Update 02/07/22: Video source updated
The post I published on Information Warfare is going to be the subject of a talk at Ireland's National Cyber Security Conference on October 7th, 2021. As this is the case, I would like to tailor a little of that talk to some of the threats and risks to Ireland and our information environment. It's a shame that I only had 30 mins to lay out the issues as this post will probably end up taking longer to read than to watch the video because of the scale of the topic, but this is the nature of conference talks.
Video of the Talk
Some of the aspects that I discuss in the talk are slightly different as talks come across better with pictures so I may in future talk about The Gulf War War in more picturesque terms as I found a bunch of cool information in both text and picture form that wasn't included in the previous post as it does a really good job of getting the picture across of how some aspects of the attacks worked.
Finally, I used Col. Andrew Borden, USAF (Ret.) Degrade, Deny, Corrupt and Exploit framework to look at threats and risks to Ireland, so instead of giving the background to this framework, I will just jump in, assuming that you have seen the talk or read the previous post and discuss. But first, I want to mention one of the major points I try to make. The Cyber-Physical Impact.
The Cyber-Physical Impact
The thing to understand about Information Warfare is that an idea like hacking or the concept of Cyber where you limit one's thinking to digital systems, rather than the broader spectrum of systems that computers interact with such as Operational Technology or the RF Spectrum. Computers control and interact with systems that do much more than the computer itself. As Bruce Schneier once pointed out;
As the chairman pointed out, there are now computers in everything. But I want to suggest another way of thinking about it in that everything is now a computer: This is not a phone. It’s a computer that makes phone calls. A refrigerator is a computer that keeps things cold. ATM machine is a computer with money inside. Your car is not a mechanical device with a computer. It’s a computer with four wheels and an engine…
Part of Bruce Schneier's tetimony to the House of Representatives, Subcommittee on Communications and Technology, Joint with Subcommittee on Commerce, Manufacturing, and Trade, Committee on Energy and Commerce; Understanding the Role of Connected Devices in Recent Cyber Attacks, pp 27
In every aspect that I can conceive, or that has occurred previously, an Information Warfare technique has involved the meshing of some form of manipulating the inputs and outputs of a computer to achieve an objective. This could be the returns of a radar, the varying levels of Chlorine used to make clean drinking water or listening to RF outputs of systems to locate them in a physical place. This is where, at least in part, the future of combat lies, because when everything became computers, so computers became everything.
The merging of the physical and digital realms opened up several threats that we have not fully comprehended the damage that could be done at this crossroads. In medical devices alone, in 2019, there were two advisories from CISA, in the US, whereby the sniffing of, and sending of data over RF, would allow attackers to send commands to the medical devices. One was in insulin pumps and the other was in pacemakers and while these would require an attacker to be roughly within Bluetooth range of a given medical device, if this unlikely scenario were to unfold, an attack could put either system into a state such that its use could be life-threatening.
Fundamentally, the concept of networking is about connecting two different systems in different geographic locations. This could be as simple two computers right next to each other all the way up to how Ireland has various networks, linked together that are connected to various countries all over the world creating a network of networks. These disparate systems all require physical infrastructure to link them together. Even wireless technologies have associated microwave towers. Even space-based systems require physical, on the ground to function, be they ground stations or launch pads to get into space in the first place.
I worry that this fundamental fact is something that has not entirely sunk into the minds of professionals and policymakers, for example, if you were to read the National Cyber Security Strategy, there are exactly four mentions of the word physical;
... These compromises can take the form of theft or destruction of data or money and the physical disruption or destruction of services or infrastructure. ... (pp 3)
... Recent years have seen the development and regular use of very advanced tools for cyber enabled attacks and espionage, and, likely for the first time, the physical destruction of Critical National Infrastructure by cyber enabled means. ... (pp 13)
... Lastly, at the top of this pyramid, are those State sponsored entities, usually military or security organisations, seeking to use network and information systems to conduct operations ranging from the exfiltration of data to the destruction of physical infrastructure. ... (pp 16)
... They could make laws to prohibit parties using their territories for illicit purposes or activities, and they could use physical borders as a means of defending against external threats. ... (pp 16)
National Cyber Security Strategy 2019-2024
While in this limited context, these seem like reasonable statements to make, and the fourth is a simple statement of fact, in that the internet has no borders. In the full context of the quotes, things are a little less reasonable. The first is a statement from the Executive Summary. The Second is the context for the first and while it is in a section about the Strategic Risks that Ireland faces, it calls the internet 'a-spatial' which is a patently false statement and goes on further to mention that there is an 'arms race' between Great Powers and that they have destroyed physical infrastructure, as best seen by Stuxnet and the German Steel Mill attacks. The second point is a contradiction in terms.
The third point is about risks to Critical National Infrastructure, is about the skilled and resourceful nature of APT's to physical and references the previous work of APT groups, hardly an in depth understanding of the two realms, and to be honest, this makes a lot of sense, security is an intangible idea after all, and arguably one that the public has a certain apathy for.
Degrade
Data can be degraded either by delaying it until its usefulness is reduced or by destroying it in full or part. For example, the use of concealment is an Attack measure (degradation) against the collection task. The use of jamming to reduce the Capacity of a communications channel (thereby delaying transmission) is another example.
Col. Andrew Borden, USAF (Ret.); What is Information Warfare?
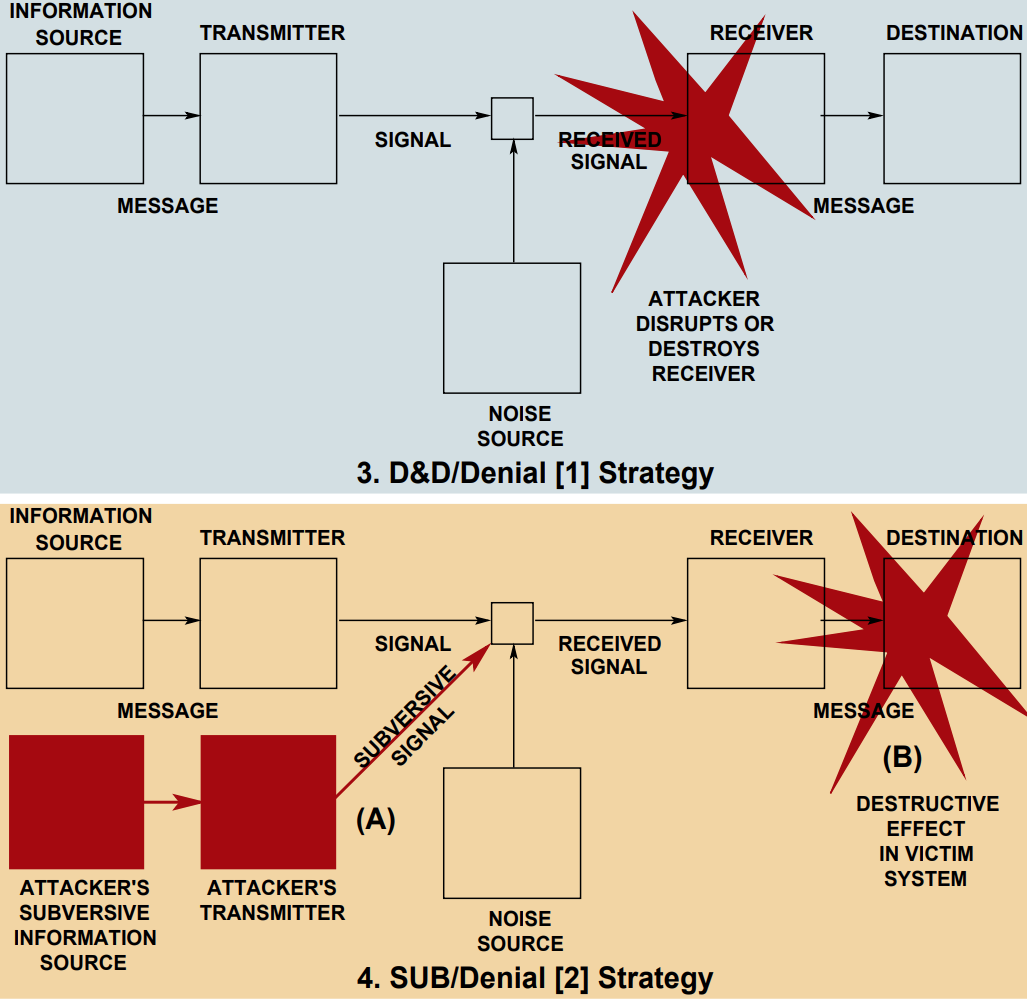
It should though be noted that according to Claude Shannon's Mathematical Theory of Communication, Information is not collected, stored, moved or used to reduce uncertainty, Information is generated in the course of reducing uncertainty and this reduction in uncertainty is measured in bits. As this is the case, information cannot be destroyed, as the transmission of information is in bits per second, noise can be introduced to degrade the rate of bits per second in which a transmission is received. Claude also developed a diagram that can be used to visualise this process;
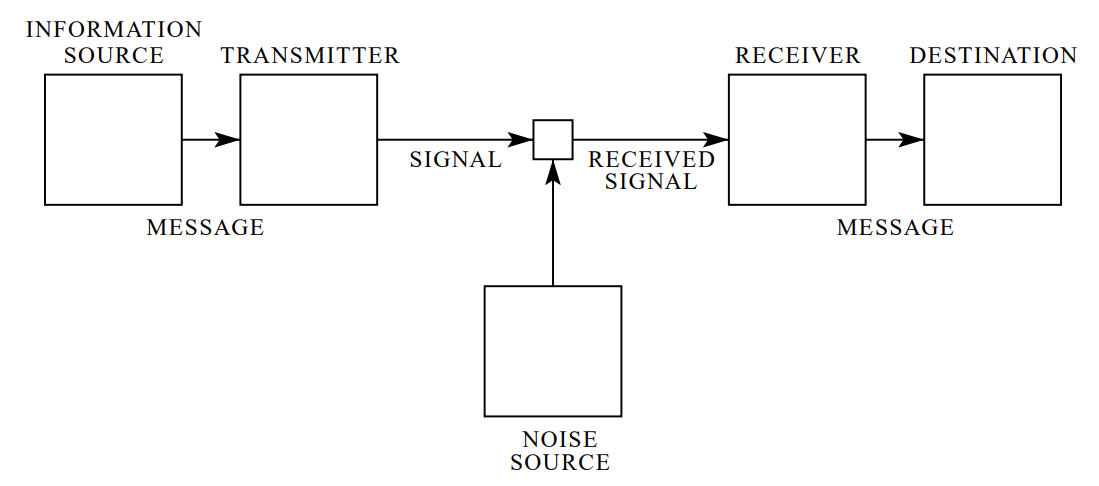
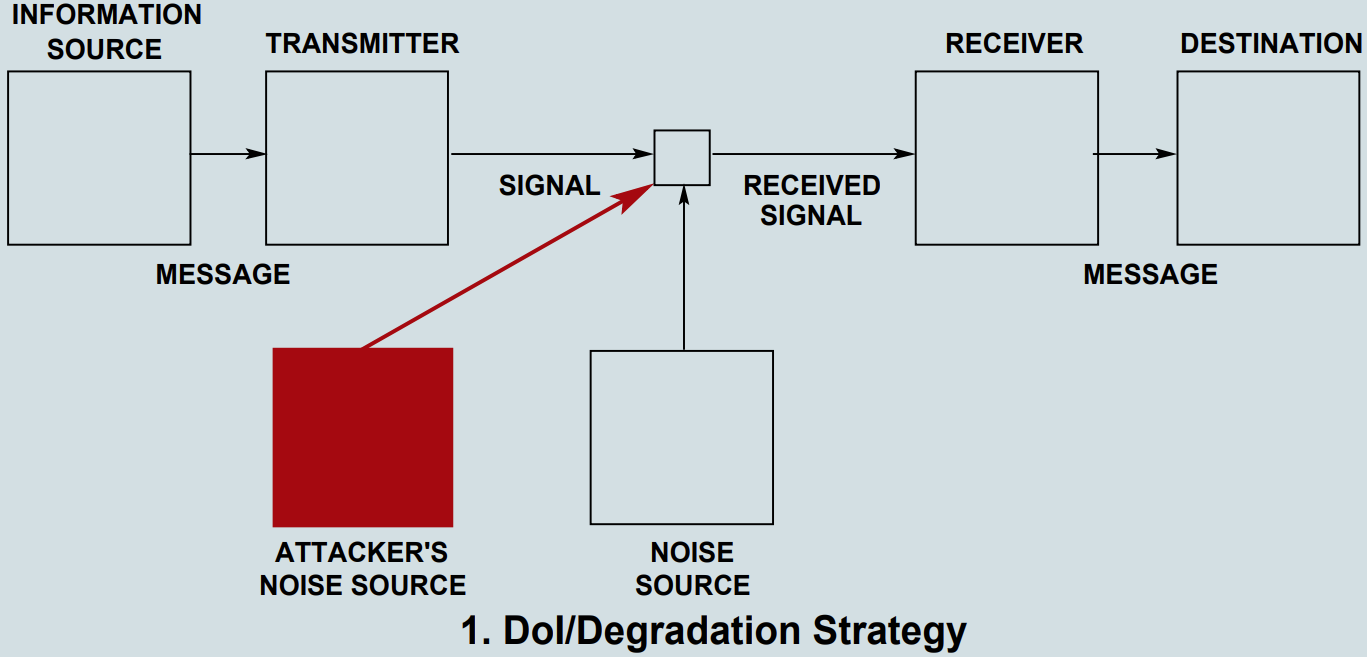
Something that I discovered along the way is that two professors wrote a paper on the nature of Information Warfare in evolutionary terms and came up with a set of diagrams to visualise Information Attacks, which I will include
Sea Lines of Communication (SLOC’s)
SLOC's are the primary maritime based economic routes between ports, they are the highways of the sea basically. Throughout time they have been essential in both peacetime as part of commerce, for example, the vast majority of products coming from China to Ireland come via container ship that makes multiple stops along the way, dropping off and taking on cargo before heading to the next port, finally arriving at Dublin Port with products to be sold here in Ireland.
