With the War In Ukraine, we have a unique opportunity to look at Information Warfare happening before our eyes and compare what we saw to some of our past assumptions on what was expected to be seen in such a conflict. As someone who has spoken a lot about this previously, CMG Events asked me to come along and update Ireland on what we have seen and what we can learn from the conflict.
Video of the Talk
The talk last year was on the Information Warfare threat to Ireland and served as a primer on Information Warfare as well as outlining the limited number of attacks possible in Information terms, as well as what we can see happening here in Ireland. At BSides Dublin, I gave a talk which was written in a very short amount of time on what we can see happening now and why it is more boring and mundane than most people had probably expected.
A Quick Primer
Last year I introduced viewers, listeners and readers to Col. Andrew Borden, USAF (Ret.) model of Information Warfare, where using Claude Shannon's Mathematical Theory of Information, Borden broke down the various attacks using Information Warfare to lay out the four categories of attacks available in the Information dimension of warfare, Deny, Degade, Corrupt and Exploit. He also talked about how Information Warfare would be used in a Combined Arms fashion, where militaries use multiple dimensions of warfare, such as land air and cyber at the same time, to achieve goals. This is something we have already seen in Ukraine;
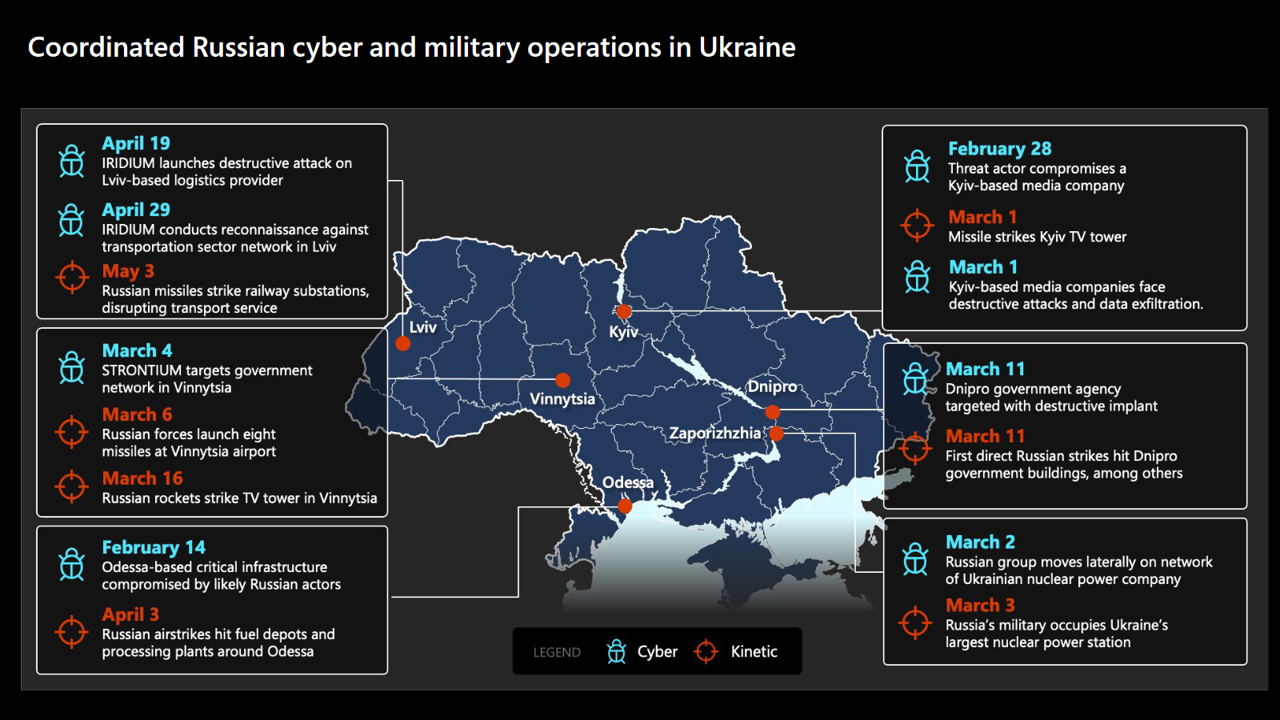
In the past, I have given examples of the various kinds of attacks in each case but as this is a quick primer and I have little new on this front, rather than give the same verbose examples, I will rather give brief explanations and only highlight new and interesting examples with context. If you are interested though in some deeper examples, you can references previous posts and talks here, and here.
Attacks that Deny & Degrade
Attacks that Deny are attacks on the information itself. These can be attacks such as Wipers that in some way destroy data, but they can also such as ones that cut off access to data or slow your access to information. This is best understood in the context of forcing adversaries to use slower connections, such as using satellite over fibre or cutting fibre cables such that you no longer have access to data.
Attacks that Deny can be broken down into two different categories. The first is attacks against data collection assets. In military terms, this could be radars or intelligence collection planes but cyber audiences would be more familiar with assets such as those that feed data towards SIEMs for analysts to tackle. The other form of Denial is where rather than go after collection, you go after the analysts or decision makers that utilize such data. While you might see this as your CEO or CISO etc, traditionally militaries have seen this as high ranking officers such as generals or the leaders of particular operations to upset the operations.
Attacks that Corrupt
Attacks that Corrupt are attacks that feed false data into an Information Environment and is best exemplified in the everyday world that we all live in as disinformation such as that rubbish spewed by the Anti Vaccine crowd, or as I see them, the Pro Disease crowd. After all, if you are against preventing diseases, you are for disease. It is the flip side of that coin. Russia has a long history of such Disinformation, sometimes spread by propaganda outlets such as RT but also useful idiots or fellow travellers of Russian ideology.
In the past, I have shied away from having discussions or talking about Russia like this as for a lot of people it is too political. In the wake of Russia's escalation in the War in Ukraine though, I am taking my gloves off. I am not making political statements, but statements of fact and in you disagree with me on these particular issues, that's fine! But we aren't having a disagreement about politics but the nature of reality because Russian Propaganda and Disinformation are no basis to build your worldviews upon or worthy of engagement in good faith discussions.
A prime example of the impacts of this Russian Propaganda and Disinformation can be seen in Russia by looking at who is being targeted with such Propaganda and Disinformation, as we saw with a fun article from the OpenFacto Francophone OSINT collective who tracked down the massive extent of Russian Military Intelligence's control over Propaganda and Disinformation when they were linked to the InfoRos group of sites. The GRU is using OpenFacto as a form of population control to limit and shape the opinions of ordinary Russians on a daily basis as InfoRos are some of the most popular sites in Russia.
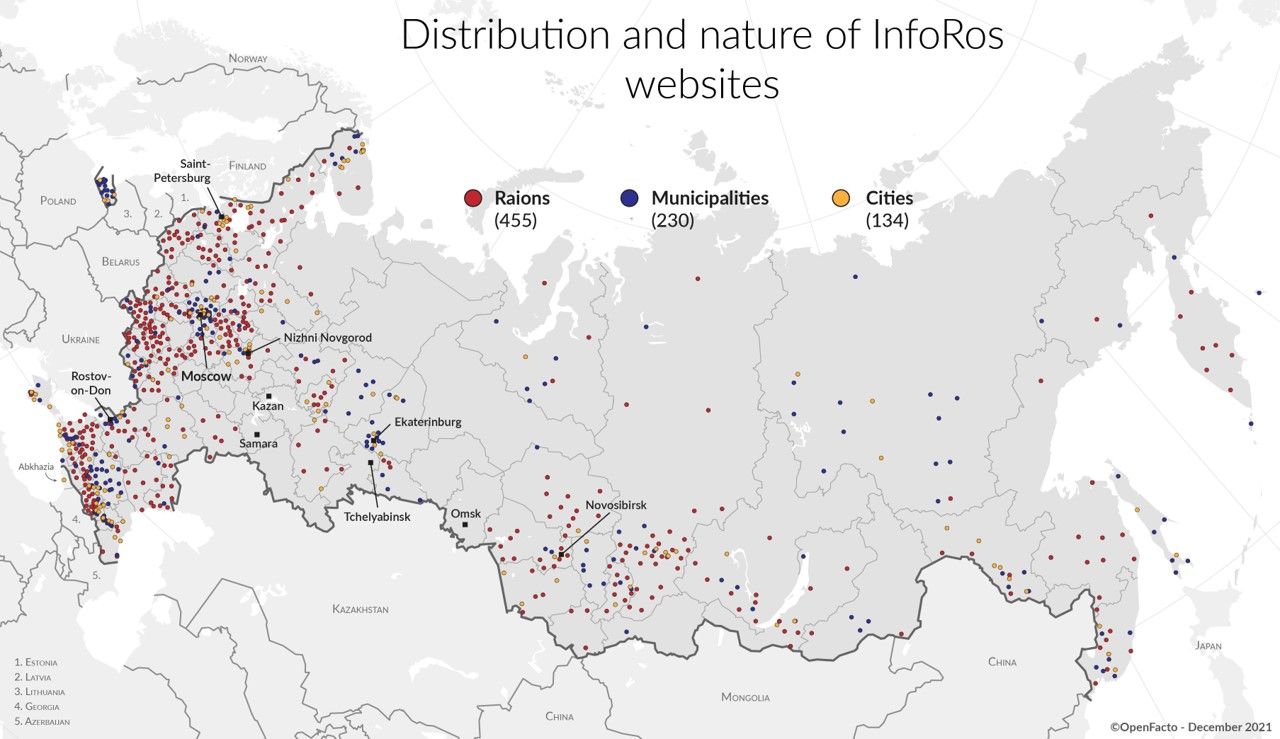
But InfoRos is also cited as a source of news used by other sites that then are shared around the world, such as Infobrics and OneWorld Press, which spread anti-Western and Pro Russian Propaganda and Disinformation. It should also be noted that former directors include Denis Tyurin and Aleksandr Starunskiy have been directors of InfoRos. Estonian intelligence have identified Starunskiy as commander of, and Tyurin as an officer in GRU unit 54777 (pp 62). This unit specializes in psychological warfare, informational confrontation, information-technical influencing of foreign countries and protecting Russia against foreign information operations.
