chain. This idea was something the US called Command and Control Warfare or C2W.
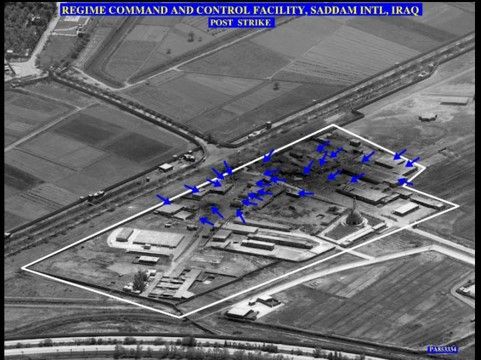
Command and Control Warfare
In the sense that most engineers and analysts in the Cyber Realm would be used to looking at the world, a perfect example of C2W would be where DNS requests are blackholed such that the C2 Server never gets to act upon infected machines or when a new piece of malware is analysed and Yara rules are distributed which can prevent a system from being compromised or detect an existing compromise.
While this is entirely possible in the military realm, there is more you can do. For example, if a state was to run a malware campaign, they could go after those that planned and ordered the campaign and the same goes for those that plan and order military operations.
During the Air Campaign of the First Gulf War, the Coalition Forces went after the C2 Systems of Iraq. This is something I previously wrote about in my first post on Information Warfare, but the cliff notes are that the Coalition Forces, particularly the US started with the KARI fibre optic network, and then the POTS network, leaving only the insecure microwave for Iraqi Armed Forces comms. While they could stop here, they also targeted the literal command and control systems of the Iraqi regime. They went after Saddam's generals.

C2W in Ukraine
Today, Ukraine is doing the same thing. They are using drones. First, they are using modified commercial drones to find Russian positions and forward coordinates to artillery units so that fire can be directed, possibly using the indigenously designed Kvitnyk laser designated artillery shell, as can be seen here, directing fire at a Russian anti-air system;
Amazing footage! An #UkrainianArmy drone detects a Buk M1-2 air defense system of #RussianArmy, its crew report its position to an artillery unit and they target it immediately using precision-guided artillery shells! pic.twitter.com/WRZLKmAtU9
— Babak Taghvaee - Μπάπακ Τακβαίε - بابک تقوایی (@BabakTaghvaee) March 16, 2022
They are using similar techniques to go after forward units rather than just sticking to more rear area units, as can be seen here being used as part of an attack on Russian formation;
UAV footage showing Ukrainian attacks on a Russian armored column in Brovary, including that captured T-72A tank. According to the audio, the regimental commander was killed. It appears it was a mix of Ukrainian artillery and tank strikes on the column.https://t.co/LemIgjQiOZ pic.twitter.com/x2tVSHPENa
— Rob Lee (@RALee85) March 10, 2022
They are also not limited to commercial drones, they have been purchasers of the Turkish Bayraktar TB2 too, to great effect to fire and direct laser guided weapons. The TB2 has specifically been used to target the command posts of Russian troops, in classic C2W fashion;
Last couple TB2 vids have looked like Ukraine has started hunting down Russian army command post. Possibly where the last couple generals and high ranking officers were killed pic.twitter.com/m5vl9DXzG2
— Lost Weapons (@LostWeapons) March 11, 2022
Ukraine hasn't been solely relying on drones though, they have also had significant help from the US as part of the JMTGU and Canada as part of Operation Unifier where among other items of training, they have been teaching Ukraine the finer art of Marksmanship. This isn't all the help they have been receiving on Marksmanship though as it appears that the CIA has opened the School of the Americas to Ukraine rather than just fascist dictators in South America, though I am significantly less fond of this kind of support given the history of the School of the Americas... So what has the impact of all of this been?
General's







Confirmed dead from top left to bottom right;
- Major General Vitaly Gerasimov - Chief of Staff and First Deputy Commander of the 41st Combined Arms Army
- Major General Andrei Sukhovetsky - Deputy Commander of the 41st Combined Arms Army
- Major General Andriy Kolesnikov - Commander of the Eastern Military District
- Major General Oleg Mityaev, Commander 150th Motor Rifle Division
- Lieutenant General Andrey Nikolaevich Mordvichev, Commander 8th Combined Arms Army
- Lieutenant General Yakov Vladimirovich Rezantsev, Commander 49th Combined Arms Army
- Major General Vladimir Petrovich Frolov, Commander 8th Guards Combined Arms Army
Colonel's and Equivalent's









Confirmed dead from top left to bottom right;
- Colonel Konstantin Zizevsky, Commander 247th Guards Airborne Assault Regiment