In times of war they have been particularly important too, in the post-classical era, we have seen privateers attempt to capture prize ships or loot them of their goods so that the economies of your adversary would hurt. In World War I, the UK used the Grand Fleet based at Scapa Flow to Blockade the German state and attempt to starve it, leading to things like the Turnip Winter. By the time of World War II, Germany had learned from this and took its Unrestricted Submarine Warfare concept from WWI to the next level by beginning the Battle of the Atlantic to starve the British, which turned into a decisive battle for the Allies to secure their SLOC's in the North Atlantic and the North Sea.
By the time of the Cold War, NATO forces expected to be pushed back from the Fulda Gap towards the Franco-German border, something that the Warsaw Pact forces expected to take approximately 7 days.
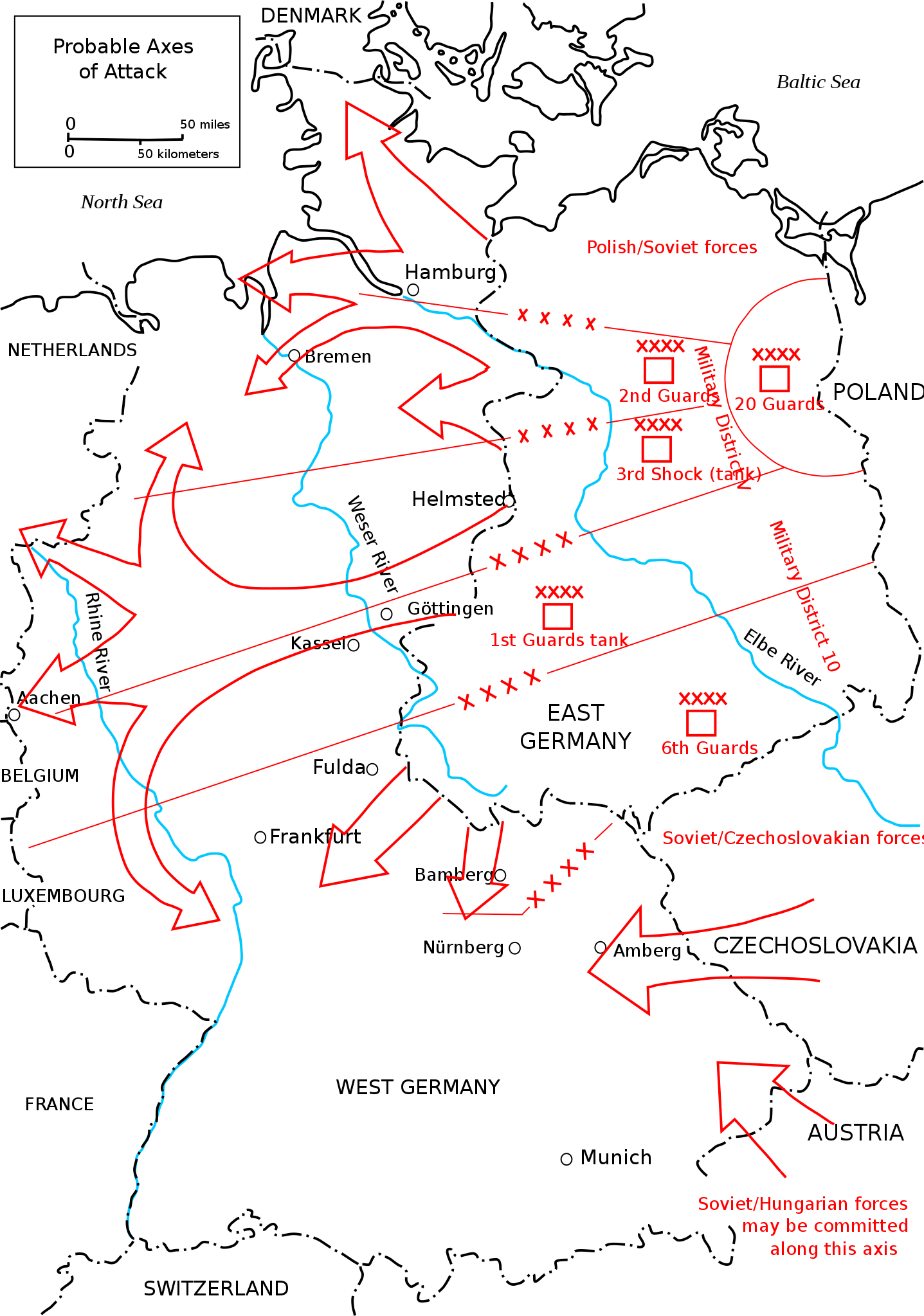
In this timeframe, NATO forces would be expected to hold out for as long as possible for the US to mobilize and to arrive in Europe via massive sealift and airlift operations. The Warsaw Pact naval forces, particular that of the Soviet Navy and its massive submarine arm would spend most of the first 7 days of this conflict attempting to disrupt the sealift operation and to an extent airlift operation. One of the main plot points in Tom Clancy's Red Storm Rising beyond AMERICA, FUCK YEAH! is about US and Soviet operations in the North Atlantic to resupply and disrupt, respectfully, operations there.
The thing I want to get across though is that in 1992 when the VADM John McConnel became the Director of the NSA, he was shown a map of SLOC's and a map of Submarine Fibre Optic Cables. Over the course of his tenure between 1992 and 96, he effectively revolutionized the NSA, taking it from an organisation working on intercepting, decrypting and analysing microwave signals to one moving towards an organisation working on not just Submarine Fibre Optic Cables or even fibre optic cables in general, but to one working more generally in the space of Information Warfare, particularly via Cyber means.
Looking at Ireland
Ireland is a uniquely interesting case to look at, not just because I am Irish and that I live in Ireland, but because Geography is Destiny, we are at the crossroads between the US and Europe and the UK and because of it, a lot of subsea maritime infrastructure exists here, a recognised fact going back to 1858 when the first transatlantic cable was laid from Kerry to Newfoundland. And because of our past, we are a state that speaks English, but also now the only one in the European Union. At Slandail 2020, I took note of what the then CEO, and now Chairman of IBM UK and Ireland said that Ireland's economic success is built on; Ireland being a 'stable, democratic, safe and secure, rules based society'.
We have leveraged our geography and our past to create a so-called Knowledge Economy that is an appealing investment proposition for foreign direct investment. The Government's strategy across my entire life and for more time before that, going back as far as that of T. K. Whitaker, is to use this platform to attract multinational technology, pharmaceutical and financial companies to come to Ireland, to invest in Ireland, backed up by our dubious corporate taxation policy.
The subsea maritime infrastructure I mentioned, today are Transatlantic Submarine Fibre Optic Cables. There are 18 total Transatlantic Submarine Fibre Optic Cables that cross the North Atlantic. Five of them make landings in Ireland but more importantly, 17 of them transit our Exclusive Economic Zone or EEZ. Exclusive Economic Zone's are defined by the United Nations Convention on the Law of the Sea, where they are defined as;
Article 55
Specific legal regime of the exclusive economic zone
The exclusive economic zone is an area beyond and adjacent to the territorial sea, subject to the specific legal regime established in this Part, under which the rights and jurisdiction of the coastal State and the rights and freedoms of other States are governed by the relevant provisions of this Convention.
Article 57
Breadth of the exclusive economic zone
The exclusive economic zone shall not extend beyond 200 nautical miles from the baselines from which the breadth of the territorial sea is measured.
Article 55 & 57; United Nations Convention on the Law of the Sea
Essentially it creates an area, beyond our 12 nautical mile territorial waters, out to 200 nautical miles where Ireland has a sovereign right to, for example, all economic activities in the area or conservation of marine wildlife in the area. This means that we have privileges as a state to conduct activity in that area that no other state has without our permission. So what does this picture of EEZ covered in Submarine Fibre Optic Cables look like? Well, I created a composite image of our EEZ from the Irish Government and Submarine Fibre Optic Cable data from TeleGeography;
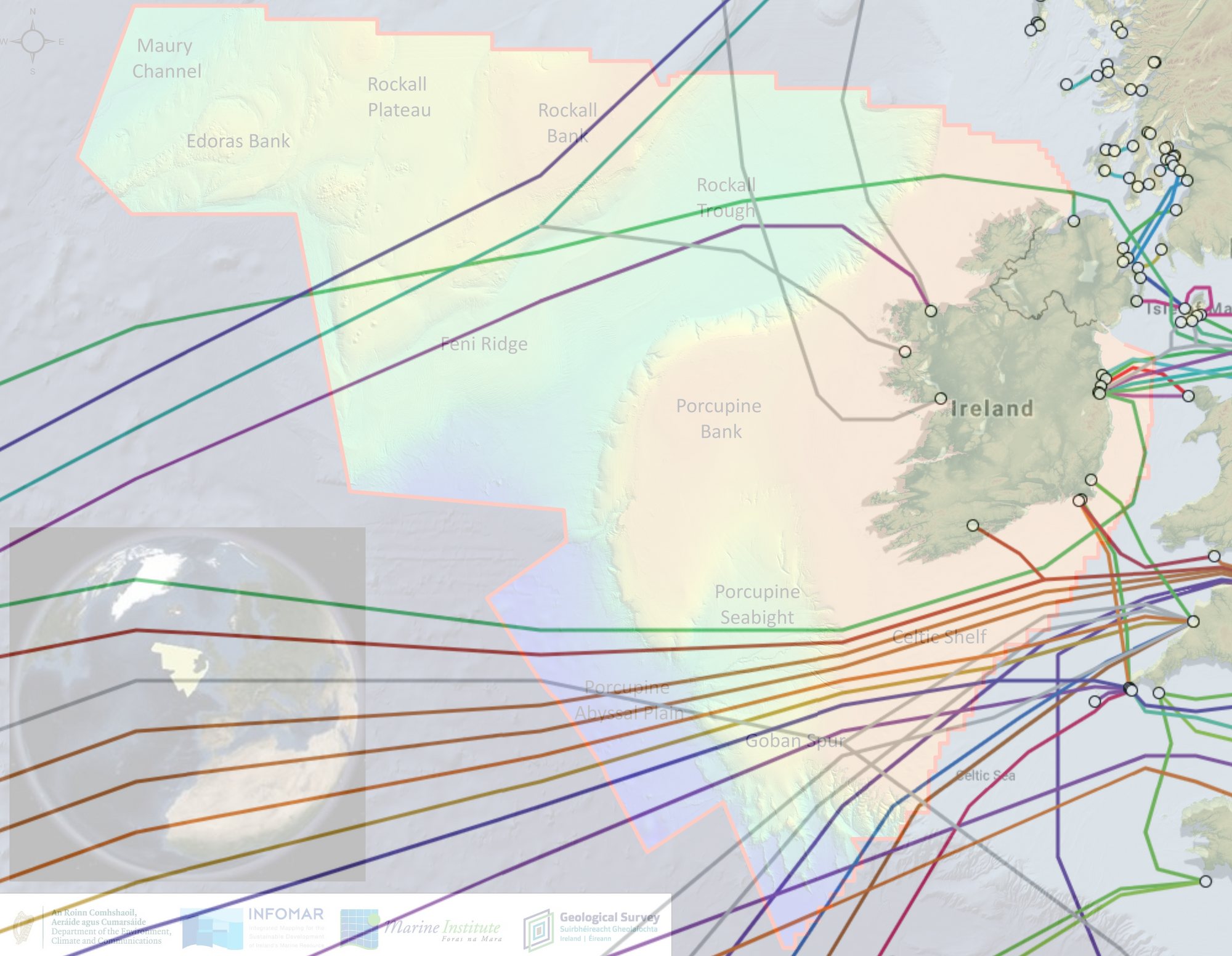
Normally, this is the part where I would state that we have some duties, as we do with our Neutral Status where we have to enforce our Neutrality, and we do have duties, but those duties are not to protect these cables from physical attack or deter cables from being tapped by various means on land at landing points and this is where the major risk opens up for us.