One part of this unit's operations include exposing "the civilian population", as targets of psychological warfare. So what impact does all of this have on ordinary Russians? Well a group of people put together a Google Map of local war dead from the War in Ukraine. The map has now been removed for a violation of the Terms of Service, but I took some screenshots of the map and you can see that there is a relationship between places where InfoRos operates and where Russia's war dead are from;
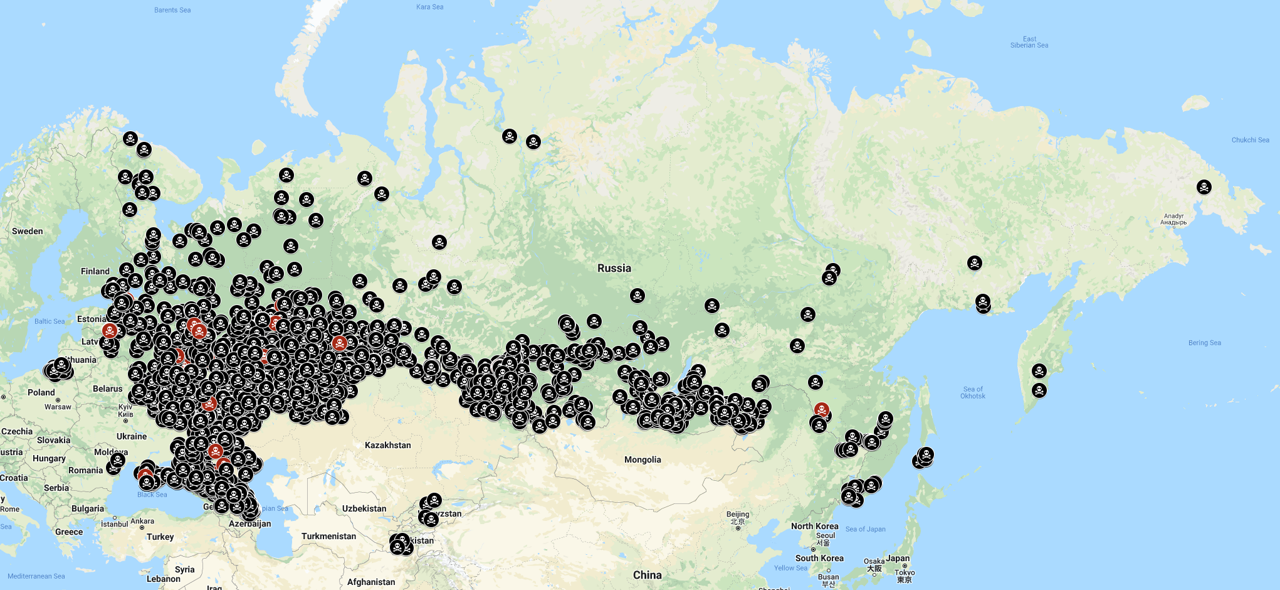
I do wish I could overlay the Open Facto map with the one from Google as they are different projections and while I have some photoshop skills, I don't have the ability to curve Mercator Projection over whatever Open Facto used. The good news though is that while I can't do this, BBC Russia did their own dive into Russia's war dead and created their own maps, though they did so via Oblasts rather than in the granular depth Open Faco used, so you can't see the impact of the Propaganda.
We can also see a great example of Russia's process in action where in November Tim Kirby, an American by birth but Kremlin sock puppet by profession, began to talk about US funded Biolabs in Ukraine on his English language radio show in Russia. Once this is out there prior to the war starts, it is prepositioned to be amplified by other sock puppet outlets when the time comes that it is needed.
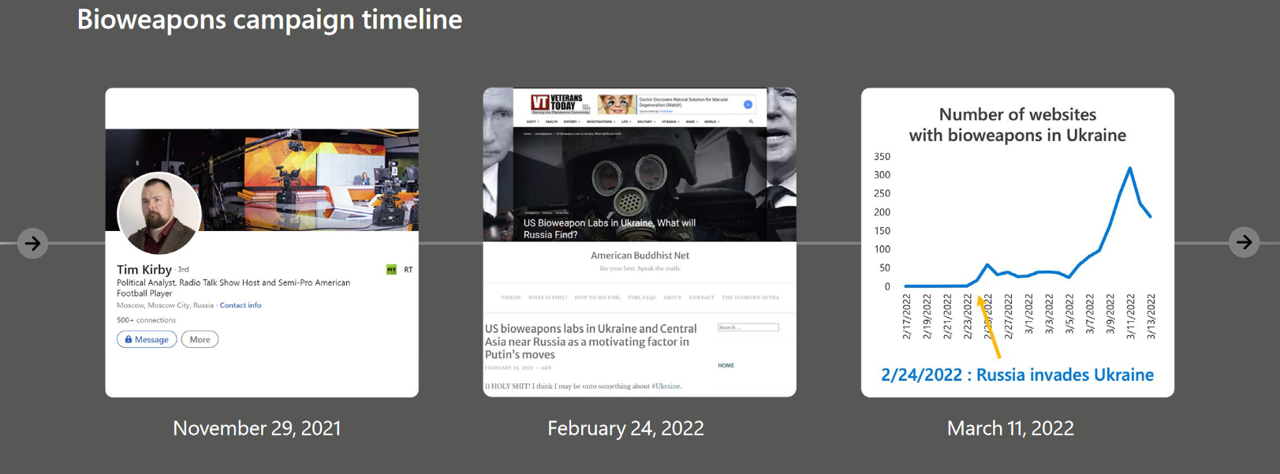
In some ways, this is a very spaghetti-at-the-wall approach, but all you need is to keep coming up with outlandish ideas and for one to take hold for it to become a whole thing. We see this regularly with conspiracy theories such as this. Once the war began, Russian sock puppet sites amplified the Disinformation, and it eventually took hold. You would expect that any credible journalist would do their due diligence but journalism is dead and clicks are king so it became a major news story built on nothing but Kremlin fueled hot air, sometimes with the Kremlin's own "Journalists";
RT journalist Bryan MacDonald: ‘I called the war wrong. I clearly wasn’t as much of an expert as I thought I was’ https://t.co/pW0qTGs65h
— Kevin Rothrock (@KevinRothrock) March 16, 2022
This is a regular problem when dealing with such Kremlin Propaganda and Disinformation. Experts turn out to be not experts at all and are pushing a particular angle that is curiously pro-Russian. And sometimes we disappointingly see that in causes that I for example believe in, such as this comment from the Peace and Neutrality Alliance (PANA);
Let's ignore the strategic narcissism for a second, I'll come back to that...
— 🖕Пу́тін хуйло́ 💙💛 Слава і победа Україні 🇺🇦✊ (@LegendaryPatMan) June 28, 2022
Ukraine was attacked by a superpower. Losing ONLY two cities is an achievement especially when you consider that the cities where lost and recovered https://t.co/bSehbefFDe
Now not everything PANA says is pro-Russian but it is worth noting that while they are anti-American, they are also curiously quiet on Russia's War in Ukraine and then say pro-Russian things on twitter. It makes you question how pro peace they are and what they really stand for, if they only want the US to be peaceful but are ok with other, more authoritarian regimes going to war, particularly the brutal war that Russia wages.