- Colonel Andrei Zakharov, Commander 6th Guards Tank Regiment of the 90th Guards Tank Division
- Colonel Sergei Ivanovich Porokhnya, Commander of the 12th engineering brigade
- Colonel Sergey Sukharev, Commander 331st Airborne Regiment
- Captain First Rank Andrey Nikolaevich Paliy, Deputy Commander Black Sea Fleet
- Colonel Alexei Sharov, commander of the 810th Marine Brigade
- Colonel Nikolai Ovcharenko, Western Military District's Deputy Commander of Engineer Troops
- Colonel Denis Kurilo, Commander 200th Separate Motor Rifle Brigade
- Colonel Igor Evgenievich Nikolaev, Commander 252nd Motor Rifle Regiment of the 3rd Motor Rifle Division
Lieutenant Colonel's









List
- Lieutenant Colonel Denis Glebov, Deputy Commander 11th Air Assault Brigade
- Lieutenant Colonel Yuriy Agarkov, Commander 33rd Motor Rifle Regiment of the 20th Guards Motor Rifle Division
- Lieutenant Colonel Ilya Yuryevich Pyatkin, Special Rapid Response Unit
- Lieutenant Colonel Sergey Savateev, Special Rapid Response Unit
- Lieutenant Colonel Aleksey Sharshavov, Commander of 171st Independent Air Assault Battalion of the 7th Air Assault Division
- Lieutenant Colonel Igor Zharov, Regimental commander of an unknown airborne unit
- Lieutenant Colonel Alexey Narzullaevich Khasanov, Deputy Commander 31st Guards Fighter Aviation Regiment
- Lieutenant Colonel Viktor Kuzmin, Political Officer 234th Guards Air Assault Regiment
- Warlord Vladimir Zhoga, Neo Nazi piece of shit, self professed War Criminal and Commander of the Sparta Battalion
And this is only me skimming over the ones that I can find good pictures of. As of April 28th, I have possibly another General killed, 19 Colonels and 33 Lieutenant Colonels. Astonishing numbers for any war since 1900, before you even consider the 46 Majors, 87 Captains and 147 Lieutenants, before you even consider captured, wounded, missing or arrested officers. And I can't imagine how many Senior NCOs are dead when they are the backbone of militaries, or what the true scale of death is given that some of the best numbers we have come from leaks like this, from Meduza;
In a now deleted VK post, the pro-Kremlin media outlet Readovka claims that Russia’s Defense Ministry stated at a “closed briefing” that it’s lost 13,414 soldiers in Ukraine *plus* another 7,000 who are missing. 116 sailors killed aboard the Moskva, with 100+ still missing. pic.twitter.com/jHx7lZi9WA
— Kevin Rothrock (@KevinRothrock) April 22, 2022
What is important that you take away from this is that Ukraine is systematically destroying Russia's capability to make and carry out strategic and operational plans. Ultimately we can't know the full impact of these deaths on Russia's fighting capabilities, probably until long after the war is over, but given how the war has progressed, it is clear that not just has the offensive not gone to plan, but that it has deteriorated as the war has dragged on, and not just because of the poor logistics.
Attacks that Corrupt
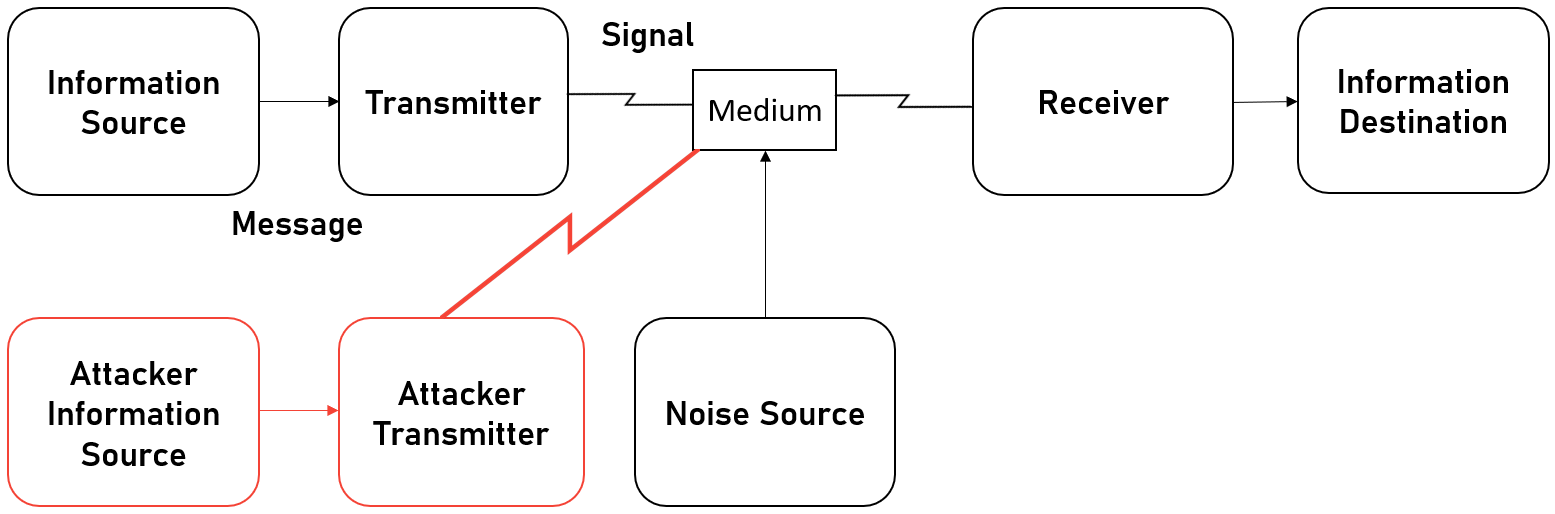
Operation Outside the Box
Operation Outside the Box was a raid on an undocumented nuclear facility, possibly a covert graphite reactor, in Syria by Israel in 2007. While the raid itself is interesting for multiple reasons such as the Iranian financing of the reactor, the deaths of multiple North Korean nuclear technicians or scientists in the raid or above all else the nuclear materials for the reactor came from North Korea, no, the most interesting part is how Israel used Electronic Warfare and possibly Cyber Warfare as part of the raid.
The raid required several Israeli aircraft to penetrate the airspace of Syria undetected to attack the facility. This happened in 2007 and the only nation in the world with stealth aircraft was the US with the F-117 and F-22 fighters and the B-2 Bomber. Israel used what they had, F-15s and F-16s for the raid along with electronic warfare aircraft. The attack took place in four major stages.
The first stage was to take off from Ramat David Airbase and fly up the Syrian coast until they reached the Turkish-Syrian border where they attacked a radar site at Tall al-Abuad in Syria. It was attacked with electronic warfare techniques, most likely jamming and then bombed with precision-guided bombs to take out the site. This created an entry point in Syrian air defence for the planes to penetrate the airspace. Once in the airspace, the really interesting part of the attack could begin.