If we think in the traditional threat modelling methodology used in Cyber Security of identifying assets, identifying vulnerability in the assets, the threats to this asset and the risk being the non zero chance that something bad will happen and the threat will succeed in attacks, and mitigations that can be applied to these assets, how do we look at these SLOC's?
Lt. Shane Mulcahy, a Staff Officer of the Naval Operations Command Centre, wrote maybe the most important paper in the history of the Defence Forces Review. In his paper, he gives a brief history of the importance of Submarine Fibre Optic Cable, as well as some of the issues and risks associated with them before going on to forge a strategy based on political efforts in updating the United Nations Convention on the Law of the Sea to more reflect the importance of these cables and to ingrain protections for them in International Law, but also in two paragraphs, lays out the major risk that Ireland faces as a state;
Some will argue that given the international effort required to secure the vast North Atlantic maritime domain in which we reside, our part as a small, ‘neutral’ nation, should neither be significant nor central. It is worth remembering however that as an Island that has successfully grown a digital economy on a fragile maritime infrastructure, Ireland may have the most to lose.
Considering western preoccupation with weapons of mass destruction in previous decades, it seems almost comical to find that a ship’s anchor could now be described as an ‘existential threat’ to national security and prosperity. With no alternative to using these undersea cables, Ireland must become proactive towards securing the maritime domain on which our contemporary, digital society depends.
Lt. Shane Mulcahy; Patrolling Below the Horizon: Addressing Ireland’s Awareness of our Maritime Geospatial Domain; Defence Forces Review 2019
Not just is Lt. Mulcahy succinct, but he also lays out the key importance of Submarine Fibre Optic Cables to the state in that we have grown a 'digital economy' off of them and that our 'digital society depends' on them. I am not doing Lt. Mulcahy's article justice though as he talks about other issues beyond human damage such as earthquakes, subsurface landslides and 'curious sea-life'. It's worth reading in full.
This sentiment is also something that Dr. Cathal Berry, a TD for Kildare North and former Army Ranger Wing intelligence officer and 2IC is acutely aware of, but lays out in much better terms;
Tens of thousands of financial transactions are sent on these cables every hour along with communications. People think ‘the cloud’ is in the sky but it’s really in the bottom of the sea,
Jophn Mooney quoting Dr. Cathal Berry (TD); Navy called in as Russians suspected of targeting undersea internet cable
Before looking at mitigations, we understand the asset, the breadth of the risks from small to existential, accidental to deliberate, what is the threat here?
The first is relatively simple, espionage. The tapping of the cables is not covered by the United Nations Convention on the Law of the Sea, but it is something that occurs and just as I was working on this talk, GUGI Yantar showed up off of the Irish coast. Yantar is a vessel of the Russian Navy's Main Directorate of Underwater Research where it is titled as an 'oceanic research vessel', a naval euphemism for spy ships.
Traditionally these ships are effectively the mothership of a submersible or a number of submersibles that they provide a lifeline to as missions are conducted on the deep sea. This is the same idea as RV Knorr deploying DSV Argo to discover RMS Titanic in 1985. It should be noted that the Mothership does not have to be a vessel like Yantar or Knorr, as you can deploy submersibles from submarines too, as best seen in Tom Clancy's The Hunt for Red October where USS Dallas deploys the DSRV or the Losharik that that is deployed from the Delta Stretch. These submersibles can be used to put things on, or retrieve things from the seabed. These things are equipment such as fibre optic cable taps, or passive sonar arrays such as the SOSUS network, but can do as much as is needed as long as work on the seabed is needed as this artwork from H I Sutton shows;
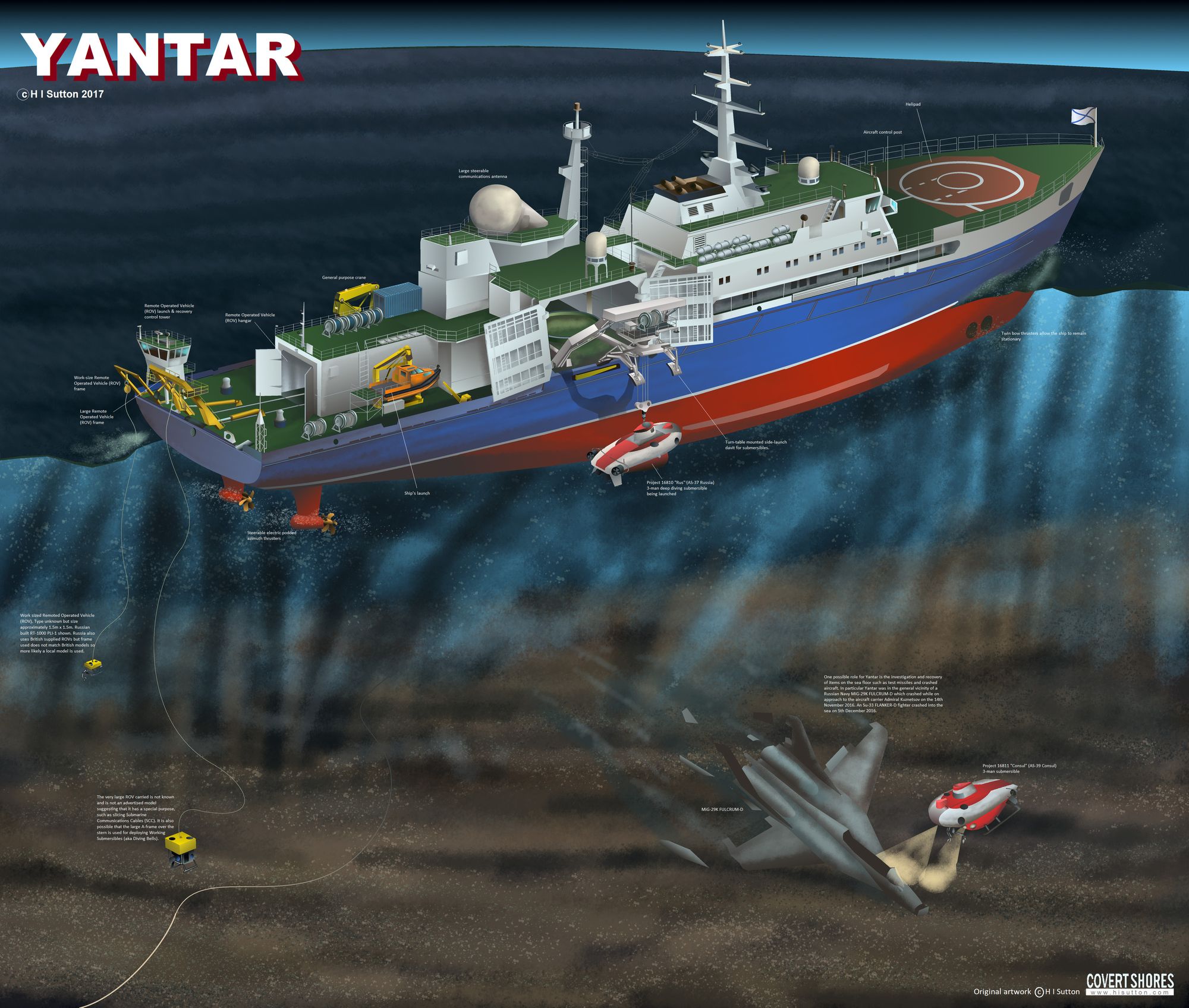
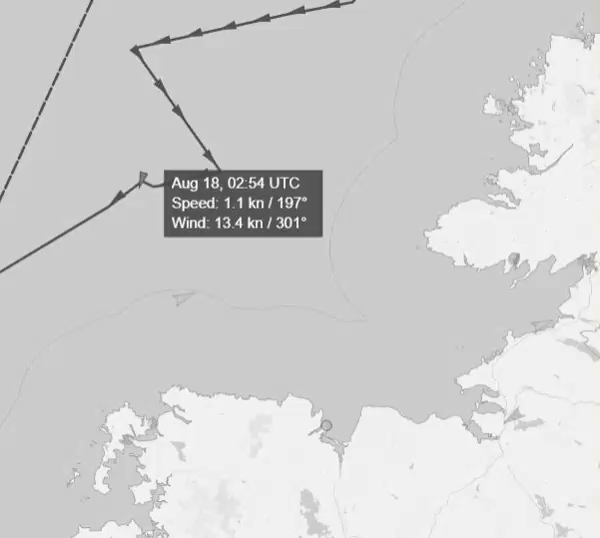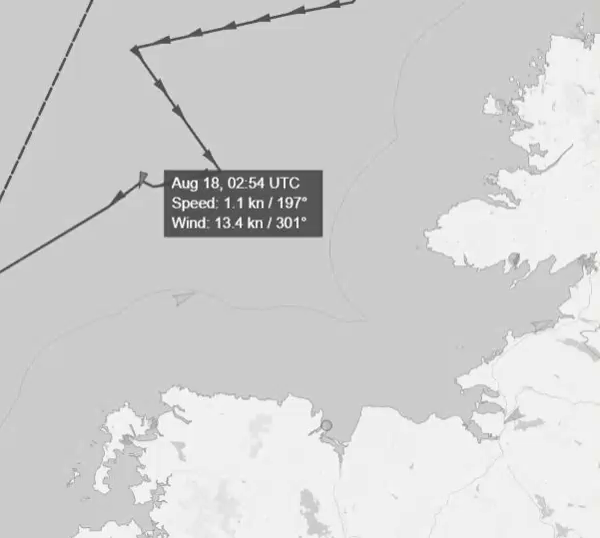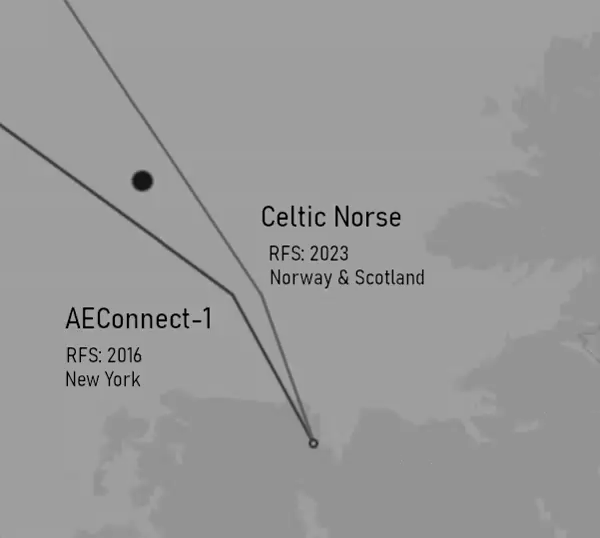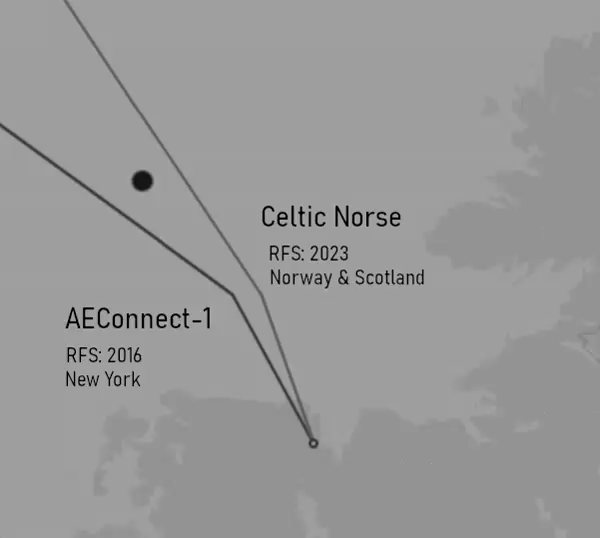
In the talk, I referenced a tweet from @The_Lookout_N, but I want to highlight the work of a fellow Wonk, @dbmee who was tracking Yantar well in advance of most others in the OSINT community. He created a gif that he tweeted that included both the track the ship had taken before The_Lookout_N's tweet and with knowledge of where she weighed anchor and did stuff, he looked at it in relation to the nearby Submarine communication cables that leave from somewhere near Ballina in Co. Mayo;
These types of activities can pose an unusual problem as espionage generally under International Law is a bit of a grey area that remains mostly unregulated and the practices of espionage, most of the time anyway, are dealt with by the principle of Consent by Silence. Under the United Nations Convention on the Law of the Sea, as long as they are in compliance with Articles 88 through to 115 and remain outside of Irish Territorial Waters, they have total freedom of action and navigation within the law, as long as there is no evidence of illegal activates. And since espionage is not economic activity, the Russian Government does not have the notify the Irish Government of the ship's arrival or activities in the area.