The most effective way to deal with Disinformation and Propaganda, as we have learned time and time again, is that the most effective way to deal with the problem is to Deplatform such sock puppets and those who spread hate such as Nazis and racists. Not only does it make the world a better place for everyone, but it also makes such people feel unwelcome in regular society, which they should be. To an extent, we have done this in Europe and we are all the better for it.
Now some people don't like this as they believe it infringes their Free Speech, but in an essay in the New York Times, Roxane Gay discusses the idea that this isn't censorship where there is an attached punishment, but it is curation where we choose to not discuss or engage in such hate or bigotry. In the Marketplace of Ideas that we have today, we nearly universally agree that there are some just bad ideas like Nazism or Neo-Nazism. By choosing to not engage in these ideas, we are expressing that these ideas are unacceptable. By deplatforming these ideas, we are saying that they are unacceptable in decent society and the frankly genocidal statements that are on Россия-1 for example, are totally unacceptable.
The Other Corruption
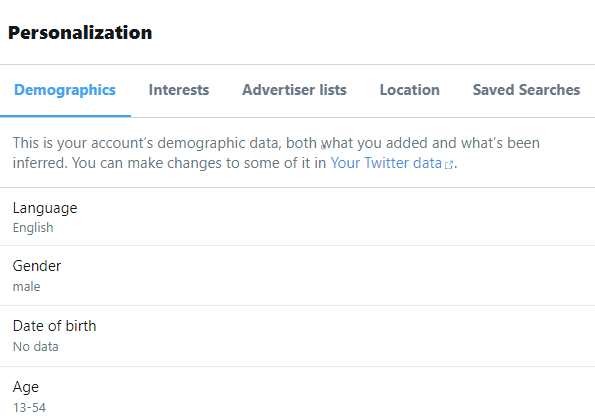
One of the things that I am becoming increasingly cognizant of is how algorithms tailor a picture of the world. This can be through search results, in which we are Filter Bubbled into being a particular person based on the data a search engine has about us. Or how twitter doesn't provide us with information as it comes in from those we follow, but what twitter thinks we should see based on what it thinks we want. This can be problematic given that sometimes when a company has a poor picture of who it thinks you are. So for example, if you ask twitter for all of your data, which you are entitled to do under GDPR, you can look at twitter's algorithms think you are, and because I gave literally zero data to twitter, they are aware that I am a male between 13 and 54 and I speak English. That is it;
It should also be noted that this can be used for more nefarious purposes as we can see with the Great Firewall in China where data is only allowed in if it passes muster with the censors at the Publicity Department of the Chinese Communist Party. Some of these things sometimes bleed out into the rest of the world, such as we have seen with TikTok where keywords in posts trigger a review before the post is publically visible, or how TikTok has data sent back to China even though they pinky promised not to send data to China, or OnePlus phones sending back a file called badtext.txt to China for some reason. I could go on, I have piles of examples like this where a mix of Governments and just Surveillance Capitalism generally are being used to exploit or monitor people in extremely distasteful ways, something women, particularly in the US are coming to terms with very quickly.
Attacks that Exploit
Finally, there are attacks that Exploit. Exploitation is exploitation in intelligence terms rather than the cyber sense. Rather than infiltrating a system, you are collecting intelligence on adversary actions to build a picture of what is going on. This can be collecting and analysing fresh data as it comes in, or it could also be taking previously collected intelligence and reanalysing it in the current context to build a more accurate picture of the threat posed by a particular adversary, a process called Back Bearing. Last year I showcased how you can use Back Bearing to put Russian intelligence operations in Ireland into context and this year, I can do the same by looking at the diplomatic lists, that the Department of Foreign Affairs publishes every month, and comparing February 2022 to March of 2022, when Ireland expelled 4 Russian diplomats for "security reasons" i.e. they were spies;

While I can't identify all four diplomats that we expelled, as one of them may have been some kind of lower functionary rather than a fully accredited diplomat, we can for example look at Igor Molyanov, who has a LinkedIn page. Now if you're expecting these identities to tie back to something major, you'll be disappointed. Vladimir Vasilchik, or in Russian Владимир Васильчик, which you can use to find a completely empty facebook (archived here) profile for example.
This is because these identities are what are known as Legends. These are credible identities, with backgrounds, that one can use get by as someone else, for example as a student, as we saw with Victor Muller Ferreira a.k.a. Sergey Vladimirovich Cherkasov, a Russian spy who attended Trinity Colege Dublin between 2014 and 2018, as part of building his legend.
What We Can Learn
1. Reassess Threat & Risk Models and Your Intelligence Cycle
In Intelligence, one of the most valuable things you can do is to look at your Intelligence Cycle and look for flaws in your processes. Generally, this is valuable as you want to always be producing your best intelligence but it's even more important when you are wrong about something. Some people find being wrong to be a bad thing, people perceive that it makes them a bad person or less worthy. I on the other hand, I LOVE being wrong! Being wrong is the single best way to learn something and to improve whatever you are wrong about. To quote one of my personal heroes, Gene Kranz;
Failure is an ingredient in life, it's an ingredient in growing. Probably the worst failure of my life, and our lives as mission contollers, is when we lost our crew. And we lived with that failure. And what we did about it though, became very important. We sat and established a set of values, a set of standards, that we would all live up to. They were expectations for ourselves and for others. Failure is an incredible, intense, learning process and if you use it as a learning process, it was worthwhile
Gene Kranz on Failure: My Path; Smithsonian National Air and Space Museum; @ 00:01:15
If we apply this to myself and my thinking on Russia, my biggest failing remains my horrendous Russian... Years of trying to learn it have not paid off all that well so I have limited access to some very valuable information. Google Translate can of course help, but if you want to go into a forum used by Russian soldiers posted in one part of Siberia to try and understand how they feel about various things, you are going to be gated off from a lot of the best information about how troops feel about various situations or how they see the world from inside Russia.
Of the data I do have access to, in English, the small amount of Russian that I can read, Russian via Google Translate or Russian I can have a friend translate, there are two other categories that my failings fall into. The first is my failure to connect the dots between disparate events, and the second is my failure to weigh data properly.
Dots I Didn't Connect
- I was aware that Russian pilots had lower flight hours per year when compared to other militaries. The International Institute for Strategic Studies, in their 2014 edition of The Military Balance, estimated that Russian combat pilots had approximately 60 to 100 flight hours per year and transport pilots had 120 flight hours per year. For comparison, The US Air Force in 2018 had pilots flying 18 flight hours per month, or 204 per year. While this is lower than what the USAF wants, it is between double and treble what Russian combat pilots get by comparison. Ultimately, flying a plane towards the ground so you can fire off some rockets, is an utterly terrifying experience that you can't just go out and do! You need to train to be able to do things like that. Sames goes for a lot of things and when you are training, you aren't under fire from a billion stinger missiles with your actual life at stake. So to be able to tune out the monkey brain and focus on the mission is hard and requires you to train for these things, repeatedly.
- I was aware that Russia had particularly poor logistics when compared to a western military. Where we would use a Company, a unit with between 80 and 250 people, Russia would use a Platoon, a unit with 10 to 100 people. In military terms, this is an order of magnitude smaller of a unit. I knew that Russia was tied to railroads and that they just didn't have enough trucks to supply their troops in an engagement, let alone consider the state of the trucks. What I wasn't aware of though was that Russia's military hasn't adopted the concept of pallets. When I first heard this, it broke my mind... For me, there are only two lessons worth learning from World War 2, and one of them that is that logistics win wars. You can see it in Normandy with the Red Ball Express, on small Pacific islands with the Tokyo Express, and you can see it on the Eastern Front where fighting happened basically along railroads or to cut rail links. You can even see it in US tank platoons where the US designed the Platoons around the GMC CCKW 2½-ton truck. One truck could carry all the fuel, ammo, spares, food etc, that a platoon of 4 or 5 Sherman's would need to operate for a day. Not to mention the Sherman itself was designed to be highly reliable so that it would need less maintenance and be less of a logistical burden and how the existing burden lead directly to the design of Roll On/Roll Off ships, which are commonplace today in military and civilian logistics.
- There is a lot that could be said on corruption in Russia's Armed Forces, RUSI has a fantastic blog post linking to just some of the issues that have come to light because of the War in Ukraine. In particular, though I want to focus on the radios that Russian Forces are using. They should be using the R-187 Azert SDR radio, which on paper is a modern military tactical radio, but we really see them using a bunch of civilian Baofeng UV-82 radios, which you used to be able to buy on Amazon for around 100 quid. The Azert radio contract was to be 18.5 billion rubles but 6.7 billion was stolen as part of bribes and people skimming cash off the top for themselves. In the end, the radios ended up being cheap-ish junk, mostly made in China using off the shelf parts. This is no way to make one of the most mission critical pieces of military hardware.