Almost immediately, the entire Syrian radar system went off the air for a period of time that included the raid, say U.S. intelligence analysts.
David A. Fulghum, Robert Wall and Amy Butler; Israel Shows Electronic Prowess
Through a combination of jamming the HF and VHF communication links that are used for the command and control of air defences, other unknown forms of electronic attack from the electronic warfare support aircraft and the "penetration through computer-to-computer links", the aircraft were able to transit the airspace undetected and bomb the suspected nuclear reactor. It is unknown if the "penetration through computer-to-computer links" is a form of cyber warfare or if computers were linked via the HF/VHF network and were vulnerable to jamming or electronic attack.
It is believed that the electronic warfare support aircraft were able to create a spoofed image of the skies above Syria in what is called a "false sky picture" so that even though the Israeli aircraft were transiting the airspace, all the radar saw was the electronically manipulated image of the sky, that was what the Israelis broadcast and what they wanted the Syrian's to see.
U.S. aerospace industry and retired military officials indicated today that a technology like the U.S. developed "Suter" airborne network attack system
...
The technology allows users to invade communications networks, see what enemy sensors see and even take over as systems administrator so sensors can be manipulated into positions so that approaching aircraft can't be seen, they say. The process involves locating enemy emitters with great precision and then directing data streams into them that can include false targets and misleading messages algorithms that allow a number of activities including control.
David A. Fulghum; Why Syria's Air Defenses Failed to Detect Israelis
Essentially invisible to air defences, the Israeli aircraft proceeded to the target where commandos used laser designators to illuminate the target to be destroyed. With the facility bombed and destroyed, it was time for the aircraft to head home via the route they came, still undetected.
The vast majority of useful reporting on this comes from a fascinating article by David A. Fulghum, Robert Wall and Amy Butler called "Israel Shows Electronic Prowess" in Aviation Week which gives an account of the attack through the lens of electronic warfare.
The Ghost of Hostomel
Normally when people think about the Ghost of Somewhere in Ukraine at the moment, they think of the Ghost of Kyiv, the badass but unfortunately fictional story of the first Fighter Ace of the 21st Century. For me though, Russia's destruction of the An-225 Мрія, one of the greatest pieces of humanitarian equipment on Earth was a real gut punch. The Мрія could be used to transport a lot of things, but when you needed oversize cargo delivered somewhere in the world, in an emergency, it was the only platform that could be relied on and sometimes it was the only platform you could use.
After its destruction was confirmed, there were some incredible and heartwarming memes about how much it meant, not just to international nerds like me who think planes are cool, but to regular Ukrainians who knew it as this one of a kind, gentle giant that helped the world painted in a beautiful paint job that screamed Ukraine. it has even become a symbol you can buy a plushie of. But for me, the best example I have seen of its value is when someone spoofed false data into flight tracking sites that said the Мрія was running racetracks around Kyiv with the callsign FCKPUTIN.
Just because it shows up on flight tracking sites, doesn't mean it's real: Destroyed An-225, formerly the world's largest cargo plane, is showing on @flightradar24, callsign FCKPUTIN, circling Kyiv at 4,500ft.https://t.co/DGHdaexIZs pic.twitter.com/GZanwMnukm
— Peter Aldhous (@paldhous) March 11, 2022
The Scale of Propaganda
Just under a month before the Russian Offensive started, OpenFacto, a French language collective of OSINT investigators published an absolutely incredible article, that is in English on their Twitter. OpenFacto started looking into a collective of sites called InfoRos. Now InfoRos is a major news portal and it wasn't until 2021.
2021 was a bad year for InfoRos. The US Congress released a report on the unit behind InfoRos, GRU Unit 54777, there was a flurry of reporting by major American news organisations, some of which included focusing on Alexander Starunsky, which Meduza covered in detail here. But the really good stuff came from the Estonian Foreign Intelligence Service, where in their 2021 Public Security Environment Assessment, they dedicated nearly 5% of the report to the work of Unit 54777.
OpenFacto saw all of this and decided to poke around at InfoRos with some pointy sticks and see what fell out. Looking at the source of the pages, they were able to find a script, which had a dedicated nameserver that they could do a reverse lookup on. And wouldn't you know, they found not the 276 registered sites they claimed to be operating, but 1341;
We identified a distinctive snippet of its source code and performed a reverse nameserver lookup via the InfoRos server that hosted the first discovered sites. We found a total of 1,341 InfoRos linked-websites. Most redirected to a Russian city news portal controlled by InfoRos.
— OpenFacto (@openfacto) January 27, 2022
When they started looking at the sites, they noticed that 75% of them didn't exist before 2019 or that it was a local site for a city or region that was acquired by InfoRos, effectively buying fronts to distribute Propaganda. It's also interesting that while there is a distribution across the whole of Russia, the vast majority of sites are in areas that are in Europe.
We have identified a network of more than 1300 websites run by the GRU, targeting Russian speakers including domestic audiences. A thread 🧵...
— OpenFacto (@openfacto) January 27, 2022
And read our full report here https://t.co/UArqBocSb3 #Russia #Disinfo #OSINT pic.twitter.com/u2LZJOMJmY
The other major distribution of InfoRos sites are places where Russia has what it considers to be problem areas such as Ciscaucasia, where Russia has internal republics such as Chechnya and Dagestan, or neighbouring states like Georgia where Russia has fought wars to ensure that Georgia is a divided state with autonomous regions like Abkhazia and Adjara or breakaway states from Georgia such as South Ossetia. Not to mention Armenia or Azerbaijan who fought a war last year over Nagorno-Karabakh, or Turkey a NATO state fighting the Kurds inside Turkey, but also beyond their borders in Northern Syria and Northern Iraq.