Yantar and other oceanic research vessels such as the French ship Dupuy de Lôme, or my personal favourite, the USNS Waters (T-AGS-45) which does 'ocean engineering', is rumoured to be used for work such as that undertaken by the Hughes Glomar Explorer of Project Azorian fame. These types of ships are not the only threat though, submarines are a larger issue.
Between 2016 and early 2020, there were persistent rumours that Russian submarines were operating off of the coast of Ireland, sometimes the rumour was that of an Akula class nuclear powered attack submarine, and other times it was that of a Kil0 class diesel eclectic attack submarine, was doing stuff off of the coast of Ireland. This stuff was always in relation to Submarine Fibre Optic Cables with the narrative of either working on taps of these cables or worse, severing these cables in the event of war. Beyond rumours, in open sources, there was very little concrete to be said until one day, Russia made a regular penetration of Irish Air Space but left its transponders on, and we got a track of their activity;
Now according to @MIL_Radar, the TU-142MR broke away from the patrol at the West coast of Ireland, the TU-142MK continued on towards to the South West of Ireland. Loitering just above where transatlantic subsea fiber optic cables route to and past Ireland. pic.twitter.com/he9kATf2yr
— Robert Gilbey (@RobGilbey) March 9, 2020
In the tweet, you can see the map shows that the aircraft took an unusual circular flight path while it was off the coast and as Rob notes, it is associated with its Trailing Wire Antenna used for VLF, but also ELF, communications with submarines below the surface, and this was one in one of the most densely populated regions of the world with Submarine Fibre Optic Cables.
Mitigating this could be difficult for a number of reasons for us. First of all the tactics traditionally used to deter these kinds of activities could be unpalatable to the Irish public, for reasons that will become clear, but also because a lot of these tactics would be extremely difficult or in one case impossible for us to accomplish.
Starting with the impossible, the most common technique is Herding. Herding is where you have advance intelligence that such an operation is going ahead by an adversary submarine. Knowing that this is the case, you send out your own submarine to patrol the area and attempt to locate the adversary submarine. When you have it located, tailed and identified as an adversary submarine, you place a call to a nearby Anti Submarine Warfare ship to close the range and have that ship begin to hound the adversary with sonar and perhaps weapons. Once a submarine knows they are found they will get out of there quickly. You can see this process done quite well, in an overdramatized fashion in this YouTube video.
This is clearly impossible because we don't have a submarine to herd with but also for a second reason which is that only one ship in the entire fleet of the Naval Service is equipped with a sonar system to detect anything below the surface of the sea, the flagship LÉ Eithne. She is equipped with the Plessey PMS-26 sonar system which was designed by a company that hasn't existed since 1989. Beyond LÉ Eithne, the most recent records of this system use, that can find records for, are of its use in a Danish Corvette class built between 1978 and 1980 and a Nigerian Corvette built between 1977 and 1980, both of which have been out of service for nearly 20 years. In 1984 when LÉ Eithne went into service it wasn't that out of date. It would be the only ship currently in the world operating such a system, if it was fitted of course.
Given that we lack sonar systems generally in the Naval Service, you can imagine that another option would be to install sonar systems on existing and future ships, and you would be right, though a number of issues present themselves, primarily the chronic underfunding of the Defence Forces in general. Given that none of our modern ships have sonar, it clearly isn't a priority for the Dept of Defence and even if it was, and we could get the sonar systems, we can't put ships to see because we lack the personnel to do so, which is part of a larger issue around pay and retention generally in the DF, but acutely in the Naval Service where the Government can't even be bothered to pay bonus' for ships going to sea short staffed.
To better detect and surveil surface vessels such as Yantar would require more patrols from the Naval Service, which runs into the same issues as before but the gap could be partly filled by the Air Corps running patrols in the CN-235 or the C295's which will replace them, but the fleet is stretched with two CN-235's so running regular patrols with just two C295's would also be a stretch. There are also staffing issues in the Air Corps so running these plans in high tempo operations with multiple crews may also lead to issues.
Deny
To Deny means to deny completely by a direct attack on the means of accomplishment. The use of a High Energy Laser to blind or destroy an electro-optic sensor is an example of denial by direct attack. Another example is a virus that destroys operating systems in a computer used to do Situation Assessment.
Col. Andrew Borden, USAF (Ret.); What is Information Warfare?
Air Control
Normally when someone considers the concept of Information Denial, we look at how an adversary denies you access to your Information Environment, but Ireland has placed itself in an interesting position and somewhat curious position of denying itself information.
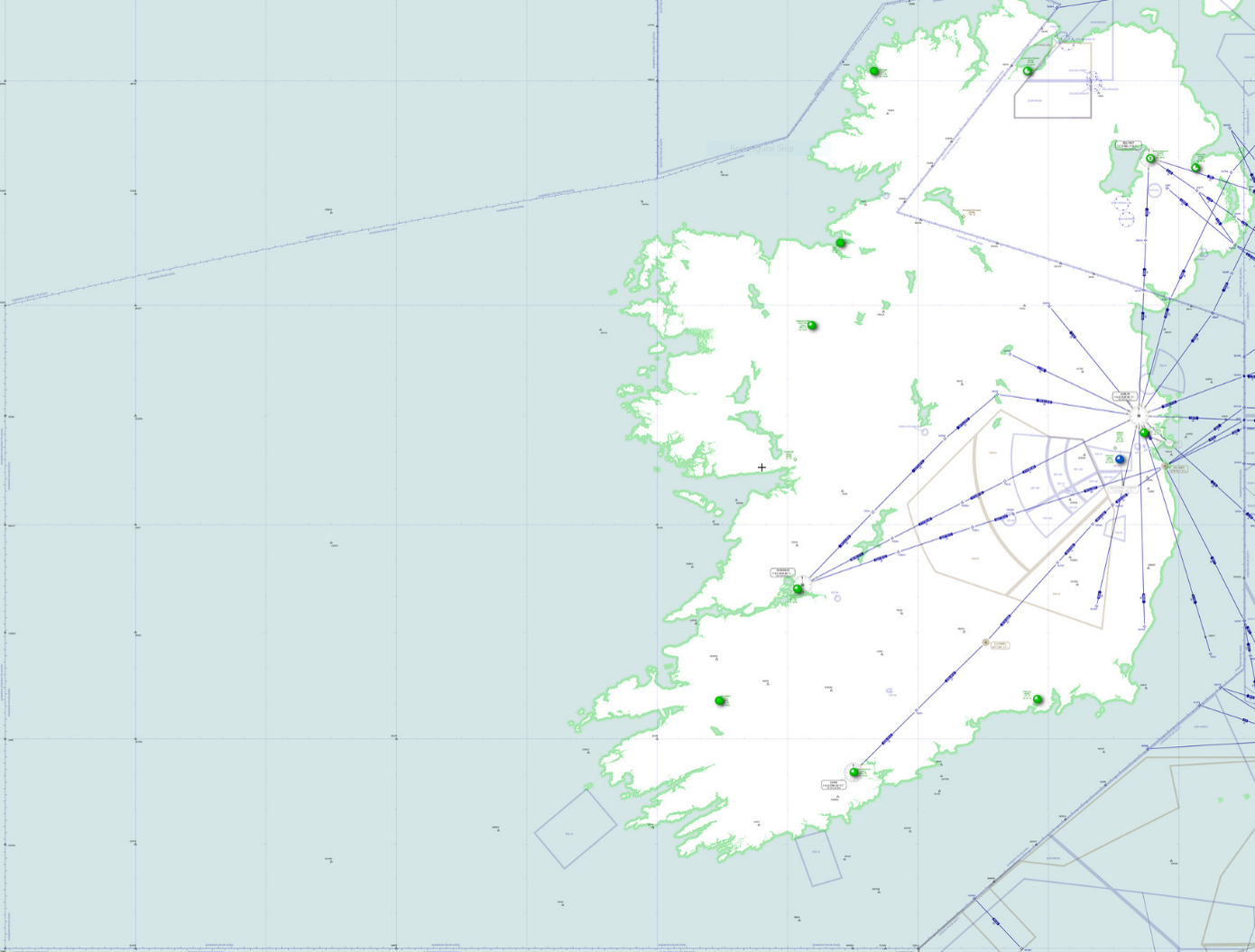
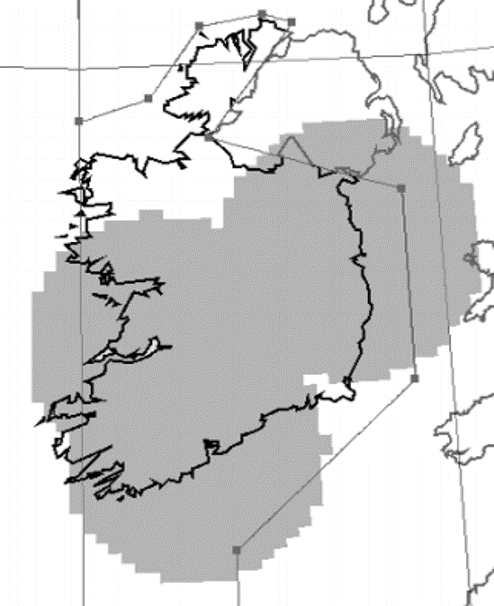
Ireland has a HUGE area of airspace to monitor. If you look at the below image of Shannon Flight information region or Shannon FIR for short, you will see most of the area of responsibility of Irish Air Traffic Control where you will be in direct contact with the Traffic Controllers and you will be vectored on the waypoint or route you need to take towards your destination.
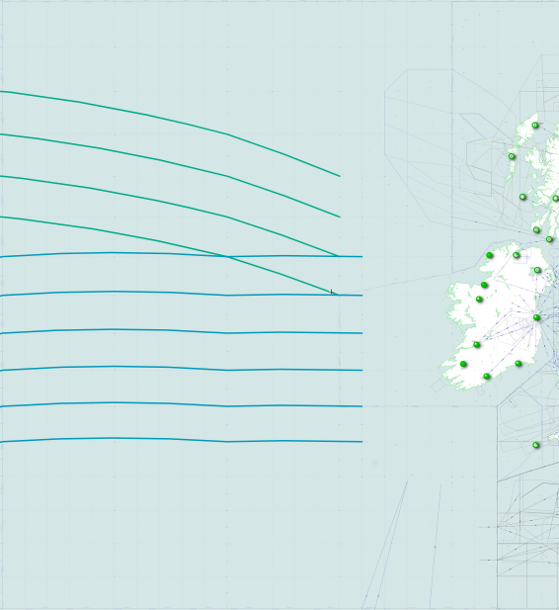
While this is a rather large area, it does not tell the whole story. Ireland and the UK also operate a second region called Shanwick Oceanic Control Region or Shanwick OCR for short, which is a gigantic tract of the airspace that covers 2.3 million square kilometres that goes from the north of Spain, out to the Molson-Guinness line which it follows north to south of Iceland, back towards just west of the Faroe Islands, down towards and around Shannon FIR and back to its starting point.