- The Su-25SM3 upgrade program, which would bring the Su-25 up to the early to mid 2000s by western standards in Close Air Support aircraft, started in 2014. By 2019, 25 upgraded aircraft had been delivered, with three more in 2020 and what sounds like a single one in 2021. We see similar things with the vaunted T-14 program where there were to be thousands of them built but to date but really we have only seen prototypes and the first deliveries were to arrive in 2022, but I don't think that will happen for reasons I can't quite put my finger on... The delivery was also to be made in to the Taman Guards but to say they have been decimated in Ukraine would be a gross understatement.
- After reading Mark Galeotti's fantastic book, The Vory, on the history of the Russian Mafia and to an extent, Russian Organised Crime in general, I was well aware of the depths to which organised crime had permeated Russia, from culture to the government. Even when Putin went into Ukraine first in 2014, some of his vanguard were Russian gangsters along with local Ukrainian mobsters. I knew that Крыша (Krysha) literally meaning roof, or in context, protection, but I didn't think that the military would need protection too. The story of Misha the Bear and how he extorted three brigades at a base that became known as The Damned Place is worth reading up on.
- Finally, I was aware of дедовщина (Dedovshchina) in the Russian Armed Forces. This is the culture of hazing as some people call it, but as I see it, it is the bullying of lower ranking soldiers by higher ranking ones. This over time has led to an internal culture of brutality in the Russian Armed Forces whereby the most brutal rise to the top. This is why so many Russian officers see no issues indirectly or indiscriminately bombing civilian targets or committing war crimes such as torture and murder in places like Bucha, Borodianka and Makariv. I can hardly imagine the effect that this culture has on a private who may never have seen any active combat at all and only gotten the most basic of training.
I can't even begin to fathom of any of this would impact Russian soldier's ability to fight or the state of their morale and I haven't even mentioned how behind the times their medical equipment is in the field or how just prior to the war some soldiers went days without rations when I could buy them online and in date when they were getting gone off ones.
Poor Data Weighing
- Estonia's Foreign Intelligence Service publishes a yearly document, which they call International Security and Estonia. I have been reading them for years at this stage because they are fascinating documents from one of the few countries in Europe willing to call things as they see them, in particular, they see Russia as their largest threat and generally, they have a LOT to say about Russian actions in Estonia and the greater Baltic region. in 2021, they specifically said that Russian Armed Forces in Ukraine "is a clear sign of Russia’s unwillingness to renounce aggression." (pp 18). In the 2022 report, which came out of the 31st of January 2022, the document literally said "In our assessment, the Russian Armed Forces are ready to embark on a full-scale military operation against Ukraine from the second half of February." (pp 10). While this is all data I am aware of, and by the middle of January I had my mind made up that Russia was going to invade Ukraine, including picking dates, they were one of the few to make that call and prior to anyone taking notice, make it clear that actions such as we saw from March of 2021, when the military buildup on Ukraine's border started, that this was par for the course for Russia.
- I fell for Disinformation. Lots of it. Even though I should have known better. In particular, I wasn't as skeptical as I should have been with news sources such as TASS or Pravda. When there was a missile test, such as we saw with Sarmat, I shouldn't have assumed that this was a production specimen but a unique one off to have the troubled program finally seem finished to the world. When I was looking at military exercises like ZAPAD or VOSTOK, I should have assumed that they were more choreographed than I had realized as I have been told now that in some cases, troops trained just for their one bit to seem powerful to Dear Leader Vladimir Vladimirovich.
Now this is all stuff I should have known better. After all I do spend A LOT of time talking and thinking about Russian Information Operations. But it should also be a lesson in the power of Disinformation, particularly in an area that is known to be particularly hard to analyse as military power isn't as simple as comparing numbers and requires expertise well beyond a single area. It also requires that you dig really deep into some very weird details like the length of time that chromium-lined barrels for artillery canons can hold up to wear when you are firing hundreds of rounds per day and what you can do to mitigate the performance degradation that happens over time (pdf download for reference). Though, none of this stopped me from believing Слава победа Украïнi (Glory to Victory of Ukraine)
With Good Data Comes Good Analysis
In the run up to the War in Ukraine kicking off again, I was still subject to a lot of these flaws, but there was so much overwhelming data coming in on what was going on that it was very, very easy to discount the disinformation coming from Russia.
The other thing that is worth noting is that internally for Wonk's doing OSINT, I try and drive the F3EAD Cycle. One of the Wonks, who wants to remain anonymous, so let's call them Horacio, is incredible at using the F3EAD cycle! He uses a nearly entirely curiosity-driven approach to understanding what is going on in a given area and does so over time. They will fuse GIS, with imagery, AIS, ASD-B, and documentary evidence from the past and present, along with his thoughts and analysis as their work is ongoing. This continious process of recombination of data based on what is happening, and their open sharing for criticism and input from the Hivemind of Wonk's, allows them to continually refine their understanding of what they are looking at, build signatures and start to make intelligence driven predictions about what is going on over time.
That is real intelligence work! Which kinda leads me to my third failing. I do a lot of my thinking by taking notes and saving things, and I do so in a mostly siloed away. I rarely share it or work in a completely open fashion like Horacio, leaving me subject to my own biases. The few times I do come out of this silo are when there are major world events going on and the Hivemind dogpiles into a thread on Slack and brings the app to its knees. This is what happened in the lead up to the war and it brought around some interesting results.
The Rasputitsa to Russia's or Bezdorizhzhya to Ukrainians, or the Rainy Seasons, where the unpaved, and sometimes paved areas of Russia and Eastern Europe can become so impassible that even things like tanks, which should be able to cross all terrains at all times, get literally swallowed up by the mud. Knowing this was coming and that the Winter Olympics were on in China, and that Xi Jinping really enjoys sportswashing things like China's genocide of the Uyghurs, Putin was unlikely to make enemies on all his flanks. We also knew that units were coming from the Eastern Military District and with estimates of travel time from East to West of Russia, time to unload, make it to jumping off points, receive plans or objectives and plan for them.
You could make a pretty good guess that with Putin's short war hypothesis, that the war would begin sometime after the 21st of February and before the Rasputitsa, which generally starts at the beginning of March, but the time the Rasputitsa hits vary. Regardless it gives a neat little window of two weeks to have a quick 20 minute adventure, in and out. It would also allow Putin two months to attempt to wrap up Partisan activities before May 9th, Victory Day.