The Quiet Corruption
While neither Borden nor Kopp discusses this form of Information Corruption, I believe that as professionals who work in Cyber should be aware that algorithms can be used to create a tailored view of what the world looks like. Now, this doesn't have to be malicious, Twitter for example changed up how they displayed tweets a while ago. Originally twitter would give users tweets as they came in, but over time they changed this so that twitter would show you popular tweets from your followers.
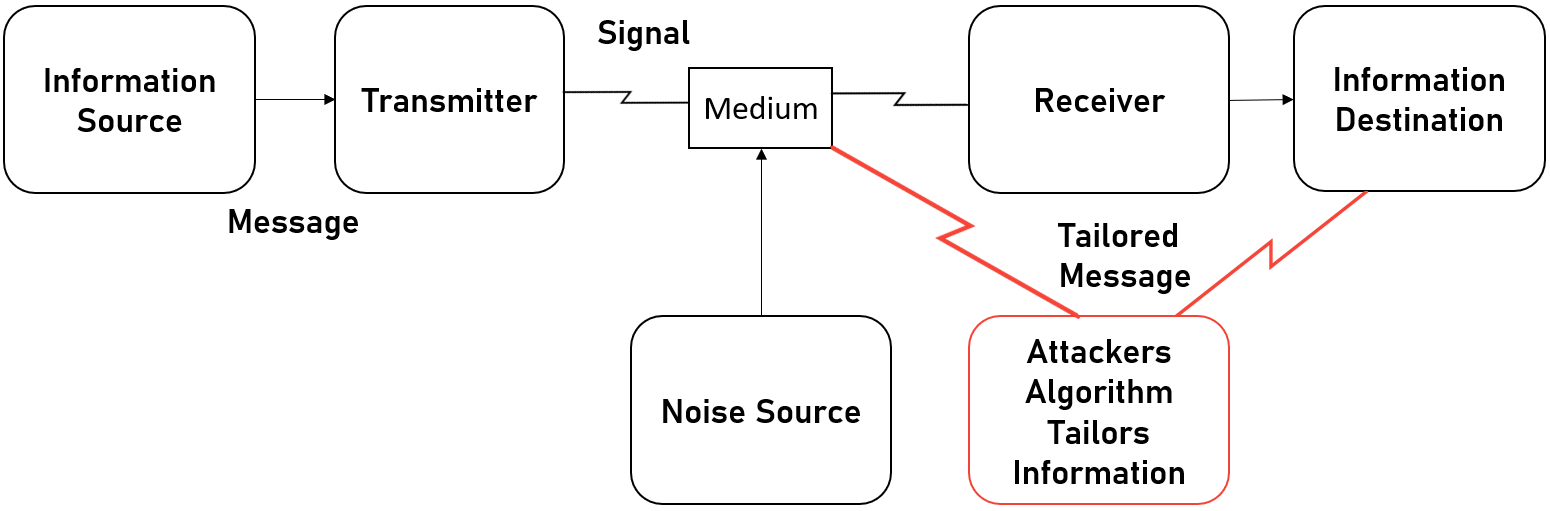
A less tasteful version of this tailored message would be the controlled implosion of the Evergrande company in China. While going through the controlled implosion, it was huge news here in the West with regular articles in various papers and segments on TV news shows. But inside China, it was a very different story inside the Great Firewall;
There are also kinda basic things, about you know, media, there was a New York Times piece, I think last week, about how Evergrande is everywhere in the foreign news and is nowhere in Chinese news and that means that, you know, Chinese people aren't maybe informed about what is happening. Obviously they know something about what is happening, but not to the extent, as they could if it was an open media.
Jen Patja Howell, Jacob Schulz and Katrina Northrop; The Lawfare Podcast: Katrina Northrop on the Evergrande Debt Crisis; 00:13:45
You can argue the merits and failings of limiting the reach of the story inside China and the ultimate purposes of doing it, but the censors at the Publicity Department of the Chinese Communist Party, or should I say the Propaganda Department of the CCP are making the active choice to not allow the media to report on the issues around Evergrande. You could also look at how Air-Moving Device has checked TikTok's API to see if certain phrases would trigger a manual review of a user's posts if they contained certain words. And how things are different when compared to Douyin, which is TikTok in China.
It should though be noted that this isn't limited to just China. Facebook for example has been shown to actively promote Holocaust Denial, and it is not alone with these problems. Reddit has repeatedly had similar issues, and more recently, Spotify has had this problem for throwing money at a moron who has had one too many head injuries and spends too much time JAQing off, writer Roxane Gay made a salient point;
I would never support censorship. And because I am a writer, I know that language matters. There’s a difference between censorship and curation. When we are not free to express ourselves, when we can be thrown in jail or even lose our lives for speaking freely, that is censorship. When we say, as a society, that bigotry and misinformation are unacceptable, and that people who espouse those ideas don’t deserve access to significant platforms, that’s curation. We are expressing our taste and moral discernment, and saying what we find acceptable and what we do not.
Roxane Gay; Why I’ve Decided to Take My Podcast Off Spotify
We can use algorithms for good and bad, it's just we have to make hard choices about what they should be used for as they can spread vile hatred, or be used to promote the good in the world.