Somewhere between 1000 and 1500 flights per day use this air space, primarily a set of routes called the North Atlantic Organised Track System. There are four westbound routes, Alpha to Delta, and five eastbound routes, Uniform to Zulu, which you can see in the below image as green and blue respectively.
So one would imagine that an area of this size, with this many flights traversing though it would be very heavily surveilled and to an extent, you would be right. See the thing is that there are two different types of aircraft surveillance. The first is what you find at apps like Flightradar24 or FlightAware, or websites like ADS-B Exchange, where the aircraft broadcasts data or Air Traffic Control interrogates the transponder for data. When the aircraft is broadcasting data, it is doing so using a technology called ADS-B, which can be detected using ground-based sensors, or if the aircraft is equipped with satellite communications, using space-based sensors.
When Air Traffic Control interrogates the Transponder for data, the transponder will broadcast certain data depending on its operating mode. Mode A transmits its IACO code, such as AE01D8 for Cobra Ball 1, Mode C which transmits the IACO code and the altitude of the aircraft back, and finally, Mode S which transmits the IACO code, altitude and can allow for data exchange between Air Traffic Control. Mode S also has an 'Enhanced Surveillance' variant which allows for the track of the flight, ground speed, indicated airspeed and vertical rate etc, for more accurate tracking. This is what you see in things like Flightradar24.
And if you look at Shanwick OCR coverage from Eurocontrol, you'll see this amazing map of the area where there is huge coverage by both ground and space-based sensors;
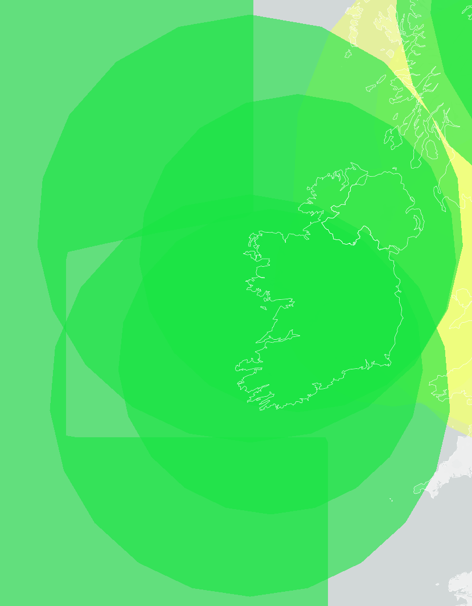
The problem with the ADS-B is that for many reasons pilots can turn it off as they choose and because it is dependant on the internal navigational systems of the aircraft, if it goes off, Air Traffic Control loses all positional information about that aircraft. This is why you might sometimes see it called Secondary Surveillance Radar. The secondary part is because Air Traffic Control is unable to interrogate the aircraft when the transponder is turned off. They can of course use Primary Radar, or what people think of with radar, the spinning thing on top of structures, rather than the homemade antenna, that I made out of plumbers pipe I have hanging off of my dads shed.
As well as their being legitimate reasons for you to need to turn off the transponder, there are also illegitimate reasons such as we saw during 9/11 where hijackers turned off the transponders as part of their hijackings. As well as this a large chunk of military aircraft, for obvious reasons, don't come with transponders or by default have them off. This means that Air Traffic Control is dependant on being able to interrogate these aircraft by Primary Radar to gather track, altitude and identification data. Ireland has a minor issue though, while we do have Primary Radars but we only have terminal radars which are used on approach to airports. Also we only have them at three airports; Dublin, Shannon and Cork, even though we have 10 airports across the country, and these Primary Radars don't even cover the entire island and airports such as Donegal Airport aren't covered either.
We have for years talked about rectifying this situation by getting a long-range radar to better cover Shannon FIR and parts of Shanwick OCR, as well as to interrogate military aircraft, particularly Russian aircraft, as they make regular penetrations into Irish airspace, but as of yet, we still do not have this radar. If you want to see how regularly Russian aircraft make such penetrations, fear not, we have a not so secret defence pact with the British to defend our airspace, and if you want to see how regularly they occur, a wonderful OSINT nerd has a webpage to keep track of RAF QRA's or Quick Reaction Alert's so you can track these things after the fact, or follow his twitter accounts and get the news as it comes in.
When these QRA's are launched, generally you will find that the RAF will send out two Typhoon's and also launch a Voyager A330 MRTT Tanker for support, and occasionally an E-3 Sentry AEW.1, though they are going out of service fast and old since they are based on the Boeing 707 and are soon to be replaced with the and E-7 Wedgetail based on the 737NG. The Tanker and AWACS aircraft will sit in what are called Orbits, pre-mapped circles on a flight chart, where they can sit and wait for the Typhoons to refuel or where the AWACS can scan a large area of the sky with its massive radar, so much so, that if you look at the area around Ireland, there are so many orbits that it accounts for 22% all of these orbits in the UK.
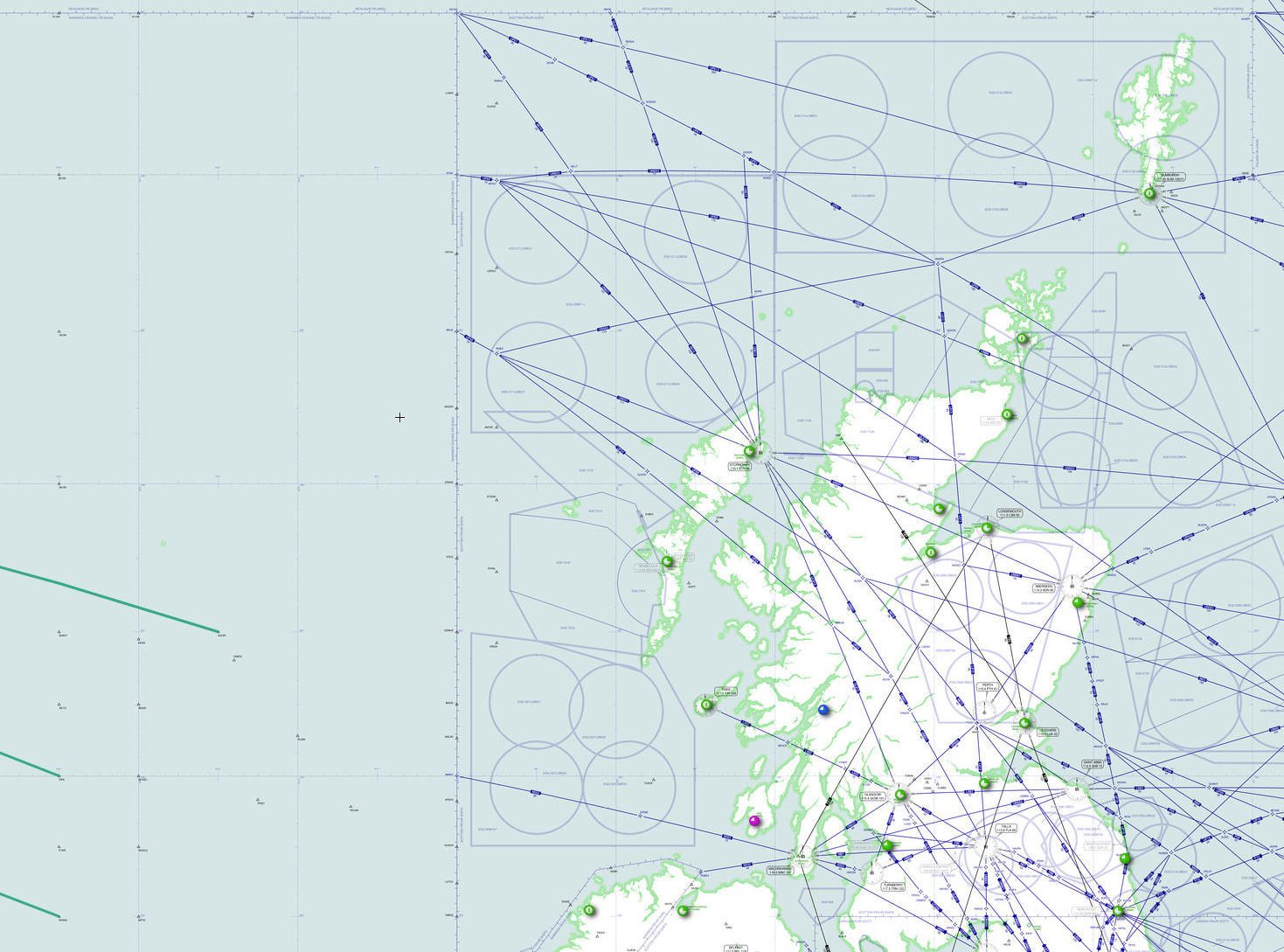
Effectively, we are compromising our neutrality and offloading this burden to the UK, so that we don't have to think about or do anything about this issue. It doesn't have to be this way though, we could build and operate the long-range radar system and when I was a teenager there was news about the US offering Ireland some F-15's on the cheap to protect our airspace from what the US probably feared was our own 9/11 happening here. Though bear in mind while I vividly remember this story, and so does my dad, I haven't actually tracked down the source of this news or rumour.
It doesn't have to be F-15's or even NATO aircraft though. Sweden's Saab makes the JAS 39 Gripen C/D and E/F which would do a fantastic job with a low flyaway cost and the lowest operational costs by some margin to boot, but it also raises other issues such as retention crisis in the Air Corps too. Of course, there are other issues in that there have been comments made about there not being parking spots for aircraft, so infrastructure would have to be expanded and we could need extra expertise to deal with the engines in the Gripen, so things would not be as simple as just purchasing the Gripen.
Overall this has put Ireland in the somewhat precarious position of not knowing what is under the sea, because our ships lack sonar, not knowing what is on the sea because we can't put our ships to sea and we don't know what's in the skies because we can't see what is our skies if someone chooses not to be seen. Our overreliance on the RAF and the Royal Navy to protect our territory is, and should be seen as a national disgrace. As Dr. Cathal Berry said
"It completely undermines our status as a militarily neutral state that we have to rely on the RAF,"
Paul Williams quoting Dr Cathal Berry TF; Secret defence pact allowing RAF jets in Irish airspace ‘undermines our neutrality’, says TD Berry
Corrupt
To Corrupt is to insert false data. For example, the use of dummies on the battlefield is an Attack Measure against the Collection function. Intrusion into a communications channel and spoofing is another example. Psychological Operations (Psyops) is an example of Corrupting information being Stored in the protein processor (the human mind).
Col. Andrew Borden, USAF (Ret.); What is Information Warfare?
Information corruption is a broad topic that I have a lot to say on, so much so that I have several addendum posts in the works on various topics inside this such as a breakdown of what propaganda is, the various types of it as well as examples from history. The piece will also mention ideas that have come into vogue such as Fake News and Misinformation and the actions of states, companies and individuals and cover some tactics and techniques used as part of propaganda such as the Official History, Astroturfing and Political Warfare.
That is for another time though when I have significantly more research done on the topic and when I am prepared to treat the complex and charged topic that it is with the appropriate level of nuance required to approach to the subject.
It's wider than this though, you could look towards the illegal entry to Ireland of US during the Abortion Referendum where they tried to illegally influence the choices of Irish voters, or you could look towards the Hamilton68 dashboard by the Alliance for Securing Democracy which can be used to track the outputs of state backed news sources in Russia, China and Iran on various platforms, or to look towards Air-Moving Device who among other things occasionally talks about platforms like TikTok being used to expand and normalize the Great Firewall beyond the borders of China.
дезинформация
Or more simply Dezinformatsiya, a Russian word that until 1939 didn't exist in English, is the covert spreading of deliberately false information for the purpose of influencing public opinion or obscuring the truth. This is something we have come to live with on a day to day basis, whether we realise it or not. A prime example of the corrupted information environment we live in is the modern Vaccine Denial or Pro Disease movement. I know in my talk I called them the Anti Vaccine movement, but they aren't against vaccines, they are in denial about the facts of vaccines because of the disinformation charlatans have peddled for so long.