A week later in response to an emoji poll I laid out what I believed Russia would do based on their operational tactics. I believed that they would bring the God of War to bear on Ukraine followed by an offensive in the current war to take major economic centres off of Ukraine⁵ pic.twitter.com/UtNInLopIB
— 🖕Пу́тін хуйло́ 💙💛 Слава і победа Україні 🇺🇦✊ (@LegendaryPatMan) February 21, 2022
Using data from studies about Russian combat power and their perceived ability to attack in a given direction, along with my knowledge of how Russia's Armed Forces are supposed to fight, I made some predictions about what their targets would be, and in particular, I laid out some major targets for Russia such as Kharkiv, Kherson, Kyiv, Mariupol, Odesa, Sumy, and Zaporizhzhia. This allowed me to draw a map of what I believed Russia's offensive would look like;
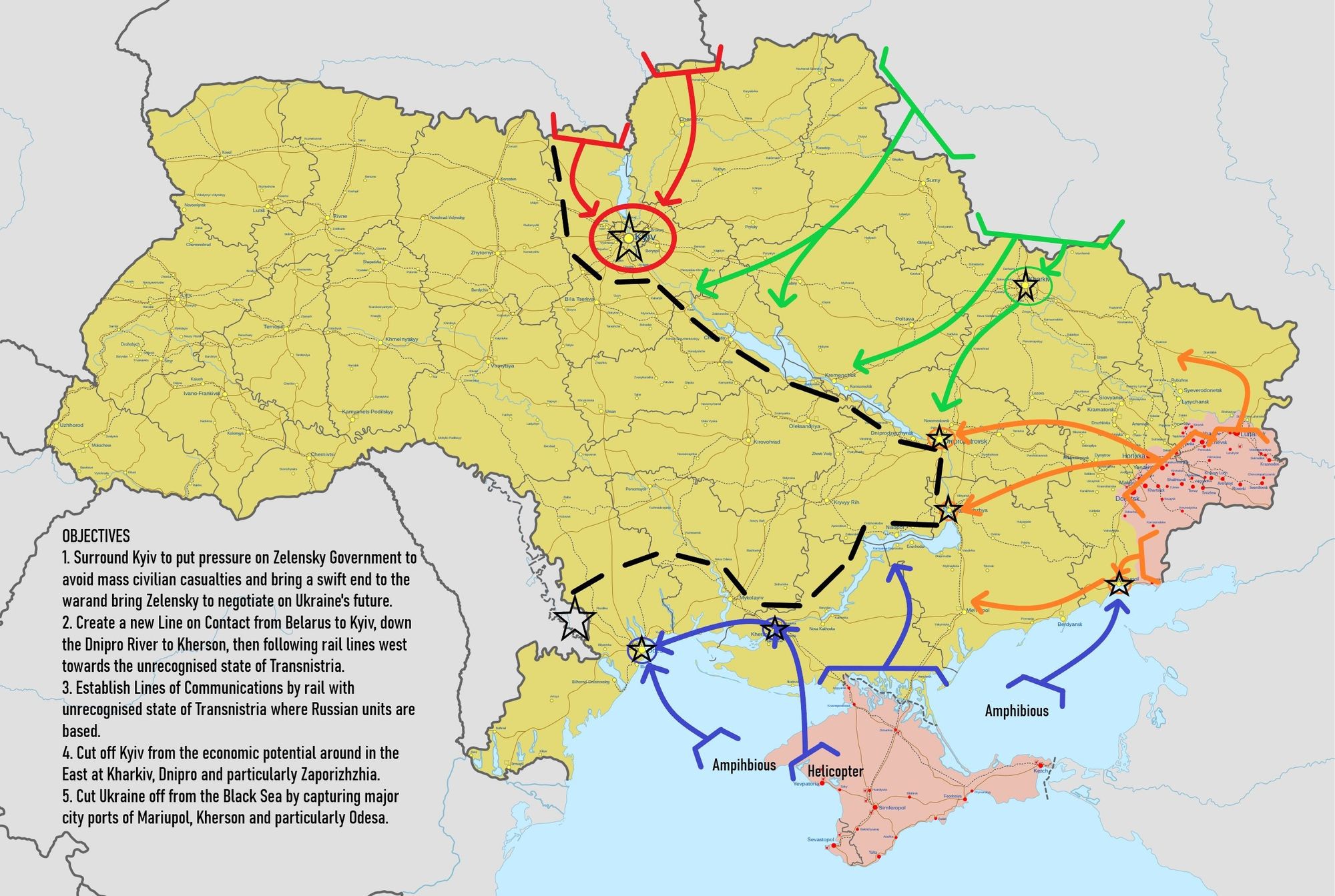
For the most part, this is what we saw. The Northern Axis, in red, culminated with the Western Flank stalling in a 40Km Convoy to nothing and the Eastern Flank stalling at the Siege of Chernihiv. The Northern Front of the Central Axis was stalled in the Battle of Sumy but did go try to go around Sumy and deeper into Ukraine, reaching as far as the area around Brovary on March 31st, while the Southern Front culminated in the Battle of Kharkiv. The Donbas Axis pushed out to control the entire Donbas and Luhansk Oblasts. Finally, the Southern Axis would, along with the Donbas Axis push for Mariupol, where we witnessed the Siege of Mariupol, along with a push for Kherson and Odesa, though Ukraine headed off this push at Mykolaiv.
Overall I had quite the high hit rate. I picked the areas Russia would attack, though not exactly the correct methods, I picked the dates that Russia would attack and was off by 24 hours and I did this over a month in advance. This is the power of intelligence when driven by good data that has been understood, rigorously analysed and critiqued rather than fitting assumptions and biases to the situation.
Looking Forward
Back to cyber things. So if we look at Russian cyber activities in Ukraine, can we learn anything from what we see in the data?
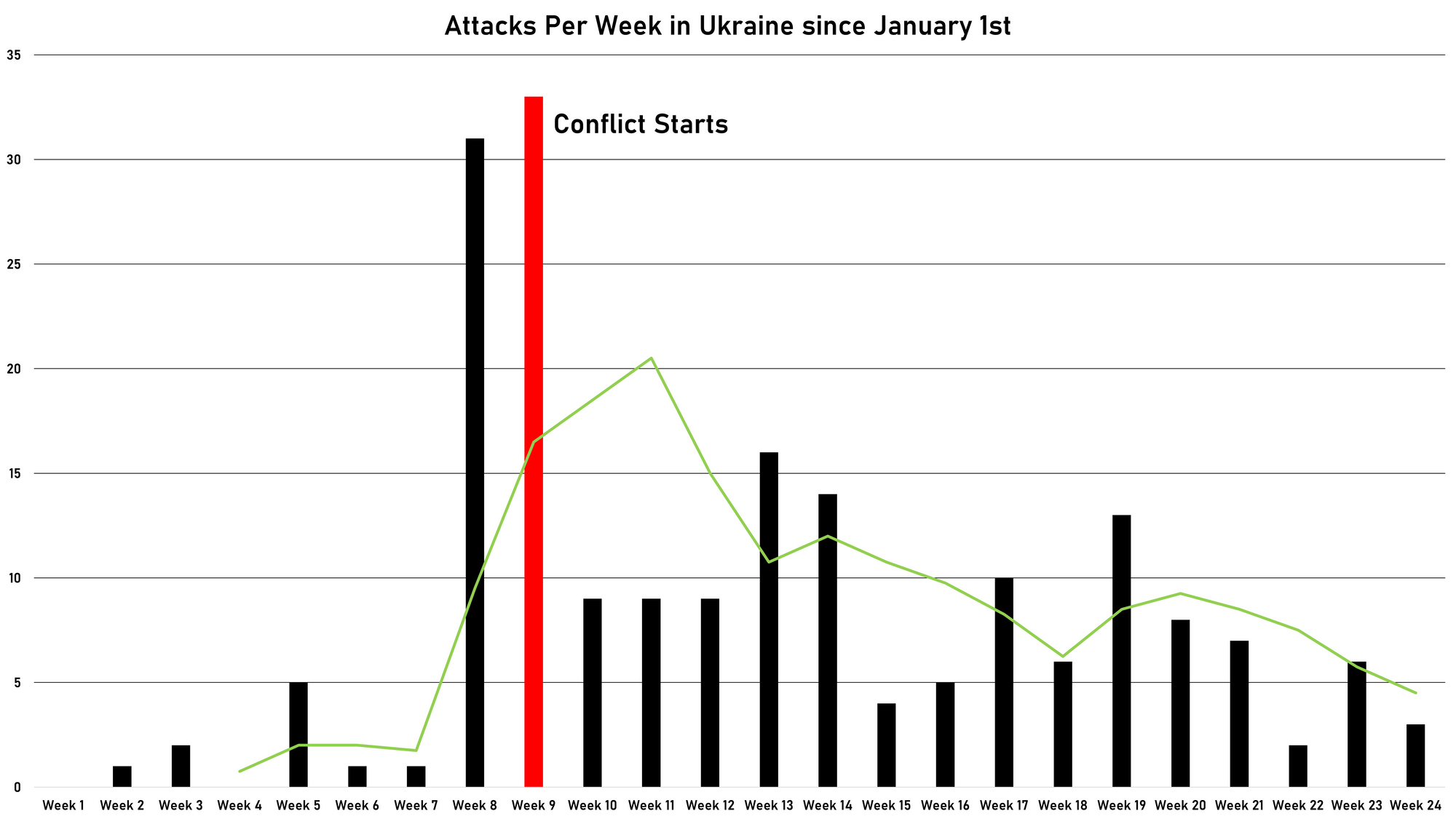
If we graph the number of cyber incidents we have seen in Russia over time and apply a 4-week-moving average to give roughly a monthly trend of attacks, we can also see Russia's preparation for the short sharp war that was anticipated. They had a large number of initial attacks that couldn't be sustained. The attacks didn't go away but they started to trend down and this trend has continued. Given Russia's tendency to pursue options outside of diplomacy, such as cyber, when coercion fails, it's fair to assume that we can see an uptick in Russian cyber operations coming at a point in the future. I'm not alone in thinking this either, the US' number two on Cyber agrees;
A slow military progress continues to thwart the Russians on the ground in Ukraine. They may increasingly consider cyber options to divide our allies and to dilute international resolve against its action,
…
We have not seen that yet, but we’re not out of the woods. We have to keep our shields up, we can’t let our guard down.