Attacks that Exploit
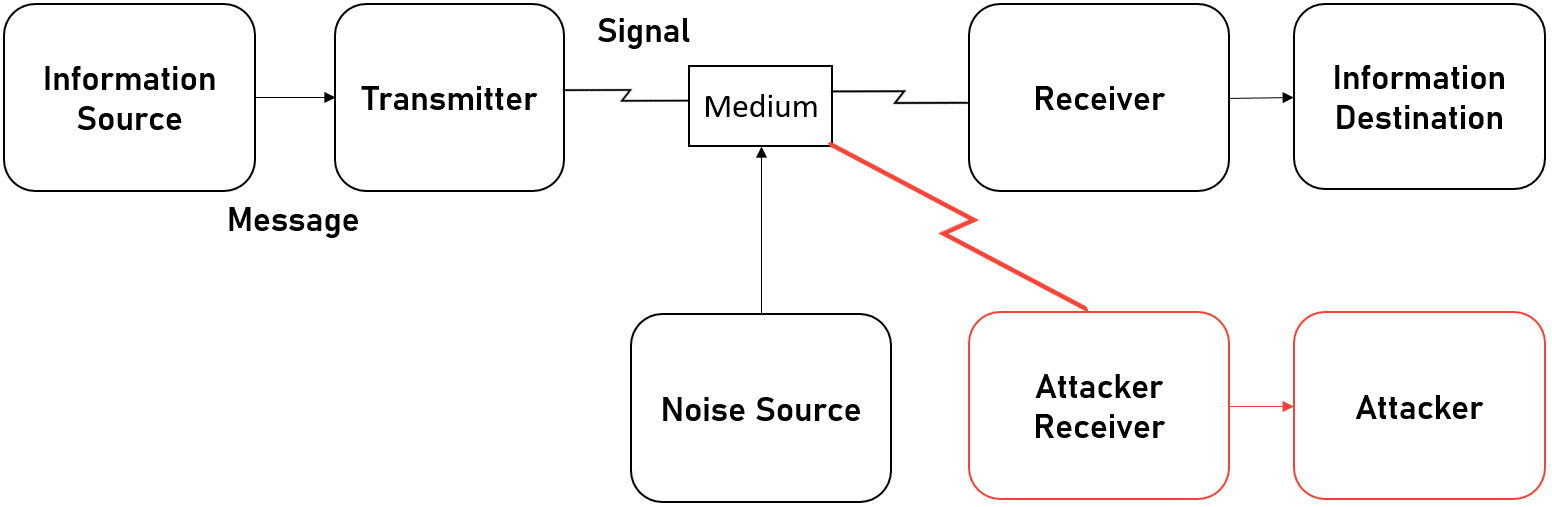
Spot The Army
During the talk, I needed a moment to grab a drink before my voice fell apart and rather than leave people to look at me take a swig of water, I'll give them something to do. I already wanted to talk about Electronic Exploitation and I had the perfect example because as a nerd who keeps an eye on the future of warfare, there are only two units worth watching, the US 780th MIB and the US 11th ACR.
Colonel Scott Woodward, who used to Command the US 11th ACR is active on Twitter and posts some really cool things there, while also actively engaging with people. He was asked about the efficacy of modern visible camouflage methods and he showed an incredible picture where the 11th ACR, with up to 1000 troops taking part in a concealment exercise, and he provided this incredible image of that concealed battalion;

This image is 2400x1600 so you can have fun downloading the png and going pixel peeping in your own time to find the whole battalion if you even can. But Colonel Woodward was using this to make a different point, that on a modern battlefield, it doesn't matter how good your concealment is, if all your fancy wireless electronics like the radio in the Humvee, or the smartphone on that guy over there, or this data linked computer in the tank etc are continually broadcasting data and making noise to be detected. Not to mention the growth of active radar emitters on the battlefield for active protection systems or for reconnaissance of your forward area, and it really stands out as a large Electronic Signature;
These were taken at the National Training Center, in California. Concealment will help you stay alive a little longer in the close fight.
— LXVIII RCO (@theRealBH6) May 8, 2020
What does your EW footprint look like is the larger question. If I can see you like this, it doesn't matter how much camo you have pic.twitter.com/EihBe4nEG3
11th ACR thought they were safe because at 2300 it was dark, they were spread out over 6 sqkm, and took the opportunity to resupply with trains but even with the best concealment efforts, his battalion was detected by its Electronic Signature at 12km's distance;
That’s exactly what it is. BN with trains hiding behind MG at about 2300. Thought they were safe cause it was dark. Picked me up at about 12 K with EW
— LXVIII RCO (@theRealBH6) May 8, 2020
Why Communication Networks Stayed Online
One thing that I and nearly everyone I know how looks like how Information Warfare impacts the Battlespace will tell you that the big lesson to have learned from First Gulf War is that if you want to decapitate a military's ability to fight, you have to crush their ability to command and communicate. Naturally, this would lead one to wonder why? And I think the best reason why is that they can exploit the intelligence, as seen in this video released by Ukrainian Intelligence;
This is a minute long intercept, which is one of several in that video. And this isn't the only intercept, the SBU has been publishing more like this on their YouTube channel. And this isn't the only reason why networks remain up. Both sides are using them to monitor the activity of each other. Not to mention how both sides have limited methods for C2, so are reliant on telegram channels for example to conduct operations at the tactical level.