Robert Evans on his incredible Behind the Bastards podcast did a two-part episode on the history of the movement and begins by talking about early attempts at having a vaccine for Smallpox, an unimaginably bad disease to contract. The process was based on a 10th centaury Chinese technique where what one would assume is a doctor would take the scabs off of a calf with Cowpox, grind the scabs up into power or a liquid infusion and place into cuts that the doctor would make in the skin of someone to be inoculated in the hopes of getting a mild infection and surviving it.
This wasn't as stupid an idea as it sounded, it's the basis for which a lot of vaccines are developed today! We use live, weakened or dead vaccine particles to develop vaccines, even some of the SARS-Cov-2 vaccines people are receiving around the world today are based on this method. This method worked, the downside is that this Cowpox based vaccine was what we call a first-generation vaccine, where one could get really ill and sometimes die from the vaccination process. While today this sounds horrific, Smallpox was an infection that killed more people than were killed in all the wars between 1900 and 1999, combined when we had a vaccine to boot, shows that the occasional death from the vaccine far outweighed the public benefit of the vaccine.
Then the second generation of vaccines came around with the most important man you have never heard of, Maurice Hilleman, The Great Vaccinator, who Radiolab did an incredible episode on of his work, where in 40 years he developed over 40 vaccines, including 8 of the 14 that are regularly given to children and in some estimates is believed to have saved 8 million lives a year. These types of vaccines were developed to reduce the risks associated with earlier vaccines because let's face it, getting vaccinated, unless you hate the needle should be a pleasant-ish process rather than a scary one. Finally today we have vaccines for things like SARS-Cov-2 based on mRNA which are incredible and leading to huge breakthroughs in vaccines.
Now, your mom or whoever sharing this vaccine denial rubbish on Facebook isn't partaking in the act of Disinformation. They are doing Misinformation, they are sharing what they believe to be true because they have fallen for Disinformation. The real people at issue are people like who the Center for Countering Digital Hate called The Disinformation Dozen.

`The Disinformation Dozen` tells the story of the business model of the Vaccine Denial, Pro Disease movement. It tells the stories of the income received by these individuals through their organisations, including links to read their tax returns, loans they received to protect employee's paychecks and salaries that they earned from being on the boards of organisations as well as data about the wages of the 266 employees they have at various organisations, working on this disinformation and income they have from being speakers and promoters at each other's events, totalling a combined $36 million, which the CCDH break down by each disinformer.
The report also performed an analysis of the spread of this disinformation, tagging 483 pieces of content between February and March of 2021, in 10 private and 20 public Facebook groups that then went on to be posted or shared 484,876 times, out of a total of 689,404 pieces of Vaccine Denial content across the platform, accounting for 70.3% of the sample of content. They were also able to show that just three of the disinformer are responsible for over half of all the disinformation.
The report also highlights that there is a clear link between the disinformers and the social media platforms they use, and the income all parties earn as the report examines a number of legal filings made by the disinformers or their organisations about how the removal of content or fact checking of their content severely impacts the income of the disinformers, yet at the same time it allows facebook to earn up to $1.1 billion, for the 37.8 million followers the Vaccine Denial Audience has on facebook and Instagram, at an Average Revenue Per Person $29.23.
YouTube earned $707,222 in ad revenue, which it splits 45:55 with the content creator, YouTube earned $318,250 and the content creator earned $388,972. While advertising on YouTube is more complex as you may not be eligible for ads or you may have ads turned off on your channel, YouTube may have earned more from this content being viewed as ads could have been placed on other pieces of content outside of sample in the study. Finally, the report took a look at the followers of various accounts on Twitter, estimating that 392,575 followers are monetizable by having ads served, estimating that $7.6 million was earned.
If you have ever wondered how these people make their money and continue to contribute verbal, textual and audiovisual diarrhoea to discussions of public health, now you know.
Realistically speaking, this isn't a particularly big issue in Ireland as 87.42% of the eligible population is fully vaccinated, as of the 4th of October 2021, it is worth looking at the below graph of Government data which clearly shows multiple plateau's, in multiple age groups showing that some people are not and have not been getting vaccinated, while the have the opportunity to do so, it shows that there is hesitancy out there to vaccinate.
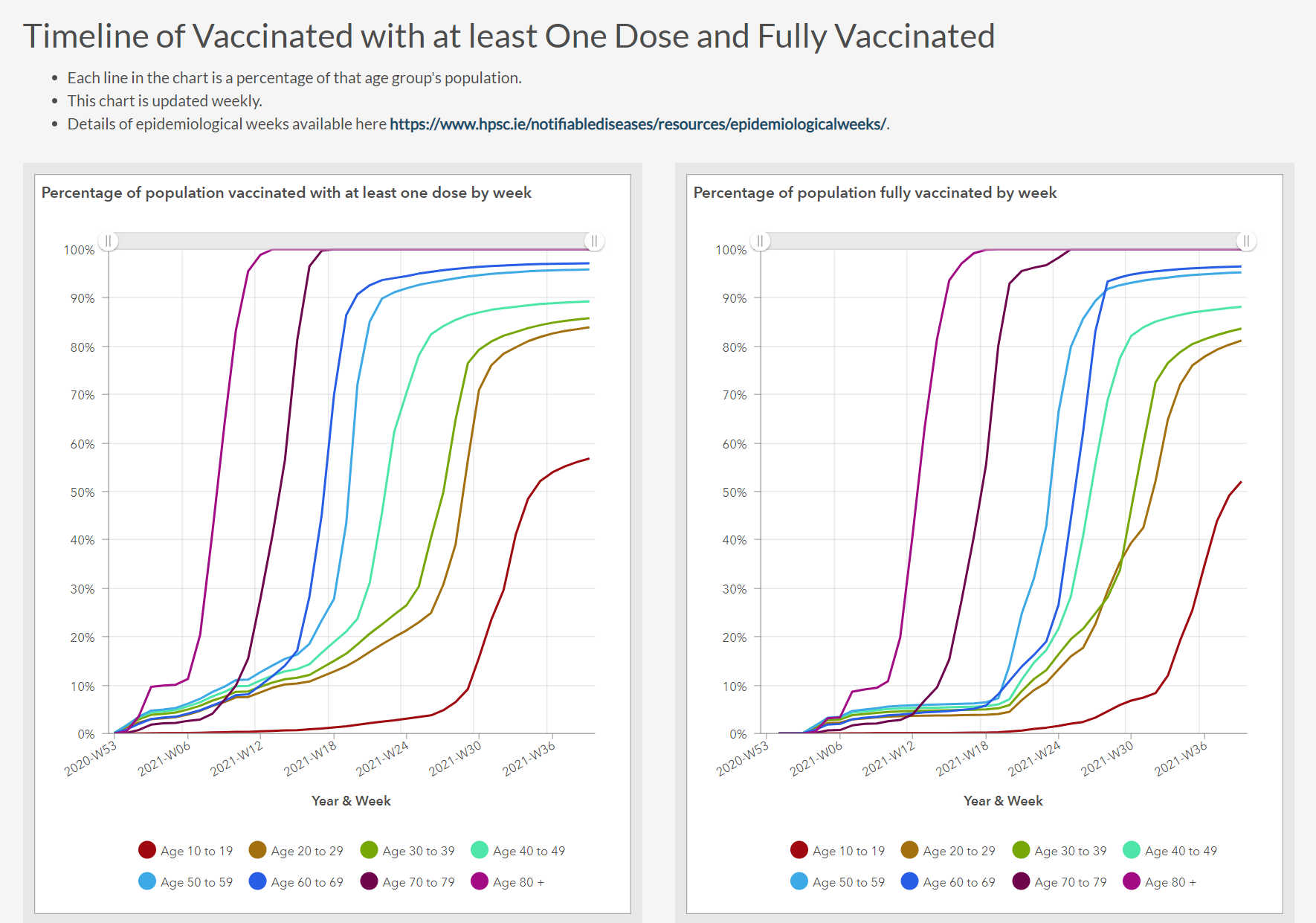
I cannot link these two things together and say that there is a causal relationship between the Vaccine Denial Disinformation and people choosing to not get vaccinated. I know from personal experience that some people cannot get vaccinated, so 100% is not possible, but the plateau's from people between 20 and 40 is unrelated to those that cannot get vaccinated as that is generally only a single-digit population, so there is hesitancy for reasons I can only speculate on. The 10 to 19 age group shouldn't be considered yet, as they have only recently been approved in part for vaccination, first for over 16's and recently from 12 and up, and the nightmarish process of going back to school would clearly impact this.
Exploit
To Exploit is to Collect against the adversary’s Movement of Data. This increases the data available for friendly Situation Assessment and makes the generation of friendly Information more efficient.
Col. Andrew Borden, USAF (Ret.); What is Information Warfare?
While Col. Borden has a definition of Exploitation in the context of Information Warfare and it makes sense to me, it may not be clear what exactly is intended by this. For me, the diagrams of Kopp and Mills do a much better job of describing what Exploitation looks like;
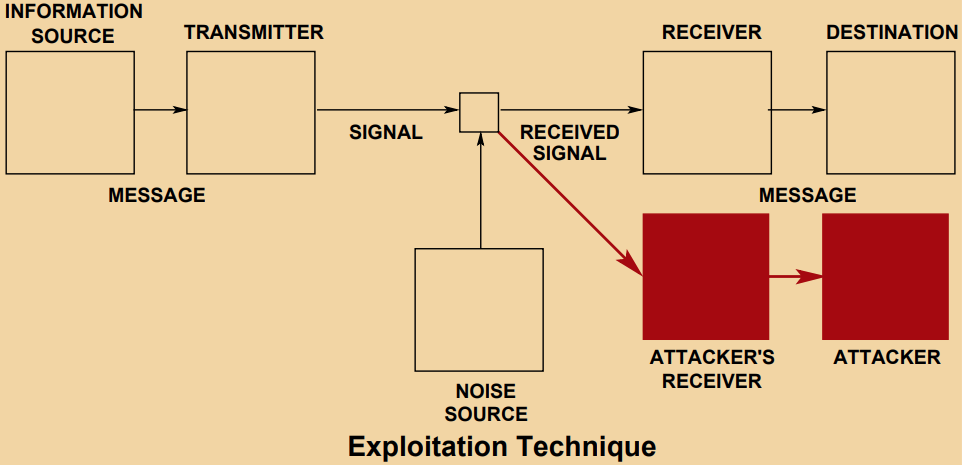
This idea can best be summed up as Exploitation being about collecting data on what the adversary is doing so that you have a better picture of their activities. This is best seen through the classic counterintelligence technique of Backbearing.
Backbearing
While I did just say that Backbearing is the classic counterintelligence technique, its use goes back a lot further than that. In Land Navigation or Orienteering, it is a set of bearings that you can use to work backwards along a path you have travelled so that even if you get lost trying to get from A to Z, you can safely work back from P to A and get un-lost. A great demonstration of the idea is seen in this tutorial for those interested.
In the world of intelligence, it has a similar meaning, though you don't know where A is, you just eventually realise based on the information you have, that you are at P and that you need to work backwards using the snippets of data or indirect data that you have to form a larger picture of what is going. You can form the larger picture by looking for things your adversary doesn't know and is attempting to find out about or figure out. If there is somewhere in particular that they are interested in and what you can infer from this. And if there is a new or unusual action that the adversary is doing that hints towards things.
A brilliant literary example is John le Carré's brilliant The Honourable Schoolboy, the second book in the Karla Trilogy. While not all of the book is about Backbearing, a significant part of the story in the beginning third of the book is about telling the story of the impact of The Fall, or the story of Tinker, Tailor, Soldier, Spy. In it, Smiley, Guillam, Sachs, and di Salis spend time in between the archives and meeting room working on figuring out the damage that Bill Hayden did and to see if he, during his time as a sleeper, though his recruitment and promotion of officers, cultivated a second-generation agent to take his place and ensure a continued flow of intelligence in the event of anything happening to Hayden.
While doing Backbearing on issues like this through open sources is quite difficult as these are intelligence matters discussed in the shadows or behind closed doors, but news does occasionally make its way to various journalists that have their ear to the ground on such matters. Since 1974, the Government has had the National Security Committee or the NSC, to brief an Taoiseach and the Government of Ireland on matters of National Security. More recently in 2017 Cabinet Committee F was established, apparently based on the British Government's COBR (sometimes seen as COBRA and pronounced this way), to bring together more cabinet ministers and have An Garda Síochána and the Defence Forces brief them on matters of state security.