Neal Higgins, Deputy National Cyber Director, US Office of the National Cyber Director; Prolonged war may make Russia more cyber aggressive, US official says
The question is when. Ukraine's Major General Kyrylo Budanov has his own opinion, which he doesn't expand on, as being the second part of August;
The turning point will be in the second part of August
Major General Kyrylo Budanov; Chief Directorate of Intelligence of the Ministry of Defence of Ukraine; EXCLUSIVE: Ukraine's Military Intelligence Chief 'optimistic' of Russian defeat 'this year'; 00:00:10
It is also worth noting that we may be seeing preparations for Ukranian action in that time period and Ukraine is using HIMARS to systematically target Russian ammo depots, both in occupied Ukraine and in Russia. Ukraine also has amassed a million soldiers, with the aim of taking back the south of the country. Given the time of year they would be jumping off in, their western equipment and what one would imagine is the influence of western training, it would appear that Ukraine is preparing to retake the south along a Mykolaiv Perekop axis and Zaporizhzhia Novooleksiivka via Melitopol axis. The question is what counts as the South as you could consider Mariupol as the South, even though it has been the Eastern Front of the conflict since 2014, but also Crimea is something Ukraine rightfully considers to be in the south of Ukraine. Mark Galeotti also thinks that this same time period will be on interest too, though for some radically different reasons;
For me, I think it’s September, it’s September when a whole collection of chickens come home to roost. And although I’m not suggesting for a moment that September, things are going to suddenly going to sort of change, nonetheless I think it’s in September that we might see the beginning of the potential for things in Russia to begin to change
Mark Galeotti; In Moscow's Shadows 67: Why September is the Month to Watch, and 'Putin, Ukraine and the Revenge of History'; @ 00:02:25
Though given that Galeotti can talk more openly about his thinking, he does and he greatly expands on his neat little quote stating that September is important because;
- September is the end of Dacha season. Dachas are the summer houses or retreat that some Russians, not only wealthy ones either have, where they have plot of land or collective allotment where they grow some vegetables or have a little land to farm. For example, a friend of mine has a Dacha where his whole extended family go and farms strawberries. With September Russians will be looking at a long and difficult winter.
- The trajectory of the war is trending downwards. And has been doing so for a long period of time and Russia lacks the capacity to continue large scale operations for extended periods of time. Primarily Russia will lack Manpower in the long run and the solution, of course, is mobilization, but this is politically risky for Putin but also the Russian military, due to its structure, would have difficulty training up people to go to war and not immediately die or desert. Not to mention that Russia may not have the functional equipment to equip such a force. Demoralization at home and on the front lines. Russians will see that they are stuck in a war that has no end, no improvement and only high costs.
- September is when Russia will have local and gubernatorial elections. There is talk that they may not happen due to the Special Military Operation. The value in the election is that it keeps Political Technologists, the people who choreograph Russian politics, in business but it also generates economic activity by having these people employed and have them around for the next round of Presidental elections in 2024. Though the Siloviki, or securocrats, wouldn't like the elections to happen because elections can be a proxy for how the general public feel about how things are including debate. This would be unwelcome news. There are also issues with the future of the Liberal Party and Communist Party to stay on message with what the Kremlin will allow.
- Economic Warfare takes time to bite and will be visible. Inflation is rampant, worse than what we are experiencing elsewhere in the world, and this is causing families to burn through their savings. Galeotti expects this to impact most families by then, though it should be noted that in a poll conducted between May 16th and 25th by Alexey Navalny, 49% of Russians are already there. Companies will be in a similar position. The State's budget will be squeezed and while for the moment the Kremlin has cut down on exports to Europe, it is doing so at record prices and boosting the state's coffers at a time when other revenues have collapsed. As people and companies are squeezed, less money is spent, unemployment goes up, inflation continues, and Russia cannot spend its considerable currency reserves in the face of this Economic Warfare. All of this will lead to pressure on the Kremlin.
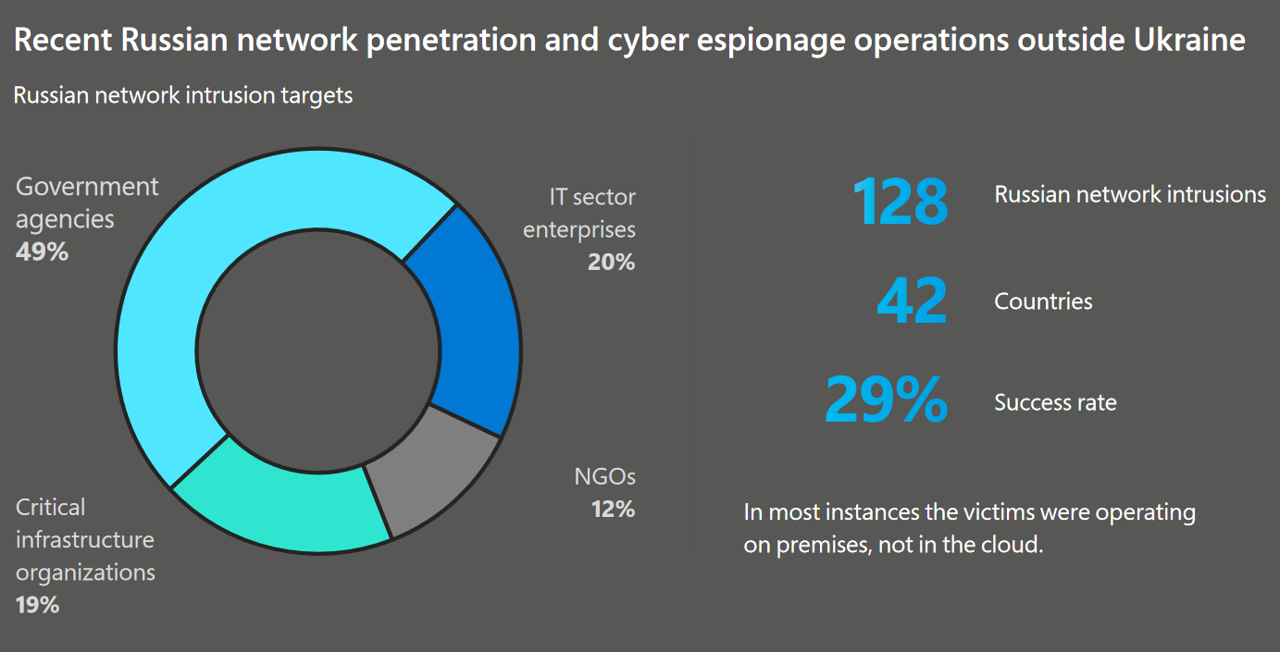
All of this extra pressure will make the Kremlin less able to respond to various things as they arise, which I will come to in just a moment, but it should be noted from a recent report from Microsoft MISTIC that these attacks have already up, and as MISTIC note, they aren't on cloud servers but on-premises servers. While in the report they note they have less visibility into such attacks, they clearly have some signatures or other closed information that they can use to identify such attacks. I do wonder though, how much of this is Russia activating agents inside organisations, as last year I did note that this is a tactic Russian intelligence use and tracking down insider threats is an order of magnitude harder than remote attackers due to the nature of insider threats being trusted.
2. The Importance of Preparation
One thing that is continually preached by all Cyber Security methodologies is the importance of preparation. Ukraine has dealt with a withering barrage of cyber operations since 2014 and has done an incredible job of either defeating the operations or having something go down and restoring service quite quickly. Russia has been the perpetrator of the vast majority of these attacks too. So you would imagine that both sides were equally prepared, particularly in the Cyber Dimension, when the war kicked off again right?
Well not really no. As we have seen, Russia prepared for a particular type of conflict where it would be short, sharp and over quickly, with no contingencies for what would happen if this did not work out for them. As we saw in my graph above, Russia had a sharp rise in Cyber Operations before a gradual decline, to a continuous level. Part of this is because new Cyber Operations take time to create and preposition, but also because it fitted Russia's plans very neatly. This was what they had prepared for.
Preparation is about more than having a plan for what should happen though. Preparation in depth includes having all of the right people, with all of the right training, with a reserve of trained people, who have all done tabletop exercises, wargames etc, ready for when, for example, a cyber incident occurs. This is the difference between having prepared to for management to tick a box and being prepared in depth. It means that your staff have the mental bandwidth to deal with the regular day to day operations you would regularly do and cope with incidents as they arise.
We can see Russia did the box ticking exercise as they lacked the mental bandwidth to quickly pivot to operations they would have in the past. We can see this at Eurovision where Ukraine was clearly going to win and Russia was excluded. Normally when Russia is excluded from such cultural or sporting events, where it can gain political victories along the lines of Russia Stronk, it will lash out with Cyber Operations. We can see this with the World Anti-Doping Agency hack in 2016. Russia's state sponsored doping program was exposed and in response, Russia decided to leak the details of tests and Therapeutic Use Exemptions to the public and allow them to draw their own conclusions about the other countries doping and make it seem as though Russia is doing what everyone else is doing.
They did this again with the OLYMPICDESTROYER malware after they were not allowed to attend the 2018 Winter Olympics in South Korea. The event was a nearly all digital affair where your tickets were on your phone, WiFi was provided via the Olympics app, the host broadcaster had their coverage disrupted and the press centre went offline due to the malware. The organisers of the Olympics did an incredible job of restoring service before it became a major problem that would jeopardize the event and the Darknet Diaries Podcast did an incredible episode talking about not just the recovery but the psychological operations in the malware if you want to know more.