Ukraine is not alone in doing this. Russia appears to be using similar techniques to target foreign volunteers. The story goes that Russia is using some surveillance equipment to find +44 numbers, but while phone surveillance isn't my area of expertise, this also doesn't seem like the smartest approach to me as Electronic Warfare suites have included IMSI Catcher-like systems for a long time and it would be easier to interrogate a SIM card for it's IMSI, which was a three digit Mobile Country Code or MCC that identifies the home of that device
And that is why these amateur fighters do not help anyone
— Carlo "Realism, Gedankenfetzen, and Rants" Masala (@CarloMasala1) March 19, 2022
British volunteer fighters may have triggered deadly strike on Ukrainian base after their phones were detected https://t.co/42afRMblxe
Even if you change your SIM Card to a Ukrainian one upon entry to the country, you aren't safe as all devices have an IMEI which identifies the network and country a phone comes from and it is possible to get the IMEI number of a device and identify the country it comes from. In theory, it is also possible to get the IMEI from a device connected via WiFi too, though this is a more complex proposition with several nuances. Ultimately it's a failure in Operational Security that comes not from the stupidity of a soldier, but a lack of understanding of the underlying technology and how it works, and normally one that western soldiers need not worry about as they have secure radios rather than phones. Any combination of these was used to identify the Ukrainian Foreign Legion members at Yavoriv above or at Kharkiv below;
Kharkiv: Russian Iskander missile targeting a Ukr base which housed infantry according to the Russian MoD. pic.twitter.com/UREpNUA1Dl
— OsintTv📺 (@OsintTv) April 2, 2022
Russia was also caught in the act by Ukrainian Intelligence relaying voice and SMS messages to high ranking Russian officers and other individuals in Ukraine. It's quite the find as it shows that Russia is targeting Ukraine across its entire spectrum of communications infrastructure.
1/5 Another significant capture in #Ukraine. Reported discovery today of a #SIMBox being used to relay Voice calls & SMS and other info to Russian forces (including top leadership of Russian army) & other individuals in #Ukraine. I will explain what this is and how it works. https://t.co/6MQAghOFqF
— Cathal Mc Daid (@mcdaidc) March 15, 2022
Now, none of this is to say that networks haven't gone down. Networks have physical points of presence in the real world while sending data around the cyberz and while there is a degree self healing in BGP for fibre networks, on mobile networks, only 5G can self heal so if a GSM tower is hit or has a cable cut or antenna damaged, it is down and needs an engineer to go out and fix it. NetBlocks has done an amazing job of keeping track of these outages, in areas around the world, such as this drop in connectivity in Kharkiv on the first day of the war;
⚠️ Update: #Ukraine's second-largest city #Kharkiv continues to take the brunt of network and telecoms disruptions, leaving many users cut off amid scenes of destruction as Russia targets the region. Kyiv is currently less impacted by outages.
— NetBlocks (@netblocks) February 24, 2022
📰 Report: https://t.co/S0qJQ7CJD3 pic.twitter.com/FxgN1bHV3m
The Other Reason Why Communication Networks Stayed Online
There has been an absolutely gargantuan effort by engineers at telecom companies, including putting their own lives at risk to maintain network connectivity. When Ukrainians say Героям слава or Glory to Heros, I know they mean the soldiers on the front line and the EOD techs who make places safe by removing unexploded ordinance, but I can't help but think about the Heros who keep the state's phone and broadband networks up. They allow us to document Russia's barbarism in Mariupol and their atrocities in Bucha, but also to see all that is good in the world like those rescuing people's pets from near the front lines or people being helped to safety and families being reunited.
Radio Use And Intercepts
In western militaries, all communication is done via secure radio that handles voice, video, data, and satcoms. These systems are also moving towards integrating AR/VR and biometric data which is just wild. Generally, these are systems like the L3 Harris Falcon family of radios or something wild like a Persistent Systems MPU5 which are do everything systems.
Russia was supposed to be moving in this direction with the R-187 Azert SDR radio, which on paper looks pretty cool! Though they have been mired in a long running corruption scandal where 6.7 billion rubles were stolen. The gist of the story is that the radios were to be manufactured in Russia, using Russian sourced components, which makes a lot of sense, but somewhere along the way, they were sold to the Russian military as overpriced junk, with 60 suppliers from European countries as well as China, Malaysia and Taiwan. Not to mention that the final assembly allegedly took place in China and the software comes from an unknown company, known just as Elvis.
It is at this point that my new favourite Twitter account, The Radio Research Group, comes into the story! These people have basically been looking at radios for the whole conflict and identifying them, such as some below;






Some examples of The Radio Research Group's work on Russian forces includes;
- Never before seen radios
- The aforementioned R-187 Azart
- Baofeng civilian radios which you can buy for 100 bucks on Amazon
- SATCOM devices among others
- A Chechen soldier with a pile of radios
- And they identify all of them
They also have identified Ukrainian radio systems, though to a lesser extent as one would imagine they care a hell of a lot more about Ukrainian operational security than Russian operational security.






Some examples of The Radio Research Group's work on Ukrainian radios include;
- Some US made Hytera radios
- Motorola XPR radio with an interesting antenna
- Motorola FRS walkie talkie
- Ukrainian's also using Baofeng radios
- Capturing Russian Azart radios
- And my personal favourite, using Anti Drone Weapons, which are basically fancy handheld radios
The big thing I love though that The Radio Research Group did is identify all of the unencrypted comms that Ukraine and Russia were using. This gave David, my Signals Officer an idea! So he went looking for, and found Russian tactical communications and recorded them, which my Cryptographic Linguist Victor translated, and I can now present to you;
Intercept 1
Translation:
A: Yes, I can ??? you, ???
B: Ryazan I’m ??? (portrait?), over
A: ??? (Portrait?), I’m Ryazan, over
B: Ryazan, [we are] working on the 16th ???
A: Continue to work on this route, everyone stay alert [via radio], I’m Ryazan
B: Roger that, over
Intercept 2
Translation:
A: I’m Ryazan, over
B: I’m Uragan, over
A: Uragan, I’m Ryazan, over
B: How… can we… transmit data, or receive it? over
(bleeping)
C: Ryazan, I’m Geyzer, ???