In 2011, before Cabinet Committee F was formed, the FBI tipped off An Garda Síochána to the fact that six stolen identities were being used by illegals in the US. A Garda enquiry came to the conclusion that Russian intelligence had stolen six Irish identities and used them to produce fake Irish passports for cover. This lead to the Department of Foreign Affairs expelling a Russian Diplomat. Illegals are agents operating without the immunity provided by diplomatic cover and as such are taking a huge risk. Diplomatic cover would mean that in the event that your cover is blown, the worst that can happen is that you have to go back home. For illegals though, you are open to serious criminal charges.
In recent years though Russia has been quite active in Ireland. In 2015, the FSB, Russia's domestic intelligence agency, think MI5, applied to have an officer placed in the embassy in Dublin which the Department of Foreign Affairs declined, though Russia probably sent this officer under Diplomatic Cover regardless.
In 2017, Russian State-Sponsored actors were inside EirGrid, and while details of the attack are limited to knowing that a router used by EirGrid was compromised and that data transmitted through a GRE tunnel was visible, unencrypted, via a Man-in-the-Middle, nothing else is known. Though it is believed that due to previous attacks, such as the 2015 and 2016 attacks on power grids in Ukraine which resulted in power being lost for some time, it's possible that the intrusion was a similar attempt to turn off the power on the island.
2018 stands out as a particular year to look at because a fantastic series of articles broke from John Mooney in the Sunday Times. The first, the title of which is a contender for understatement of the year, 2018, implies one thing going on in that Russia is spying on tech companies here in Ireland, the article has a lot more to say beyond that, starting with the fact that it's not just the tech sector but also engineering and science sectors too as well as keeping tabs on Irish companies, Critical National Infrastructure projects and research at the European Space Agency Space Solutions in Cork, and I suspect those are not the full set of targets given the amount of R&D going on here in Ireland.
The article goes on further to state that Illegals have also possibly been operating here as in the same article it is made clear that Gardaí approached a Russian couple who befriended' a man working in the tech sector, whom Gardaí believe was the target of an espionage operation. This could be as part of the cultivation of an agent, or an attempt to get access to technology. This couple subsequently were withdrawn when their legend fell apart. Along with this, Gardaí believe that the SVR, Russia's foreign intelligence agency, think SIS/MI6, are recruiting sources in political, technology and business circles as well as aiding in the spreading of propaganda.
That article isn't done yet though. It further goes on to state that Gardaí and Defence Forces staff believe that Russia is operating a number of Signals Officers, who specialise in intercepting and transmitting information, and Cipher Clerks, who specialise in encrypting and decrypting information, out of the embassy in Dublin. This is believed because they only ever leave the embassy in the company of others believed to be intelligence officers operating under diplomatic cover. The threat is real enough that the Defence Forces are believed to have conducted sweeps of the area to identify unusual signals.
The second article in the series also discusses a lot, ranging from denials from the Kremlin to further details on Russian operations in Ireland such as Ireland being used for backdoor entry into the UK but the two major bits in the story is the not exactly a surprise piece of news that Russia is using Ireland's financial system to launder the proceeds of corrupti0n. The other major bit of news is the bombshell that Russia attempted to use cutouts here in Ireland to purchase 'controlled technologies' and that the Gardaí thwarted this attempt. Now controlled technologies, to me at least, are sanctioned technologies that any company selling such technology should have checkout out the selling as not being a sanctioned entity, and the other is for Dual Use Technologies that can be used for both peaceful and military uses such as missile and nuclear technologies.
The third article in the series deals with the expansion of the embassy in Dublin. The project was overseen by Zarubegproekt, the prime contractor for the FSB and SVR in Russia, who made the application for Planning Permission via a now defunct but unnamed Dublin architectural firm. This could be an attempt to imply that make it known that it was done in a possibly illegal manner, but without evidence to back up such a claim, it's just hinted at as the Sword of Damocles that is Irish libel law hangs over such statements in the press.
The proposed development would expand the embassy from a 2000 sq ft facility into a 10,000 sq ft facility, a fivefold expansion of the embassy. More importantly though, the expansion would also include a number of underground rooms to house 'ventilation, storage and heating equipment' to which undescribed experts say are located in unusual locations for such facilities, which raises the spectre that the embassy is being used as a base of espionage and military operations in Ireland.
Further to this, Zarubegproekt insisted that the construction of the facilities was to be carried out by builders flown in from Russia, which given the skill and expertise of builders and developers available in Ireland, it is a highly unusual request that could be read as there being classified technology being installed that no foreign nationals, such as Irish should see, and if they did see certain elements of the architectural diagrams, materials on-site or installation of equipment may raise eyebrows and hint towards the true use of this expansion. Eventually though, legislation was drawn up to halt the expansion of the Russian embassy.
Finally, the fourth major article of 2018 was about Russia smuggling in so-called 'Spy Cars' into Ireland, under diplomatic plates, which would mean that security services could not inspect the vehicles as the cars are inviolable under the Vienna Convention on Consular Relations;
Article 31
4. The consular premises, their furnishings, the property of the consular post and its means of transport shall be immune from any form of requisition for purposes of national defence or public utility. ...
Article 31.4 of the Vienna Convention on Consular Relations
This is a very smart approach as these 'Spy Cars' are suspected of housing communications and signals equipment in the tyre wells and boots of these cars, and possibly other places too. This allows the occupant, a Signal Officer, near-complete freedom to travel around Ireland and at a previously arranged time and place, drive past, or stop at a location while receiving or transmitting information to and from agents in the field or to and from sources they have cultivated. This can then be given to a Cipher Clerk for retransmission to Moscow for analysis or further instruction etc.
While we don't know exactly what is inside one of these 'Spy Cars', we got a pretty good glimpse at what the innards might look like when the Netherlands Defence Intelligence and Security Service disrupted an active attempt to hack into the Organisation for the Prohibition of Chemical Weapons (OPCW) in Den Haag in 2018, in the wake of the attempted assassination of Sergei and Yulia Skripal in Salisbury, UK, home of a famous 123-metre spire and clock.
The GRU agents got a rental car at Schipol Airport, kitted it out with what they needed and went to their hotel at the Marriott in Den Haag. This is a curious choice of hotel for four GRU agents to be in as it is right next door to the headquarters of the OPCW. The location the car was found in is also directly next to the fence that separates the properties. The equipment in the car was being used to hack into the OPCW's WiFi for the purposes of further intrusions into the network.
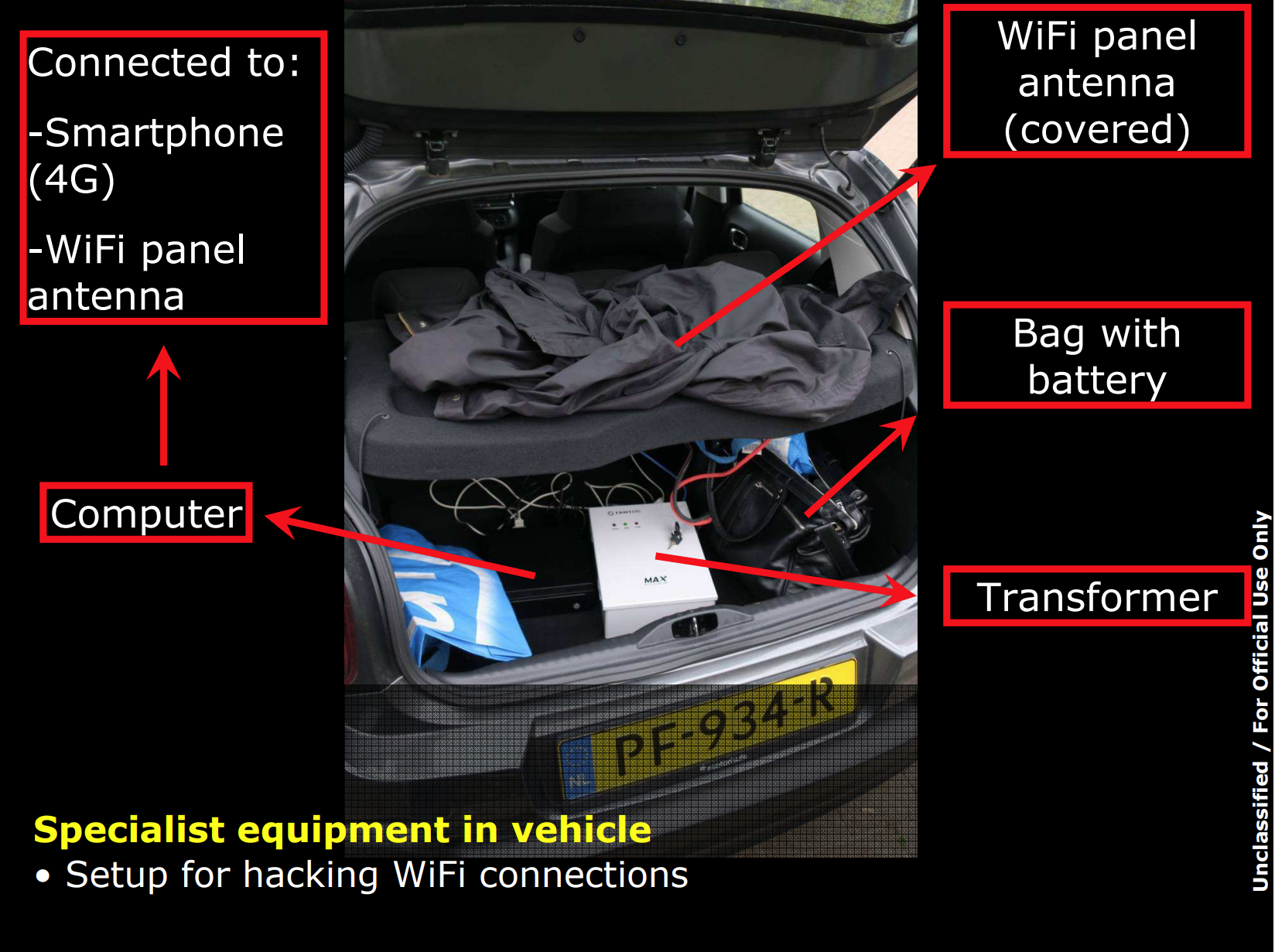
The ultimate aim of this operation is unknown, but since the weapon used in the attempted assassination, Novichok, is a fourth-generation chemical weapon that was developed in complete secrecy in the USSR and not that well known outside some very, very, very small and niche circles, Russia was probably very interested in where the OPCW got samples for comparison and how many they had, as well maybe making an attempt to sabotage the investigation.
I could go on talking about these issues but there is a story on this kind of thing every other month or so, and what I want to get across is the mountains of evidence that show that Russia is targeting Ireland across the spectrum, under the sea, on the sea, in the air and on land and doing so with a mix of civil, military, diplomatic and whatever other methods they can muster to conduct operations on Irish territory and that they are doing so for a wide variety of reasons. but there is one last story I want to highlight from 2020.
The smaller part of the story was the Russian agents were monitored while mapping Dublin port, something that would be quite handy if you know your Red Storm Rising. The major story though was related to the Submarine Fibre Optic Cables I mention earlier in this piece as Russia was attempting to map the precise locations of landing points of these cables by looking for weak points in the physical infrastructure on land and included a quote that I fully believe to be the case;
... the Russian service most likely had two intentions: spying, and cutting communications in time of conflict.
John Mooney quoting John Sipher, former Moscow based CIA offier; Russian agents plunge to new ocean depths in Ireland to crack transatlantic cables
This was also a very timely story to come out as it was out only a month before the inaugural Slándáil, the National Security Summit and it formed the backbone of a question, along with the paper from Lt. Shane Mulcahy, that I asked the authors of the National Cyber Security Strategy on why the Physical aspect of Cyber was so overlooked in the strategy.
Doing Our Own Backbearing
Rather than a conclusion as such, I would rather do some backbearing of my own and look at why I have talked so extensively about Russia and why. There are three main reasons, the first is that Russia sees us as an EU aligned state. Generally when the EU does something, Ireland follows, but also because we are a Western aligned state. This isn't to say that we are a puppet of the US or anything, but when Russia does something that is seen as unacceptable, such as attempting assassinations with chemical weapons, we like most western states expelled diplomats, actually on Austria was the only state who didn't expel anyone.