So knowing that Russia has a history of lashing out via cyber means when they are excluded, how come Eurovision didn't look like this;

I mused on twitter that this would have been "chef kiss levels of information operations". To me, this tells us a lot about the depth of capability of those behind Russian Information Operations. They are struggling to maintain operations at home, in Ukraine and against the West more generally, but are also incapable of pivoting to new situations as they arise, as we can see. This isn't to say that these hackers aren't capable, they clearly are, but that there maybe aren't nearly as many of them as we thought, or that they don't have the capability to plan these tasks as they arise or both.
Now, this isn't to say that we didn't see anything at all. A pro-Russian hacktivist group called Killnet, which very few people, if any, I know of had even heard of, took part in DDoS-ing network infrastructure for voting and attempted to disrupt performances.
When you contrast this with Ukraine though, you see an entirely different picture. By the end of 2014, the armed forces, with the exception of a small number of special forces, had failed to do anything about Russia's annexation of Crimea, the uprising in the Donbas and Luhansk regions and the blatant manipulation of presidential elections in 2014. These failures and the successes of Euromaidan and the Revolution of Dignity showed that Ukraine needed to totally reorganize. I don't just mean militarily, but really as a country. Ukraine knew that this was just the beginning and with Russian not achieving its objectives in 2014, a conflict with Russia would come sooner or later.
The Armed Forces began to change how training was done, other states sent missions to train Ukrainian Armed Forces in various weapons and tactics to become incredibly proficient at combating Russian tactics. They developed a Doctrine or set of tactics and strategies, to combat Russian forces when they would eventually come. They began to gut the law enforcement and intelligence agencies of pro-Russian personnel so that the West would supply intelligence and training, without worrying that Russia would learn about the tradecraft used by various intelligence organisations.
They went much future than totally reorganising the county's security though. Ukraine knew that Russia would be likely to target Ukrainian communications infrastructure among other things. Russia would go on to try and knock out power, twice, in Kyiv via cyber means, so they knew they had to be prepared to fix broken infrastructure during a war. This is something they also prepared for, including having telecoms engineers, escorted by troops, and repairing fibre cables earlier this year.
More than this though, regular Ukrainians had played a huge part in alerting regular people like me, in the West to what was going on in Ukraine during Euromaidan and the Revolution of Dignity (❤️Seb). They knew this would be valuable going forward to they knew to have regular people find and amplify pro-Ukranian symbols from across the world, such as this badass babushka on the Moscow Metro, three days into the war, as protestors were being beaten by riot police;
Moscow underground. Sometimes the act of resistance doesn’t have to be loud or bold, it just has to be. #Ukraine #SlavaUkraini pic.twitter.com/MvZc9wscUj
— Belarus Free Theatre (@BFreeTheatre) February 27, 2022
But most of all Ukrainians themselves were individually prepared and were willing to resist. A prime example from the first hours of the war is this video, where a woman in the Kherson region, which had just been captured and may have been a victim of shelling already, confronted armed Russian soldiers. She gave the soldiers sunflower seeds and told the fascist invaders to put them in their pockets so that when they die here in Ukraine, something good will come of their death.
Ukrainian woman confronts Russian soldiers in Henychesk, Kherson region. Asks them why they came to our land and urges to put sunflower seeds in their pockets [so that flowers would grow when they die on the Ukrainian land] pic.twitter.com/ztTx2qK7kB
— UkraineWorld (@ukraine_world) February 24, 2022
This goes so far as that the sentiment of friends I have here in Ireland who are Ukrainians, or half Irish/half Ukrainian, they have the ultimate belief in the victory of Ukraine. Even at Dublin Pride, where we had a Ukrainian Grand Marshal and a section with Ukrainian's front and foremost. As someone who has put the Pride show on for years, I am immensely proud to have helped give our brothers, our sisters and our they/them's from Ukraine, who fight and die for our freedoms, a platform to be recognized. Nothing says this better than the first tweet I saw when the war began. That Ukraine will win.
This is it guys.
— Illia Ponomarenko 🇺🇦 (@IAPonomarenko) February 24, 2022
See you in victorious Ukraine.
3. Cyber is a Management Problem
Organisational and Governance Challenges
While in a lot of ways preparation is a management task, I wanted to make it, its own thing. To me, it really shows the importance of having all of the right people in the right place, who are ready to go, with a culture of being ready for incidents as they arise. And I don't want to say that Cyber isn't a technical problem. It is. But if we look at a lot of the issues that we have, they aren't going to be solved with technical fixes or some magic cyber dust.
Ukraine, between February 24rd and April 8th, was targeted with 237 cyber operations, utilizing 40 distinct pieces of malware according to Microsoft MISTIC (pp 04) and they had an incredible success rate in defeating such operations. The Cyber Peace Institute has documented since 2014, 59 campaigns, using malware, disinformation, dumping of personal information and election interference, that have caused societal harm. Something they view as attacks on infrastructure for civil society such as the water supply or hospitals etc. Ukraine has had a remarkably strong track record of stopping these attacks before they cause damage, mitigating them entirely or restoring services in record time.
Yet when Conti went after the HSE, we learned from the report that the ransomware was comprised 7 days before the malware was triggered, and detected 3 days later (pp 3). Active attempts were made to prevent the malware from spreading and the SecOps team was working on something, I don't know what. Ultimately, it's not the SecOps team's fault as they do incredible work in an organisation where the priority is your health rather than cyber.
For me though, what it highlights is how we treat these issues. In Ukraine, they follow the Estonia Model for Cyber Security. This isn't a formal model, more a way of thinking and addressing cyber. In Estonia, after the Bronze Night incident, Estonia reckoned with what had happened. They created one of the first Cyber Security Strategies, and they gave Cyber a cabinet level position where it was being accounted for at the highest levels of government. Being seen as weak on cyber is something that loses people seats in elections and cyber is a major part of daily reporting in regular news for normal people rather than just people like me.
They have bodies that coordinate policy between various stakeholders, monitor the success of previous plans, implement new ones and update plans as needed. In particular, the goal of the policy coordination is to ensure that Cyber Policy gets as much media attention and funding as is needed to meet its goals. They have an incident management unit, which is tasked with the security of the state's infrastructure and critical infrastructure. They have legislation to do everything from kicking in doors to ensure compliance to extra-judicial fines. There is a lot more to the model, such as how Esontia organized their military, intelligence and emergency management. You can read more about the Estonia Model with this report from the NATO CCDCOE here, but that's all I need to discuss to make my point.
If you contrast that with Ireland, Ireland doesn't have a cabinet level position for Cyber. We have a Minister, whose current title is the Minister for the Environment, Climate and Communications, and even within Communications, cyber is only a small part of this brief. Even if I go and take a peek at the DCCC's Gov.ie page, I can't find a reference to cyber anywhere on the main page and the only way I can even find a reference to cyber is by going into the profile of Ciarán Ó hÓbáin, the Assistant Secretary for Communications and reading their brief. And you know, this isn't me being a tad tired from writing 10k words. Nope, if you search google for "cyber" site:https://www.gov.ie/en/organisation/department-of-the-environment-climate-and-communications/, you get zero results. The body charged with cyber literally doesn't mention cyber.
Here's something fun! If you search for "cyber" on the website of the Department of the Environment, Climate and Communications, you get zero hits on DuckDuckGo or Google
— 🖕Пу́тін хуйло́ 💙💛 Слава і победа Україні 🇺🇦✊ (@LegendaryPatMan) July 12, 2022
The body tasked with Cyber literally doesn't mention the word Cyber on its site... pic.twitter.com/zV9IbLOezc
If you look at how cyber policy is created, effectively what happens is that an EU Directive comes out and we wait until the last minute to do anything about it. Outside of the Public Consultations and going to your TD's surgery, I don't know of any other way for stakeholders to have their views heard, let alone ensure that there is adequate funding and media attention. The same goes for Incident management. I know how to report an incident to NCSC-IE but I have no idea what happens or would happen if I reported an incident, yet in Estonia, I can see entirely what the process is via their website and gain access to all sorts of cool toys too. Just like with the HSE's SecOps team, this isn't the fault of the NCSC, but it's again the same problem as we just aren't thinking about or investing in Cyber. You would think that the HSE hack would change this but... I actually went through the 2022 budget documents in search of more cyber funding, I think it went from 4.5 million to maybe 6 million, which to use a legal term of art, is fuck all.