A: Geyzer, Geyzer, I’m Ryazan, over
C: I’m Geyzer, will clarify how Uragan can pass data and receive it, over
Battlefield Shaping
Battlefield Shaping is the process of preparing the terrain for war. When people generally think about that, they think about the Gulf War in 1991 when Coalition Forces destroyed important targets in Iraq and ensured they owned the skies before commencing ground offensives. When we look at Information Warfare, and in particular Cyber Warfare, we see a similar thing. We can exploit intelligence gathered and launch attacks so that advances can be made but people tend to forget about the other aspect, the aspect of defence.
In the run up to the Russian offensive in Ukraine, there is an incredible untold story, that we have only gotten little glimmers of, of the defensive efforts to protect Ukraine's cyber infrastructure from Russia. It started as best I can tell in November of 2021 when US Cyber Command deployed Cyber Mission Teams (CMT) to Ukraine. CMTs are combinations of troops and specialist contractors who can go forward into the field and perform operations from those forward locations.
These CMTs systematically performed a statewide Threat Hunt, going through the cyber infrastructure of Ukraine and removing malware left, right and centre from various state bodies such as Ukrainian Railways and the Border Police. These CMTs also worked on a small budget of just 60 million dollars. This effort in destroying the prepositioning Russia had spent so long building up, as part of the Subversive Trilemma, that Russia's capacity was reduced. This could be one reason why we have seen so many DDoS attacks and Wipers, though that could also be because they are effective, particularly Wipers.
The linked article also mentions that Ukraine's police was the victim of a DDoS and one of the CMT partner companies, Fortinet, was able to have the US Department of Commerce cleared the funding of a "virtual machine" that is used to counter DDoS'.
Next in January, we saw a little advisory from the NSA titled NSA Issues Recommendations to Protect VSAT Communications. VSATs or Very Small Aperture Terminals are small satellite dishes, such as those that give you satellite TV or satellite broadband. The NSA advisory doesn't say much about what exactly the threat is, just that if you use one, you need to up your security game as there are threats to the terminals. In retrospect, it is clear that the NSA was aware that something like the Viasat Kerfuffle could happen or that they knew directly that it would happen, but were unwilling to divulge this information lest it burn Sources and Methods.
Also in January, Dragos' dropped a regular Knowledge Pack, which included a detection/detections of INDUSTROYER/CRASHOVERRIDE malware, which was used to take down one fifth of the power grid in Kyiv for a period of an hour in 2016. As well as this, the March Knowlege Pack included detections in February for INDUSTROYER/CRASHOVERRIDE and BlackEnergy, which was used to take down parts of the power grid in western Ukraine in 2015, effecting 225,000 customers for a period of 3 to 6 hours.
This variant of INDUSTROYER/CRASHOVERRIDE is being dubbed by CERT-UA as INDUSTROYER2. It's unknown how different it is from the original, for example, I have heard from some sources that they are radically different and should be called different names entirely and from another set of sources that there are a lot of similarities. I do know for sure that the wiper is different in operation and thus has been dubbed CADDYWIPER and that the payloads that execute on ICS systems were compiled on the 23rd of February 2022, hours before Russia began offensive operations in the early morning of the 24th of February. Though note that information on the campaign is still limited. The CERT-UA alert discusses that 9 substations did go down and that there is a set of Linux components which have not been recovered.
Here is the alert, authored by Ukraine's Computer Emergency Response Team, that had previously been shared with international partners about Russians "successfully" hacking Ukraine's power grid. https://t.co/8CNfwFhD9z pic.twitter.com/32ISNqqc3n
— Patrick Howell O'Neill (@HowellONeill) April 12, 2022
In April, Mandiant, along with FVEY making a rare joint statement, publicised the discovery of INCONTROLLER, malware that targets Industrial Control Systems (ICS). While attribution isn't specifically given, the targeting profile of the malware in North America, Europe and particularly Ukraine as well as the malware taking pointers from previous experiments like TRITON/TRISYS, and Russia's history with ICS malware with HAVEX, BlackEnergy3, INDUSTROYER and VPNFILTER, it's reasonable to assume that the malware came from Russia, something that Mandiant highlight with their graph of the nexus of Russian malware targeting ICS systems.
INCONTROLLER is comprised of 3 parts, TAGRUN, CODECALL and OMSHELL. TAGRUN scans for OPC Servers, enumerates them, brute forces credentials and allows the malware to read and write OPC Tag Values. OPC Tags are stores of data values like Data Access, which provide real time data on a sensor, such as the specific rate at which a motor is turning or Alarms and Conditions, such as a boolean value to check if a condition has been reached. There is also an extension for it called Historical Data Access, which as you can imagine provides historical, rather than real time data. While the majority of what TAGRUN does suggests recognisance, it should be noted that manipulation of OPC Tags could mask changes made by other pieces of the malware.
CODECALL is a framework that operates over the Modbus protocol to directly communicate with the Programmable Logic Controllers (PLCs) and contains modules that can identify Schneider Electric systems, connect to them, load and execute files and execute commands that can for example crash systems. OMSHELL is a modular framework used to identify and connect to Omron PLCs that allows it to enable telnet and use this access to execute arbitrary files or commands and to connect to a backdoor to execute arbitrary files or commands.
Mandiant list three attack scenarios. Scenario 1 uses OMSHELL and/or CODECALL can be used to crash PLCs to shut down operations. Scenario 2 uses all of the modules to reprogram controllers to sabotage a process. And scenario 3 has the capability to disable PLCs, such as the Omron NX-SL3300 Safety Instrumentation System (SIS), as TRITON/TRISYS did for the Schneider Electric Triconex, to cause physical destruction of industrial machinery.
And then we really started to see the Wipers... Ohh god did we see the wipers... Microsoft released a report on the number of engagements they had taken part in, from February 23rd until the 8th of April, they had 237 separate cyber operations against organisations in Ukraine, only two of which were INDUSTROYER2 with CADDYWIPER...