The second is because we a neutral state, not in the technical sense as defined by Hague Convention (V) from the Second Hague Convention, but because we believe we are one, it is seen by Russia weakness that can be exploited. As I have mentioned Ireland is used as a backdoor into other states such as the UK, but also because Neutrality tends to lead states to believe they are immune or to warp the perception of what things mean on the world stage. Sweden and Austria have been on the wrong side of this in the past where Sweden has a history of dropping depth charges on Soviet and Russian submarines entering its territory, setting traps for Soviet submarines and as recently as 2014 there was an incident where a Russian Lada class submarine made an emergency call from inside Swedish waters.
Austria though has had a much more troubled recent history where in 2018 an Austrian Colonel was a spy for Russia giving away details on the Austrian Air Force and Army artillery systems as well as information on the immigration situation in Austria and they were doing this for 30 years, and in 2020, there was another spy scandal where a diplomat was engaged in Industrial Espionage much like we see here. Vienna, but partially also cities Stockholm and Dublin to an extent, as capital cities in neutral states, as well as elsewhere like Geneva, are hubs for diplomatic activity and thus are homes for spies.
While he is best known for his past at 73 Easting and more recently being a bit of a clown, Gen. H. R. McMaster wrote a book recently on some of the things he tried to accomplish when he was Donald Trump's National Security Advisor and one of them was the concept of 'Strategic Narcissism' and he gave a lot of time on the Lawfare Podcast a while ago to discuss the concept;
Jordan, I think this has been a loadstone around our neck, is this tendancy to define the world only in relation to us and then to assume therefore that what we deciede to do or deciede not to do, will be decesive in achieving a favourable outcome. This is problematic because it is self referential and it doesn't ackwnolege the degree to which the other, esspescially adversary's, enemies, rivals, competitors, have over the future course of events.
H. R. McMaster discussing Strategic Narcissism on Lawfare's ChinaTalk Podcast @ 00:02:40
This for me at least sums up the last two points neatly. We don't, at a government level, view Russia as an enemy, but we aren't friends either, yet we try to get along nicely. The 'Strategic Narcissism' is that we ignore how Russia feels about us in that to an extent, we are a threat to them, but that they don't want to make us an enemy because we are a useful place to be acquainted with and if conflict were to break out, Ireland would be a useful place for Russia to operating in and around that presents them with a number of advantages. If you don't like the idea of 'Strategic Narcissism', Gen McMaster also has another them which is to say that we lack 'Strategic Empathy'.
The third issue is that we lack capability on a number of fronts in both military and intelligence matters, even in basic and simple terms. I mentioned the lack of sonar in the Naval Service, the lack of ability to view the airspace and for the Air Corps to control this airspace, but the problem to an extent is more fundamental than that. Logistics is the backbone of a military. Napoleon is said to have said that 'An army marches on its stomach' and this is a reference to the importance of logistics, something we are having a discussion about right now, and for the most part we are not talking about the logistics. As well as this, as Mark Galeotti points out, we don't even have the basics of counterintelligence;
Ireland doesn’t have a counter-intelligence capability. It’s a relatively soft target. Ireland is a major node for the global internet. It has a large concentration of tech companies. This is the new battle space of the future.
Mark Galeotti; Russian agents plunge to new ocean depths in Ireland to crack transatlantic cables
Security is an intangible idea that Ireland has a certain apathy for. There are a lot of people who do care about securing the state and I don't mean to disparage them and say that they have zero interest but that they are occupied with other things like their kids get a good education or that they can get a doctor when they need it or whatever is on their mind at work. This is a generalisation of affairs in Ireland, we tend not to have major discussions on matters of national security or defence strategy. We tend to assume that sure no one would attack us, that it will be grand so to speak, and this impacts our strategic vision for what the current threats are in the world to a great extent, imagining that we are living in a time just after then end of the Cold War, at the End of History and in how we choose to invest to deal with such threats. As such we don't have a National Security Strategy, there are ongoing consultations for it, but we should be clear that without a strategy and an honest look at the threats we face, because as I previously quoted the CEO of IBM UK & Ireland, security is key to our prosperity, and Gen McMaster agrees;
So I think that, espescially with involving these important issues, that involve security, that involve our prosperity, that involve building a better future for generations to come, we must be clear eyed about the nature of that challange and we have to establish objectives ...
H. R. McMaster on Lawfare's ChinaTalk Podcast @ 00:10:30
Really what we need is to come together, admit that while all of these are intangible idea's, that there are threats out there and that we need to protect ourselves from these threats, understand them and built a strategy around them. One that will include not just solving funding issues at the HSE, the unhoused crisis, the cost of buying homes etc, but also on wider topics like protecting our waters and our airspace from intrusions such that if a conflict were to begin that we would be prepared to deal with it.
I think that the approach is really important. The approach of first understanding problems on our own terms, then inventorying our vital interests, viewing whatever the challange is that you're facing though the lens of your vital interest and crafting and over arching goal with spesific objectives.
H. R. McMaster discussing shifting the overal stratigic policy of a nation on Lawfare's ChinaTalk Podcast @ 00:10:00
Finally, I want to mention Blowback. This is the intelligence concept of the impact of the unintended consequences of intelligence operations. If one of the above scenario's were to occur, such as damage done to Submarine Fibre Optic Cables, what would that do to a state like Ireland?
... the technological base of the Irish economy has developed significantly in recent years; the State is now home to a large proportion of Europe’s data (upwards of 30% according to some industry assessments) and the European headquarters of a number of the world’s largest technology firms. Critically also, the conceptual evolution of cloud computing has had profound implications for Ireland. In many cases, rather than being passive repositories of data, these centres are now home to live operational software environments; an outage or incident affecting one of those facilities could therefore have immediate disruptive effects on infrastructure or business across the EU or globally.
National Cyber Security Strategy 2019-2024; pp 13
What is the reputational damage to a state when we have great difficulties in communicating with the outside world and companies need their data that is stored in Ireland? Or all of a sudden a huge chunk of the world's compute power dropped off? Or if huge toolchains in the cloud that companies rely on vanished? What if financial transactions couldn't be sent? Taxes collected? The list goes on and on.
Tens of thousands of financial transactions are sent on these cables every hour along with communications. People think ‘the cloud’ is in the sky but it’s really in the bottom of the sea,
Jophn Mooney quoting Dr. Cathal Berry (TD); Navy called in as Russians suspected of targeting undersea internet cable
What Was Left Out?
Probably a lot, probably more than I am capable of knowing without being in a room of experts from every department in the government, but I do want to highlight two areas and explain why they were left out.
The Ransomware Compromise of the HSE
The ransomware compromise of the HSE is in a lot of ways a coming of age story for Ireland as it exposed a fundamental flaw in the security culture of the state. A prime example of this was when Paul Reid, Director General of the HSE, said that some services had been set back some 30 to 40 years. If malicious software is setting back something 30 to 40 years, it is indicative of out of date systems that are running software older than I am and maybe hardware that is just as old. The last time I was in A&E, earlier this year, there were computers running Windows 7 that were clearly networked systems. This massive tech debt is a problem.
We assume that investing once or in several smaller investments over a period of time are all that is needed to provide a service but we do not think about the recurring costs of things like IT or Information Security. As well as this, the HSE is complex beast where healthcare comes rightfully first. If healthcare is to come first, sacrifices come from elsewhere and while I can imagine there are a number of area's, in a number of state bodies where this is the case, there appears to be a fundamental mismatch between priorities and needs at a high level in the Government;
Honestly, I'm quite happy to blame the government over the HSE cyber attack. If your balance sheet looks like this, it's likely you're not prioritising the right things... pic.twitter.com/4vaIkSgNtE
— Gareth Go Tobann (@Gwareth) May 17, 2021
The other thing about the compromise is that the gang behind it are known as Wizard Spider and they are a financially motivated cyber crime gang. While you could look at their actions as degrading the ability of the HSE to deliver healthcare, something I found when I had an ultrasound on the day of the attack and had to give the radiologist all of the information about where she needed to scan and what for, and luckily I knew exactly what I was there for, not everyone would be as lucky. Or the compromise could be looked at thought the lens of Denying healthcare to some, the motivation was not one of an Information Attack, but was a financially motivated crime.
And just for reference, I call it a compromise and not an attack because attacks indicate that violence was used in the commission of an offence and this clearly is not the case. It's something I want to discuss more, but that will take some time as books like the Tallinn Manual's are hefty and dense volumes.
The Electrical Grid
I briefly mentioned that there was a man in the middle attack on a compromised router operated by Vodafone for Eirgrid, why not have that as a major talking point since it could be seen as Denial given that denying access to the electrical grid in this day and age? Or what about if the attack on Eirgrid succeeded and some generation capacity was Degraded?
Well, I did initially look into Degrade and Deny scenario's given that I have been working on a Malware Zoo of various pieces of malware which could be seen as something you could classify as a Cyber Weapon so I am acutely aware of malware that has not just attacked Industrial Control Systems, but also attacks on electrical grids such as those seen in Ukraine in 2015 and 2016. Or research that was conducted such as the Aurora Test that the US Department of Energy and Department of Homeland Security, where they used software to physically destroy power generating infrastructure via frequency excursion.
I also wanted to look at The Metcalf Sniper Attack which is a fascinating attempt to take down grid infrastructure by cutting control cables to prevent warnings that there was issues with the infrastructure. Then over the course of 19 minutes, shot over 120 rounds of ammunition from what appears to be several guns at a series of transformers, but not at the transforming circuitry, but at the cooling fins on the transformers. This caused roughly 240,000 litres of cooling oil to lead from them and allow temperatures to rise. As heat is impacts the performance of electronics, overheating leads to systems shutting down and this is what happened, but it wasn't clear that this had happened as the communications links had been cut.
Ultimately though, I chose to not concentrate on the gird, not because the link to Russia may be seen as more tenuous by some, but because anyone who has kept an eye on the grid for any amount of time knows that the current issues in the news about Data Centers are not news and this has been warned about for years. The narrow generation margins that have been run on the grid for the longest time have left us vulnerable to unreliable power delivery if we were to have an incident occur or have a compromise of the grid infrastructure were to occur as we saw here in 2018 or in Ukraine and an unreliable grid would make Ireland seem unreliable and could damage the reputation of the state in the eyes of foreign direct investors.
Plus events that could cause the kinds of damage seen in the Aurora Test, frequency excursion's, though not nearly as extreme, happen on a fairly regular basis and engineers at Eirgid make sure the grid is safe, online and functional so that you never notice. You can see some events from the past 3 years below;
Woops, someone's just had a clanger! pic.twitter.com/45IxynE5qP
— Mark Coleman (@Spark_ie) October 7, 2019
Oops! Someone dropped a spanner into the drive train somewhere 😬
— Mark Coleman (@Spark_ie) July 1, 2020
Two frequency events within 20 mins, very unusual, but no bothers to @EirGrid pic.twitter.com/1vpdZ4mAvm
There's just been an absolute whopper of a grid event on the Irish electricity system. Grid frequency floated around 49.75Hz for ~15 minutes! Back @ 50Hz now..
— Mark Coleman (@Spark_ie) May 4, 2021
(I now see Coolkeeragh CCGT 425MW was the cause)
Never seen this (the duration of dip) in my 11yrs of working on grid pic.twitter.com/NjwVse1la1
And for context of what those frequencies mean, you can see the below tweet. For reference, the context of the tweet is after the 2021 event directly above where the Coolkeeragh gas power plant went offline suddenly and 425MW of generating capacity vanished from the network.
Well, as per Grid Code, the system can (and did) operate fine at that frequency.
— Mark Coleman (@Spark_ie) May 4, 2021
BUT, the risk is if another large unit was to trip while being at 49.75Hz that's absolutely [certainly] blackout territory. pic.twitter.com/qswK62xiDp
If such an event were to happen again as we saw happen at Coolkeeragh again, or if malware was nicely placed to wait for such an event, we would be on the brink of blackouts. If things got really bad and grid infrastructure started to need to be disconnected or turned off, starting again from scratch is called a Black Start and it is complex and risky.
Acknowledgments
Cheers to Ben, the editor 😳. I can't thank enough David for his amazing ability to watch and dig up things related to the mostly unseen and uncared for elements of National Security in Ireland like the power grid, and the naval and air space around Ireland. Journalist John Mooney, for his articles and podcast, his generous time, huge patience and tips on various goings on. And finally, a thanks to the many, many more Wonks for the discussions on the various cyber and information warfare aspects.