Poor Investment Choices
This isn't just a problem at a state level though. Cybereason released a survey where they asked IT professionals about what happened after being ransomed. Globally 80% of those that paid the ransom were attacked again and of that 80%, 46% believe they were ransomed by the same gang again. Now, it's one thing to decide to pay criminals, but it's a whole other level of poor management to get ransomed, know there is a problem, do nothing about the problem and allow yourself to be put in a position where you may have to pay a ransom a second time.
This survey came out about a month after another one from Kaspersky, which showed that 9 in 10 organisations who were hit with ransomware before, would just pay if they were hit again. Not just that, these same organisations would rather pay the ransom as early and quickly as possible. This is because the cost in revenue to systems being so high, that it is cheaper to pay the ransom that lose out on said revenue;
This willingness for companies to stump up the cash could be attributed to managers having little awareness of how to respond to such threats, according to Kaspersky. Management may also be unprepared for how long it may take to restore data, with some businesses losing more revenue while their data is being recovered than by just paying the ransom.
Dan Robinson; Most organizations hit by ransomware would pay up if hit again; The Register
Though another way to look at it is rather than sacrifice a tiny proportion of said revenue on an ongoing basis, management would rather ignore the threat until the threat comes for them, then pay off the threat to go away and hope they stay away for extended periods.
And this to me is wild to me because of another recent survey that came out from 1E on how employees feel about all of these IT problems impacting them. 95% of employees found there to be issues in their digital experience and this decreased their productivity and morale. Some of the problems identified as challenges to a better experience are Security and Regulatory policies, IT being overwhelmed, IT's lack of training, technology isn't in place, and there is no management buy-in. Again, the issues aren't all technical. Sure security policies are, but IT being overwhelmed or lacking training or no buy in are all management problems that are solved by... Investing in IT... And that isn't just catching up on your tech debt, it getting on top of it and continuing to invest. Managing your Cyber is better for your bottom line, better for your reputation, better for your employees, and no downtime, because you're on top of your tech, is better for your customers.
Bridging the Gaps in Staffing
And you know, while I'm talking about staff, a friend of mine, Philipa, wrote an amazing article about how we need to break the stereotypes we have of what hackers should look like. I am a very typical looking hacker. I'm a white male with kinda scruffy hair, a budding bald spot, a kinda scraggly beard, I tend to wear printed tees with some sort of message on them, I wear shorts and sandals about 90% of the year, I have way too many hoodies. I dressed down for the day of this talk to make my point;
While Philipa, has a BS in Computer Science, she also majored in Psychology, and AI, but also a postgraduate LLB law degree in Intellectual Property Law, Technology Law, and Constitutional (fundamental) Rights Litigation and a separate Postgraduate Certificate in Education, which you need to be a teacher. She is incredibly accomplished, in multiple fields beyond technology, and she chooses to work in Cyber.
I have a very good friend who I won't name, but she is a director of cyber for a multinational here in Ireland and while she only transitioned into Cyber 7 or so years ago after 20 years in a different career, she is already incredibly accomplished, more than most men who fit the job description of hacker are or ever will be. Her degree wasn't in Cyber or Computer Science when she got it either. Yet she has told me about instances where she feels she is visibly treated differently to men in meetings, and not in a way that respects her status.
Even at this conference, just prior to my talk, Andrea Manning delivered a talk on understanding Cyber Crime. Andrea doesn't have a background in Cyber either. She originally studied Hotel Management and worked in a wide variety of industries before moving into data protection and cyber in 2015 when getting a degree in Business Information Systems. She now runs a company, CyberPie, whose goal is the provide cheap and easy access to cyber for microbusinesses here in Ireland. She is also my go to for cyber crime things because I genuinely don't who else I could go to, to ask about the various cyber threats the cyber criminals pose to Irish businesses.
And these are just the women that I know personally that come to mind as I wrote the talk. Age is also a factor too, as is where we expect hackers to come from. I help put on ZeroDays every year and I have done Lockpicking with Jester for the past 5 years now. This year we had the usual university and industry teams, but also we had school teams with age ranges from 7 and up. A girl from the Ballymun Coder Dojo team came up near the end of the day wanting to try the Lockpicking challenges. While she had never picked a lock before, there was a cryptex, biometric lock and a set of handcuffs.
This little kid obliterated the times of anyone also who even remotely tried these challenges. In the 6 minutes she had to do the challenges, she just asked me to open the biometric lock, she noticed I had a handcuff key on my wrist and asked me if she could use it, and while her mother struggled with the hint for how to open the cryptex, she got it in one. In 90 seconds, she had opened more locks than the vast majority of teams who took 5 mins to do the same, and some of whom I've been teaching lockpicking and physical security bypasses to for years. She had an innate curiosity and drive to just play and understand challenges and this is something you can't teach for all the money in the world.
And I haven't even mentioned, for example, the LGBTQA+ community who at Dublin Pride, Indeed and Tenable had HUGE stands in the Pride Village in Merrion Square, or the countless technology companies that had floats and staff walking in solidarity in the parade. All of these are people who don't look like me, but are in a lot of ways as capable or more capable of cyber than I am, yet I am the go to for Cyber because I look the part.
Overlooking these people is a critical failing in HR and one we need to recognise. These people that I have mentioned prove that not only do we need think more broadly about what we need in cyber, but recognise that not everything we need is Computer Science graduates. Even when we look at larger companies, there are all sorts of basic organisational issues that not just aren't technical, but Computer Science graduates will suck at like governance roles and strategy. For roles where you do need some technical understanding, then it's time to train people to do those roles because very few of the people like me that I studied with for example, are any good at all teaching others and teaching people is essential to preparing your teams to deal with incidents.
Not just that, Cyber people tend to think about Cyber as just computers, to such an extent that if you go and read the National Cyber Security Strategy for Ireland, the word physical is mentioned 4 times and none of those times are in the context of computers existing as physical objects in the real world. We have to recognise that not just do they exist in the real world but that they can have real world examples as factories run on Operational Technology, which is a fancy way of saying computers to manipulate physical processes. What happens if you are able to manipulate a process to blow things up? And that isn't far fetched, we saw it with the German Steel Mill incident in 2014, TRITON/TRISYS and this year with the attack on a Steel Mill in Iran. That kind of outside perspective is something you won't get if you only have cyber people.
Q & A
One of the things I was asked after my talk as part of a Q and A was essential if the Defence Forces had a Cyber Unit, would it be a silver bullet for cyber in Ireland. I am sorry to say that it will not be a silver bullet. It is something we need but you can't just magic away problems in cyber. The guards will be part of the solution as they need to be tackling cybercrime. The National Security Analysis Centre will be important in ensuring we have good intelligence coming from partners and also ensuring that we aren't adopting vulnerable technology.
But really this is a small part of the overall problem which is cultural. I seen a tweet a while ago, that got some traction, which stated that Ireland wouldn't join NATO because the Irish people value Neutrality, because we won't spend the money on the military, because we have a low risk of invasion and because EU, UK and US would step in, if we were invaded. I agree with all of this for the most part BUT for me it misses a key point. Conflict is not bilateral. Countries tend not to agree that they will have a battle at X place at Y time. Conflict can be unilateral and one country can just go to war with another.
Even outside of states, have you ever just been punched by some drunk eejit for no real reason at all? I have. I didn't want a fight, I wasn't trying to start one either. The arsehole just wanted a fight. And it happens today. This is effectively what Russia did in the invasion of Ukraine. Basically, no one wanted the war, not even ordinary, everyday Russians. And yet we got a war because Dear Leader Vladimir Vladimirovich wanted one because he wanted to go from Dear Leader to Vladimir The Great.
In geopolitical terms, this is called Strategic Narcissism, and Ireland has it in bucket fulls. Strategic Narcissism is where you can only view the intentions of others in your own terms. You lack the empathy to see the world through the eyes of another country. I have met people who say that they aren't bothered with cyber because it's expensive and "sure who'd hack me?" Well if Cyber Criminals can figure out a way to monetize hacking you, they will just hack you on the off chance you're worth something valuable.
This kind of divine faith, for lack of a better term, is not sound ground to build any kind of investment strategy on, be it Ireland's military or your government's health service or your company's next big product.
Acknowledgements
Cheers to members of the Irish Cyber Security and Privacy Discord, in particular Philipa, Liam and Owen, for helping me flesh out my thinking on a very small number of the management issues inside Cyber that I covered. And also to Schrodinger for challenging me and in doing so, helping me better display and explain my thinking on what we can learn form the threat intelligence I have available. I look forward to Schrodinger crucifying me after this post.
As usual, none of this would be possible without the wonks of the ACWP Slack! Cheers to Lima for venting with me on management issues, Bill for the continued AAR's which are essential, John for the photoshop of Eurovision, the elusive Horacio for their rad OSINT, and to Toby Tom and Ray for helping me better display the threat intel data because data is not my strong suit.