In January Microsoft MSTIC discovered WisperGate/WhisperKill which was a wiper that overwrote the Master Boot Record (MBR) leaving a message to pay the ransom.
Then ESET found HermeticWiper/FoxBlade and IsaacWiper/Lasainraw in February. HermeticWiper does the same overwriting of the MBR but it also has a worm component to spread across the networks it is on and also has a ransom component to hide its activities, though SentinalOne notes that the malware is poorly written and not just loudly generates events in the Windows Log, but also probably slows down the wiper component.
IsaacWiper is significantly less sophisticated and just overwrites the first 0x10000 bytes of a disk and then attempts to wipe all files on a given disk by writing random bytes over them, but does this in a single program thread so it would take basically until the sun engulfed the earth to erase a disk. I know that's a little over exaggerated, but it's really poor form from the Russians.
This is just scratching the surface of the offensive operations and defensive efforts that are ongoing as I haven't for example talked even talked about all of the wipers, such as SonicVote/HermeticRansom, DesertBlade, FiberLake/DoubleZero or all of the other operations such as MicroBackdoor or Armageddon, which is responsible for 4 separate campaigns in 2022 alone. But at some point, I have to stop collecting information and call a post done.
The other thing to note beyond how small of an effect that offensive operations have had, is something I want to dig into a lot more. Why did the defensive efforts work so well? Yes Ukraine has a well resourced and trained pool of defenders at the SBU, CERT-UA and the State Service of Special Communication and Information Protection of Ukraine (SSSCIP), but lots of states have similar things but that doesn't stop for example the UK getting Army recruits. Maybe the existential threat that Russia poses to Ukraine is one hell of a motivator when it comes to winning the war in the 5th Domain?
I do though wonder, what if Ukraine did what Estonia did? After the Bronze Night, Estonia really reckoned with what did happen and what could have happened if things had gone worse. The Ministry of Defence drafted one of the first National Cyber Security Strategies, anywhere in the world, in 2008. In 2011 this was handed over to the Ministry of Economic Affairs and Communications, making it a Cabinet Level responsibility with major top level buy in from the Government. Estonia also has the Cyber Security Council of the Security Committee of the Government, which is a separate body spread across the Government and government organisations, whose sole task is to implement the strategy and gauge its successes and failures.
Successive governments have also made sure that Cyber Policy gets all of the attention and funding that is needed, which has resulted in the creation of bodies like the Estonian Information Systems Authority to supervise compliance with cyber security standards, including if necessary, using door kickers to gain entry to facilities to ensure that critical infrastructure is defended correctly. It also houses bodies like CERT-EE, which along with CERT services, also provides some rad tools like baseline security profiles for information systems, X-Road and easily found education on Cyber Security for citizens. And this is just the civilian cyber defence too. I haven't talked about the role the military plays nor the work of Estonian Intelligence who are some of the best in the world, not to mention the Estonian Foreign Intelligence Service provides yearly Security Situation Reports that are packed with things happening in Cyber Space and essential reading in my humble opinion. NATO's CCDCOE has a fun write up on the detail if you're interested in it.
Ukraine has followed this with the SSSCIP reporting directly to the President. SSSCIP has CERT-UA there which does incredible work protecting the information infrastructure of Ukraine. Ukraine and policymakers are also acutely aware of the dangers posed by Cyber as they have been a bit of a Cyber Testing Range for Russia over the last decade, not to mention 8 years of war, and as this is the case, Ukraine provides all of the publicity needed to keep mind share with the general public, as well as mountains of funding. All this stands in stark contrast with Ireland where... Well, let's say I follow this kinda stuff closely and I have no fucking idea what's going on...
Where Is The Cyber Pew Pew!?
As a wrap up slide, I had a conclusion thing at the end with what I wanted people to take away, and nothing really has changed since then;

Cyber is still limited, it still takes a lot of effort and investment and there are still other weapons available and these weapons can be MUCH more effective. But I left the politics out of my BSides talk. The other takeaway I want to take away is;
- Путин — хуйло (Putin huul-yo) Putin is a dickhead 🖕 and;
- Перемога Україні (Per-em-ohh-a uu-cry-een-a) Victory to Ukraine ✊
Acknowledgements
Cheers to members of the Irish Cyber Security and Privacy Discord for giving me the chance to do a trial run of the talk before BSides, in particular, Don for the idea, Michael and Philipa for organising the talk and Liam for helping me get the flow of the talk just right with amazing feedback! To Ronan for being a sounding board to bounce ideas off of over the last year plus, to Owen for the seed of the idea on Ukraine following Estonia on strategy and finally to Schrodinger for keeping me up to date with the latest threat intel on the situation in Ukraine.
To the Wonks in the ACWP Slack generally, because they are rad and savage craic, but particularly Tinfoil for helping me test the video streaming and remembering stuff I had forgotten, aminal for patiently explaining EW like I'm a 4 year old because it's witchcraft, Jack for help with stuff that didn't end up in this post but was invaluable to my thinking, Microbiote for some graphics, David for his signals intercepts, Sinan for helping with Turkish linguistics and details on the TB2 system as well as video of it in action from Ukraine, and Bill for being a treasure throughout by organising the invaluable debriefs we're having to hone our skills. Finally to dman for being an invaluable stream of OSINT that keeps me in the loop
Finally, thanks to Victor for translating some Russian for me as my Cryptologic Linguist. To the guys from BSides, particularly Antonio for saying I should do a talk on this kinda stuff when we met at IRISSCON21 and Anne-Marie and Kim for pushing me to talk to Antonio! And Paul because while my initial talk didn't make it past the CFP, Paul wanted me to talk about the Cyber War, I wrote a whole new talk in a few weeks, based on the ideas Don gave me fueled by the opportunity Paul gave me.
